SolarWinds Aftermath Threat Hunting Survey Yields Mixed News

Introduction
Given the reach of the SolarWinds incursion and its sequelae, it’s safe to assume that there are going to be changes in certain SOC practices in the coming months and years. While the concept of supply chain breaches is far from new (as any major infosec conference attendee can confirm), this series of unfortunate events has brought supply chain integrity and security to a top-of-mind position, at least for now. Interested in learning more about how the breach might be affecting attitudes and behaviors, DomainTools fielded a survey of infosec practitioners to find out more about how this incident has affected them, and how their plans going forward may be evolving.
Whom We Surveyed, and What We Asked
The survey’s roughly 200 respondents were a mix of front-line practitioners, managers, and C-Suite executives, representing companies of all sizes, though a strong majority work in large to very large enterprises. Safe to say, then, that this is a population that has a good read on what’s going on in the SOC. Our questions fell into five very general categories:
- Whether, or to what extent, the respondent’s own organization was affected by the SolarWinds-related breach
- The role of threat hunting, present and future, at these organizations
- The role of attribution in response or hunting activities
- The role of DNS-based data and analytics in response or hunting activities
- How consumer/vendor relationships might change going forward
Impact on Respondent Organizations
About 19% of our respondents said that their own organizations were directly affected, while about 65% said they were unaffected. The remainder weren’t sure. As for the import of the news, a little over 60% reported being highly concerned, almost exactly a third were slightly concerned, and a few insouciant souls were not concerned at all. A little under 40% of the respondents said that the incident directly impacted their jobs, with incident response (IR), research, and reporting being the primary areas of focus.

We also asked about visibility—specifically, “As a result of the SolarWinds hack, how confident are you in your visibility into security information or into internal processes?” In answer, a proud 21% stated they are very confident, around 51% declared themselves fairly confident, just over 20% slightly confident, and 7% not at all confident. In the SOC, visibility is, if not everything, then it’s darn near, so that 7%, and the 20% of “slight confidence” is concerning.
The Role of Threat Hunting
As a baseline, about 62% of respondents have a threat hunting team. But that number might be different in a few months or years: about a third of respondents said that they intend to raise the priority of staffing a threat hunt team as a result of SolarWinds. That does leave the obvious point that, for a pretty strong majority, this event doesn’t materially change their threat hunting staffing.
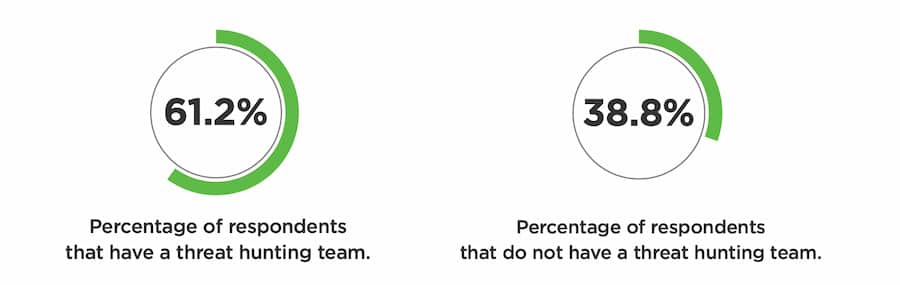
For those who do have a hunt team, more than half (around 55%) stated that they will incorporate new hunting techniques for supply chain attacks (See a recent DomainTools webinar on this exact topic for more information). And some of the respondents who have threat hunt teams report that these teams will get increased resources following the SolarWinds incident.
The Role of DNS Data
No one reading this should be surprised that a company that focuses on DNS-based intel and data is going to ask about those things in a survey. We don’t pretend to be unbiased in this respect. The respondents put it this way: a little over a third (~36%) rely heavily on DNS-based data, while around 56% rely somewhat on it, and a little over 10% don’t use it much. For the teams in the “somewhat” category, it may be a reasonable assumption that many SOC workflows don’t have anything to do with Internet-based observables. Hunting for signs of lateral movement, or building YARA rules to detect rogue binaries, to name just a couple of examples, don’t need DNS data. When it comes to analyzing and gaining context on traffic outbound from the protected environment to malicious or suspicious infrastructure, of course, the picture is very different, and indeed, almost 90% stated that for looking specifically at the SolarWinds actors, DNS data is “fairly” to “very” important. For more detail on how DNS-based data and intelligence can inform SOC functions, see recent blogs by Joe Slowik and yours truly.
Attribution: Does It Matter for Blue Teamers?
In any attention-grabbing cyber incident, one of the first questions addressed, especially at a mass-media level, is “who did it?” And, in high-profile events, there is rarely any shortage of speculation about whom to hold responsible. And it’s a natural human curiosity to wonder about this. However, we assert that while it’s understandable to be curious about the origin of an attack or incursion, blue teamers usually shouldn’t spend much time or effort on attribution. For one thing, it can be incredibly hard to get right, even for the best-resourced outfits (such as state-level counterespionage or law enforcement); for another, it is typically very time consuming and labor intensive—and that is assuming you even have access to enough of the right kind of high-confidence data to make a viable attempt.
Our respondents did indicate that attribution matters to them, though. Around 44% said they put high emphasis on defending against state-sponsored attacks, with another 37% giving it a moderate emphasis. Only a little under 20% put this emphasis level at “low.” The biggest (61%) reason they cited for why this matters is that it guides what kind of tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to look for. Next, at around 46%, was that state-sponsor attribution helps get more resource allocation. Almost 40% said that attribution is a requirement for their reporting on an incident.
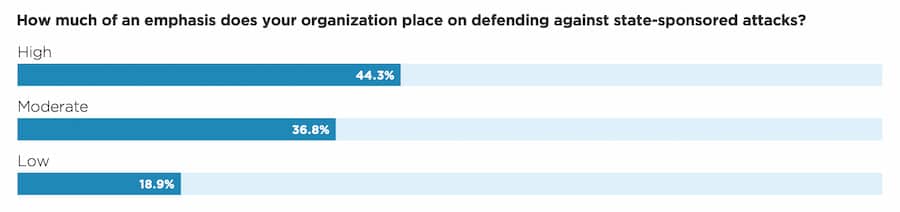
That last point puts teams in an interesting position, if the expectation is that they do the attribution themselves. If citing highly qualified external sources, then this poses less of a challenge, but again, even the best of the best are not always able to give high-confidence attribution.
Vendor Relationships
Any supply chain incident raises questions about how to secure an ecosystem that involves external software or *aaS services. Our respondents made a relatively strong statement about this in their response to the question “How will the SolarWinds hack change your approach to how you manage vendors/supply chain security and risk in the future?” Almost three-quarters cited changes they would be making, including holding vendors to the organization’s own security standards, including legal attestation (47%), increasing network segmentation to isolate vendor software and hardware (39%), implementing static and dynamic application security testing (S/DAST) (24%), cutting ties to vendors associated with adversarial nations (19%), and reducing overall reliance on vendors (17%).
These changes are understandable. They’re also a large undertaking, and it’s likely that at least some of the plans stated in our survey may get shelved. There are very few companies that can eliminate their reliance on third-party systems, and for those who do not, the other measures will represent at best a lot of work (changing network topology, running S/DAST) and at worst, may be impossible (getting legal attestation from vendors about meeting standards imposed by the customer). However, it is perfectly appropriate and healthy for organizations to be exploring these options.
What Does It All Mean?
Coming back to the theme of threat hunting and what this event means for it, we are pleased to see that over half of the respondents in the survey already have hunt teams. For many organizations, this is a nascent capability, or something that DFIR folks do when they have time—which, for many teams, rounds to near zero. We were also glad to see that almost two thirds of the organizations were not directly affected by the SolarWinds incident. With all the news about how widespread it is, it’s good to keep in mind that a lot of folks have been able to keep their focus on other threats and remediations. We definitely encourage the use of DNS data, of course, and invite any SOC folks who haven’t spent much time using such data to attend one of our webinars, such as the informal “Indicators over Cocktails,” to learn more about the role it can play in building strong detections and defenses.
Stay safe out there!



