DomainTools Reflections on the 2024 Data Breach Investigations Report
Share this entry
tl;dr
Another year has passed and that means another Verizon DBIR, but this time DomainTools was a Contributing Organization! Freaking cool for us since our mission is to make the Internet a safer place and highlighting learnings is one way to help in that mission.
For those that don’t want to read this full blog or the full DBIR, here was our perspective from the Internet intelligence side of cybersecurity:
- Median time for users to fall for phishing emails is 49 seconds
- Pretexting is a more likely social action than Phishing
- Ransomware was a top threat across 92% of industries
- Less representative than last year
- Median ratio of initially requested ransom and company revenue was only 1.34%
- The human element was a component of 68% of breaches
What do these threats all have in common? DNS!
Verizon DBIR Report Analysis and Definitions
First, we want to say thank you to the amazing Verizon Threat Research Advisory Center (VTRAC) that spent the last six months analyzing data to give our community some very valuable insights. Additionally to the:
Verizon DBIR Team
C. David Hylender, Philippe Langlois, Alex Pinto, Suzanne Widup
And, a huge shout out to:
- Christopher Novak
- Dave Kennedy and Erika Gifford
- Kate Kutchko, Marziyeh Khanouki and Yoni Fridman
These folks analyzed 30,458 real-world security incidents and 10,626 confirmed data breaches (a record high!) that happened from November 1, 2022 to October 31, 2023.
Also, before we dive in let’s just do the Websters thing and define some terms:
- BEC (Business Email Compromise): A sophisticated scam targeting both businesses and individuals performing a transfer of funds. (Internet Crimes Complaint Center)
- Ransomware: A type of malware that holds a victim’s data or device hostage, threatening to keep it locked—or worse—unless the victim pays a ransom to the attacker. (IBM Security X-Force Threat Intelligence)
- Phishing: A type of online scam that targets consumers by sending them an e-mail that appears to be from a well-known source. (Federal Trade Commission)
- Social Engineering: All techniques aimed at talking a target into revealing specific information or performing a specific action for illegitimate reasons. (European Union Agency for Cybersecurity)
- Pretexting: A tactic that hinges on telling a compelling—but fake—story. (Financial Industry Regulatory Authority)
- Artificial Intelligence: A branch of computer science focused on helping computers learn on their own, adjust to new inputs, and perform tasks – all without human intervention. (DomainTools)
Well, that Scrabble board would be fun – let’s jump in!
Takeaways from the DBIR
BEC
According to the FBI IC3 dataset, incidents involving Pretexting (the majority of which had BEC as the outcome) accounted for 1/4 of financially motivated attacks with the median transaction amount of a BEC being around $50k.
One other thing worth noting is the clear overtaking of Pretexting as a more likely social action than Phishing. If you have been watching the DBIR rise of BEC attacks – it clearly notes this as a scalable way to address threat actor monetization.
Ransomware
No surprise here that Ransomware was a top threat across 92% of industries, but the surprise was that compared to last year’s DBIR, it was less representative.
Over the past three years, the combination of Ransomware and other Extortion breaches accounted for almost 2/3 of attacks and according to the FBI’s IC3 ransomware complaint data, the median loss associated with the combination of Ransomware and other Extortion breaches has been $46k for 95% of the cases. With a median ratio of initially requested ransom and company revenue of 1.34%.
Phishing
The overall reporting rate of Phishing has been growing over the past few years, which is not alarming, especially with the rise of AI. While at a mass scale, we implement security awareness trainings, the behaviors of individuals are very infrequently changed – the median time to click on a malicious link after the email is opened is 21 seconds, and an additional 28 seconds for data to be shared. All this means is that the median time for users to fall for phishing emails is less than 49 seconds.
We are already seeing the proliferation of AI within Phishing to make attacks more powerful than ever with the introduction of CrewAI and other applications. Essentially, removing the recon phase for threat actors, makes the barrier to entry/phishing so incredibly easy.
What Do all the Above Have in Common? DNS
According to the National Security Agency, 92% of malware and C2 activity can be managed at the DNS layer. The threats and trends described in the DBIR Report and in BEC, ransomware, and phishing all suggest that adversaries rely on internet infrastructure (such as phishing or BEC domains mimicking a victim organization) that often remains unchanged and can leave clues behind to better support defense against and investigations into those behind these mentioned threats.
A Call for Strengthening Supply-Chain Awareness and Management
Page 13 and 14 of the report pull no punches in calling out the supply chain interconnection in breaches over time and the threat exploiting the weakest link within a supply chain brings to an organization. So much so, that this year Verizon has introduced tracking this as a new metric for this and all future reports that they publish. Verizon represents the metric, which shows an increase in the varieties of supply chain interconnection breaches, as “a failure of community resilience and recognition of how organizations depend on each other.”
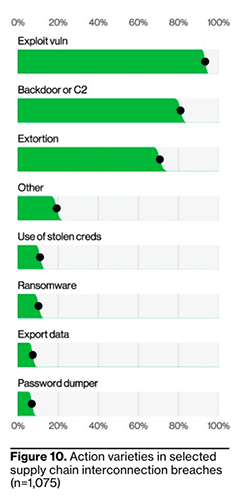
Page 13 and 14 of the DBIR highlight the need for a rigorous security assessment and audit of any software in one’s organization, or associated supply chain. Steps in these audits should include profiling vendors with security in mind before agreeing to trust them with their data. This would also include regularly monitoring vendors with the monitors one has in place with their organization. From a DNS perspective, these steps look like determining organizations with the most sensitive relationships, adding their names to the monitors for spoof domains, and checking your DNS, web proxy, SMTP, and other relevant logs for evidence of any traffic from your environment to these domains.
CISA Known Exploited Vulnerability (KEV) Catalog
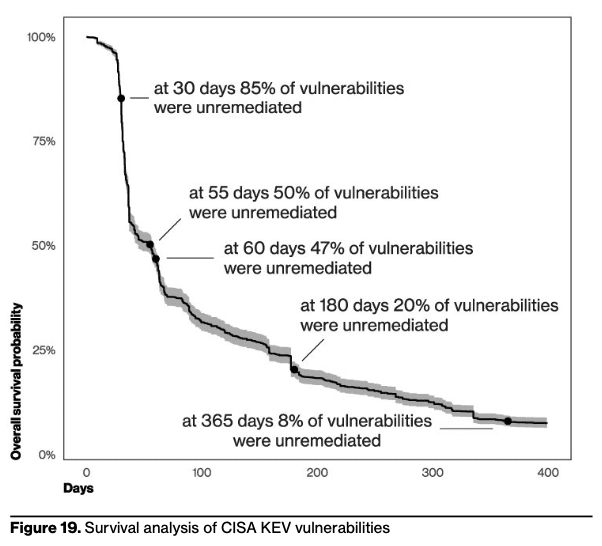
One area that was great this year in the DBIR was the inclusion of CISA KEV, the survival analysis of vulnerability management data, and the cross correlation of the KEV; which highlighted that it took 55 days to remediate only 50% of the vulnerabilities when the patches were made available. While widely accepted that a 15 day clock for patch management of critical vulns is satisfactory, the report notes that it is not keeping pace with the growing speed of threat actor scanning and exploitation of vulns.
The Human Factor(s)
Another area the DBIR excels in is going beyond the technical to highlight consistent but complex human factors around breaches as well. Last year’s rise and this year’s prevalence of Pretexting (as it relates to BEC) drives this point home from a Blue Team perspective. Email threat detection products can easily monitor for content known to be used in ongoing campaigns, but Pretexting handily defeats that by reusing already-existent business communications with the target. The field of cognitive linguistics tells us that the reuse of familiar communications and settings means that the end-user will encounter the message in a similar cognitive frame to the original interaction, which unfortunately means their risk perception and security awareness falls off precipitously. It may be harder to convince a target to click a malicious link with a random email, but if it’s coming from the distributor sales engineer tagged onto an email thread about your shared love of dogs that likelihood may shoot upward.
“For this year’s dataset, the human element was a component of 68% of breaches, roughly the same as the previous period described in the 2023 DBIR” the Summary of Findings tells us – providing the massive scope of just one problem involved in protecting an enterprise. Analysis in Figure 8 provides context for human element enumeration recently peaking in 2021, declining until 2023, and slowly increasing again.
A broader contributor base allowed the DBIR to add a new category – Errors – and find that it contributed to 28% of breaches. Internal threat actors rose to 35% from 20% just a year previous in part due to this – 73% of those internal actor breaches came from the Miscellaneous Errors pattern, a rising trend due perhaps less to increased threats than increased visibility. The DBIR also noted that the “End-user” threat actor category more than doubled to 26% versus, say, Organized Crime or State-Sponsored threat actors – again related to Misdelivery and Miscellaneous Errors leading to breaches.
The VERIS asset category “Person” as a focus of attacks saw substantial growth from the previous year as well.
This is all to say that, as always, human factors are key to breaches – and their prevention – as well. What the people in your workflow see, how they process, how they decide, whether they are employees, partners, customers, or other groups, is an essential part of any organization’s security successes or failures despite only being able to control so much. For the SOC team, this underscores the importance of actions like preemptive domain monitoring and brand protection as well as passive historical DNS, both in the ability to mitigate active threats and the visibility to see infrastructure come online and presage how malicious actors will attack next.
There are plenty more great nuggets of information in this year’s DBIR and we were excited to be noted as a Contributing Organization to this year’s report!







