Seeing Red

Executive Summary
The DomainTools Research team came across a batch of malicious-looking PDFs that stretched back to July 30, 2021. While containing no malicious content, they did link to dozens of short-lived Glitch apps hosting a SharePoint phishing page containing obfuscated JavaScript designed to harvest credentials. The targets of the spearphishing campaign are employees at major corporations with what appear to be an emphasis on employees operating in the Middle East. Upon further pivoting this looks to be just a single campaign in a long line of similar, SharePoint themed phishing attempts.
Discovery of Spearphishing Infrastructure
Through the course of regular monitoring and hunting for malicious documents tied to previous campaigns, DomainTools Research had a false positive appear in the form of a PDF document purporting to be an invoice. While this PDF document contained no actual malicious content, the PDF did contain a /URI section which linked to an outside page. This would normally be uninteresting except that an email address was appended to the URL as a fragment. Fragments in URLs are the part after an octothorpe and typically reference an ‘id’ element on an HTML page, but that can be manipulated using CSS.
What made this intriguing was that the email address belonged to a legitimate employee at a corporation based in the United Arab Emirates. Since this would be indicative of spearphishing, DomainTools Research decided to hunt for similar documents and found nearly 70 dating back to July 30, 2021, all with email addresses of actual individuals working at large corporations. Each document contained a different URL and email address of the target individual making each unique. Though each URL and email was one of a kind, the documents themselves did link to the same named page each time: red.htm. Thus, the title of this document, “Seeing Red”.
How Glitch Serves Up Malicious Content
Despite the different URLs, they were all brought together by utilizing Glitch for hosting. Glitch— the company behind Stack Exchange, Trello, and other software development tooling— provides a web-based tool with a built-in code editor that can run and host software projects from simple websites to large applications. The free version of their product allows for an app to operate for five minutes exposed to the global Internet with a Glitch-provided hostname using three random words. For example one document directed the recipient to hammerhead-resilient-birch.glitch[.]me where the malicious content was stored. Once the five minutes is up, the account behind the page has to click to serve their page again. This ephemeral nature makes Glitch shared spaces perfect for serving up malicious content, especially because Glitch’s domains are trusted and often allowlisted on many networks already. DomainTools Research reached out to Glitch about this, but have yet to hear back as of the publishing time of this document.
Hunting for Live Examples of a Malicious Payload
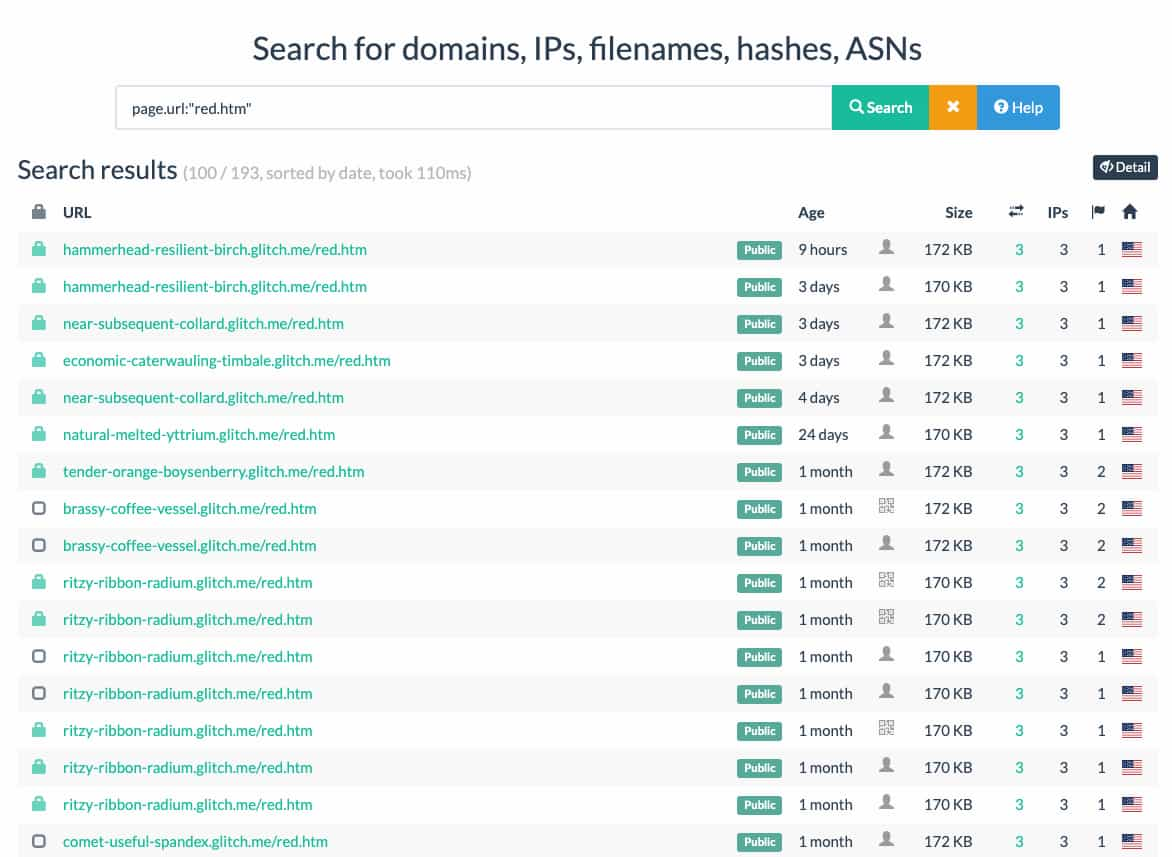
Due to how ephemeral these pages were, of the 70 documents that DomainTools Research uncovered none of them contained a live page serving up a next stage payload. Luckily, a number of tools exist that help to hunt in this case. The first was URLScan, where one can search through all of the scanned sites over the last month. While there were dozens of other URLs which led to new documents, this unfortunately just showed that many others were coming across the same issue of deactivated pages.
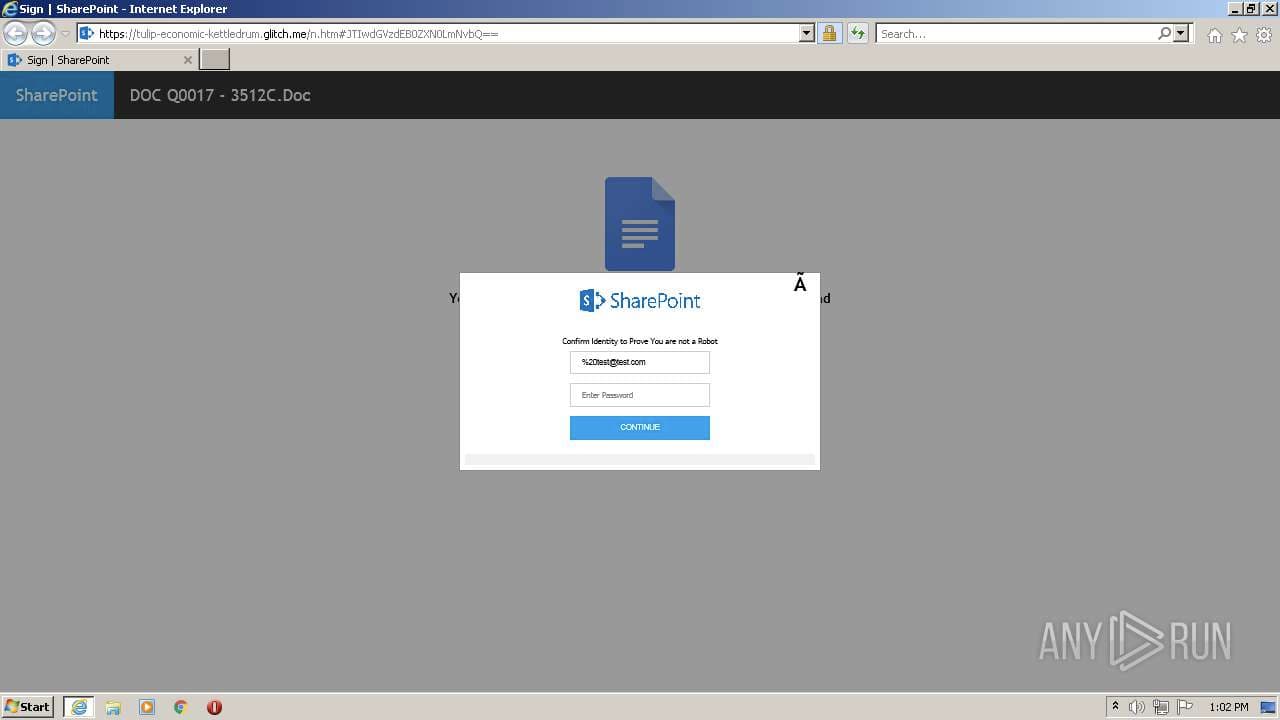
While scouring other OSINT sources, DomainTools Research eventually came across a live site on the Any.Run service, a commercial malware sandbox and public repository of executed malware that can be used for hunting on specific interactions from malicious code. While the report did not contain the next stage payload, it did contain a screenshot of the Microsoft SharePoint phishing login being used to lure the victim.
While the page content was not available, DomainTools Research did take note of the document name as well as the redirect to “in.htm” as the next page after the “red.htm” page in the initial PDF document. Searching for this document name on VirusTotal, DomainTools Research was able to locate a number of matching HTML documents that tied to previous PDFs due to the email addresses pre-populated on the page, the initial PDF documents designed to pass the email of the target along as a URL fragment mentioned prior.
Obfuscated JavaScript
Pulling these pages, DomainTools Research found chunks of obfuscated JavaScript as shown below. Once deobfuscated this revealed the email address and password being submitted to compromised WordPress sites and forwarded to an email address found in the body of the script of uzohifeanyi@outlook[.]com. Once the credentials have been harvested, the JavaScript then redirects the user to the URL of their email address.
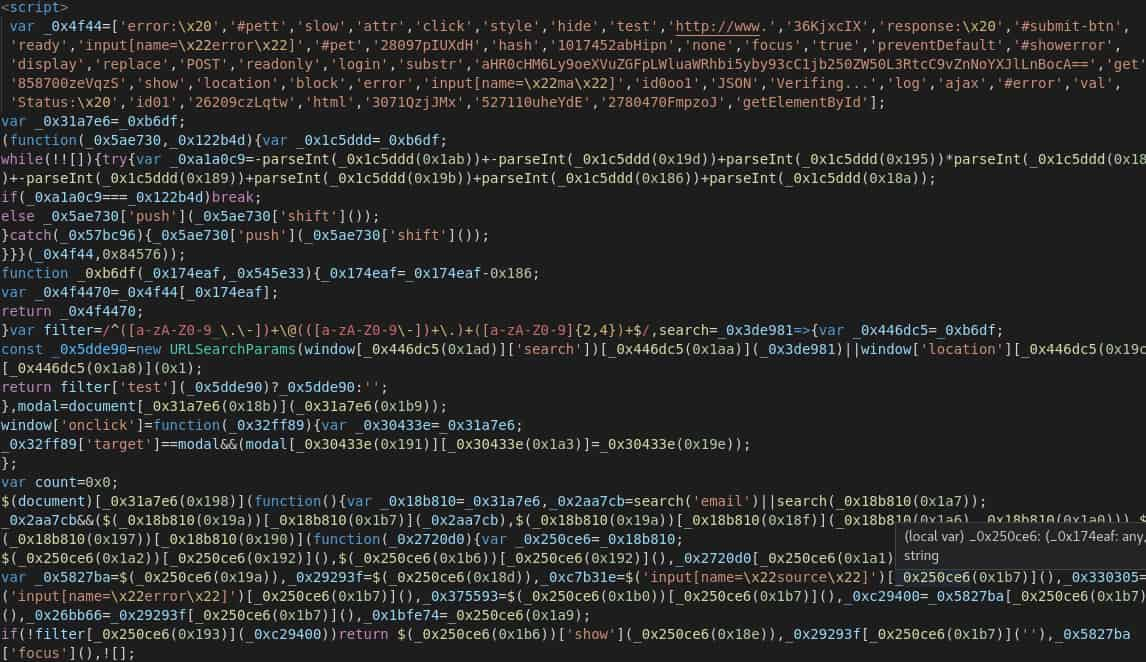
Pivoting off of the Outlook email address receiving the credentials, a host of other documents dating back to September 2021 were available under a wide range of names and hosted on additional sites providing hosting as a service similar to Glitch’s such as Heroku or through CDNs such as SelCDN.
Conclusion
Further analysis concluded that no document was ever delivered or at least that DomainTools Research could not get the sites to deliver one, making this seemingly a credential harvesting spear phishing campaign aimed at large companies with dealings in the Middle East based upon the targets found in documents.
Spaces where code can run and be hosted for free are a gold mine for attackers, especially considering many of the base domains are implicitly trusted by the blocklists corporations ingest. This delegation of trust allows for attackers to utilize a seemingly innocuous PDF with only a link to a trusted base domain to maneuver past defenses and lure in user trust. By coupling that with exfiltrating captured credentials to compromised WordPress sites, attackers have built an attack chain that can sneak past defensive tooling.
These iterations are just one of the many ways that phishers are continuing to evolve their phish kits and find ways to creatively run code that will not be caught by today’s modern EDRs and reliance on blocklists.


