Spoofing Banks is a Balancing Act
On November 12, 2019, DomainTools PhishEye picked up 291 domains that were spoofing the key term, “natwest”. From this data set, we saw that the Proximity (evaluates the likelihood a domain may be part of an attack campaign by analyzing how closely connected it is to other known-bad domains) scores were pretty high for the first screen’s worth of domains (60+). From that indication, I thought it would be valuable to take a deeper look at the connected infrastructure behind the domains individually. I exported all 291 domains into a new investigation investigation in our purpose-built tool, Iris Investigate.
Within Iris Investigate, we were able to find the following:
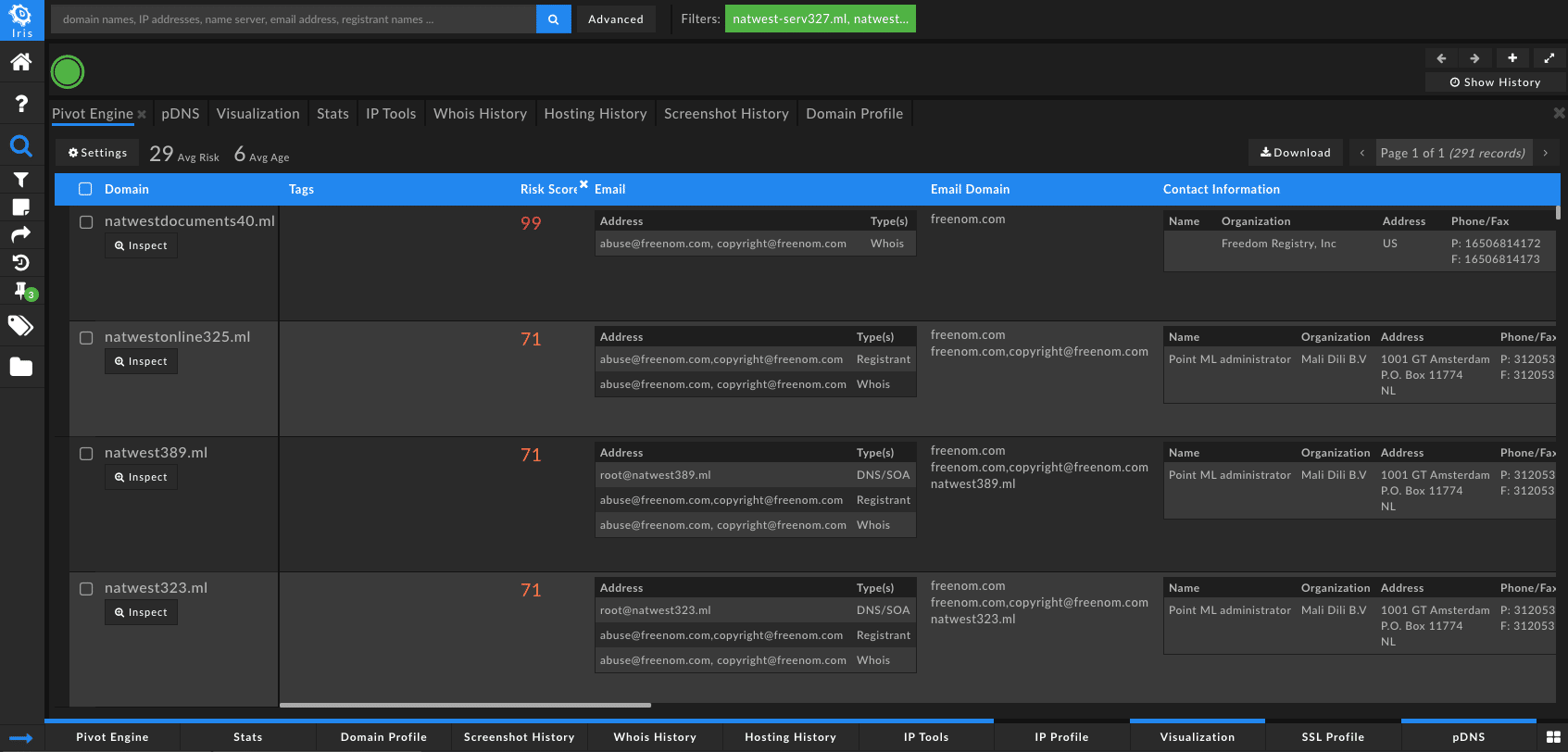
Filtering by Domain Risk Score – The score comes from two distinct algorithms: Proximity and Threat Profile. Proximity evaluates the likelihood a domain may be part of an attack campaign by analyzing how closely connected it is to other known-bad domains. Threat Profile leverages machine learning to model how closely the domain’s intrinsic properties resemble those of others used for spam, phishing, or malware. The strongest signal from either of those algorithms becomes the overall Domain Risk Score.
While trying to quickly look for connected infrastructure, my first piece was to look for any Guided Pivots, an indication of potential pivot points that are likely to be useful and related to the investigation of the dropper domain.
While scrolling down, I located the domain, natwestonline87[.]ml with a Domain Risk Score of 68. Generally, I will take a look at any domain with a Domain Risk Score of 50+ if there are also Guided Pivots. Although, this is just from a Research perspective and not from a SOC/CSIRT perspective.
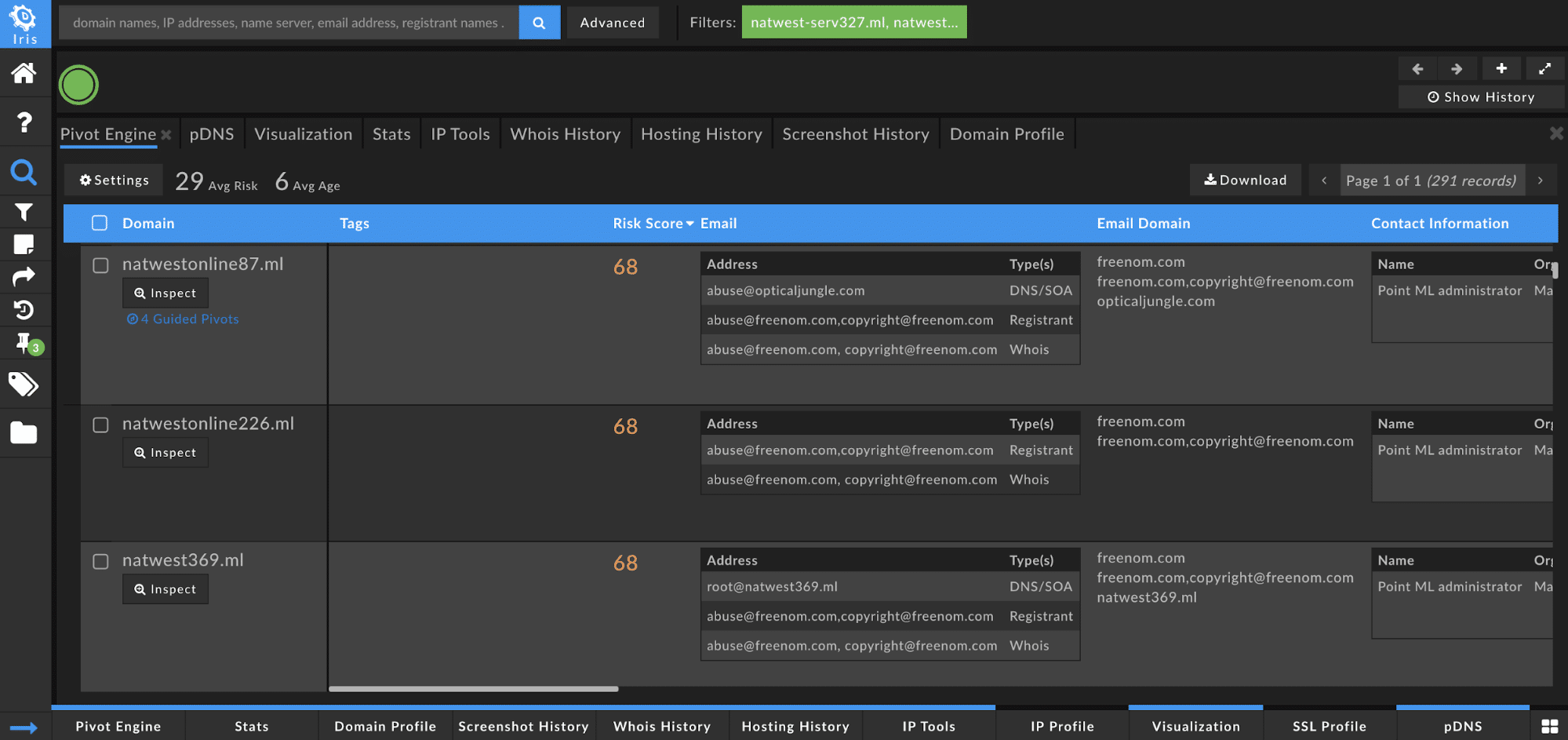
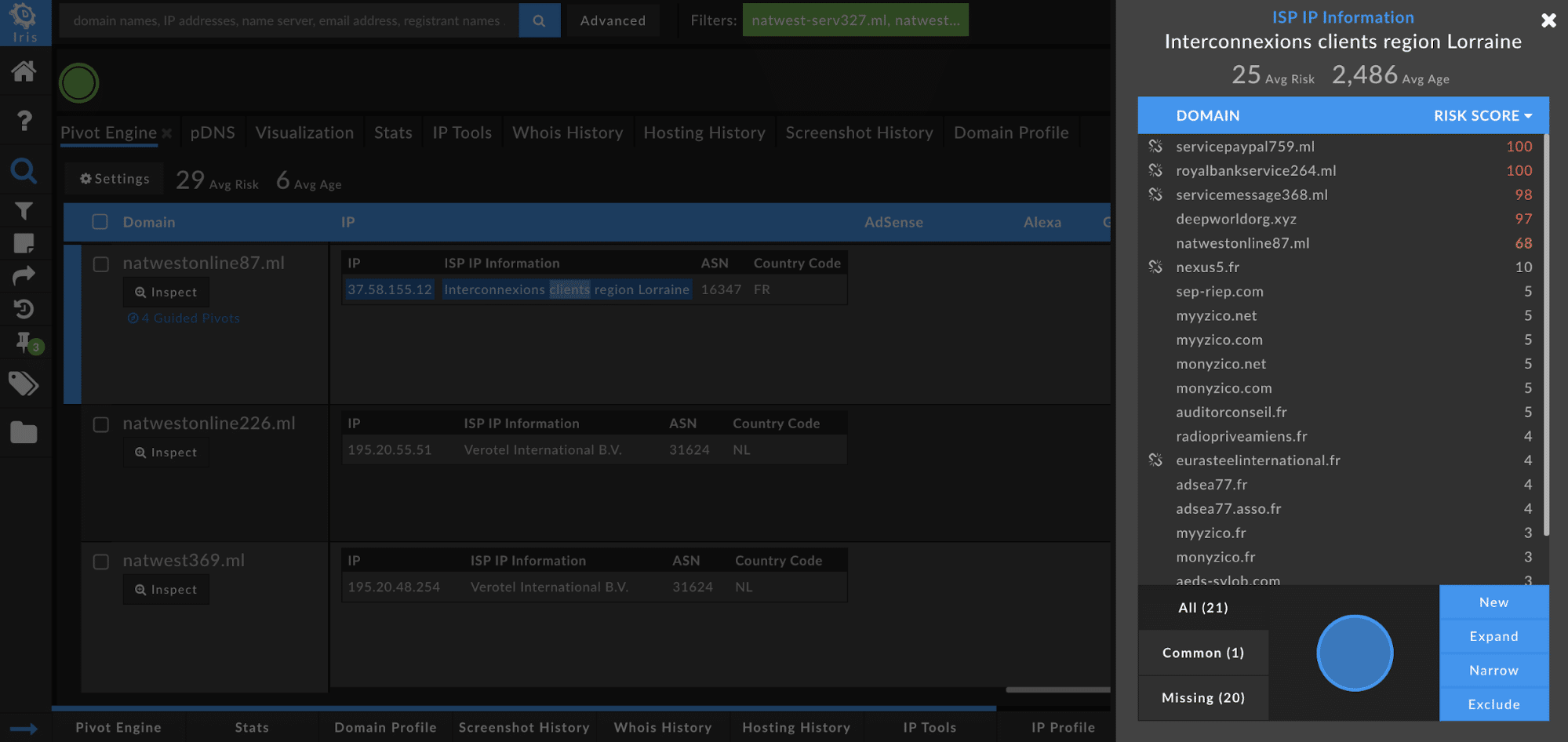
The 4 Guided Pivots for natwestonline87[.]ml are:
- IP: 37.58.155.12
- 4 domains share this value, with an average Domain Risk Score of 91
- From these four domains you can see that they are also spoofed PayPal and the Royal Bank.
- 4 domains share this value, with an average Domain Risk Score of 91
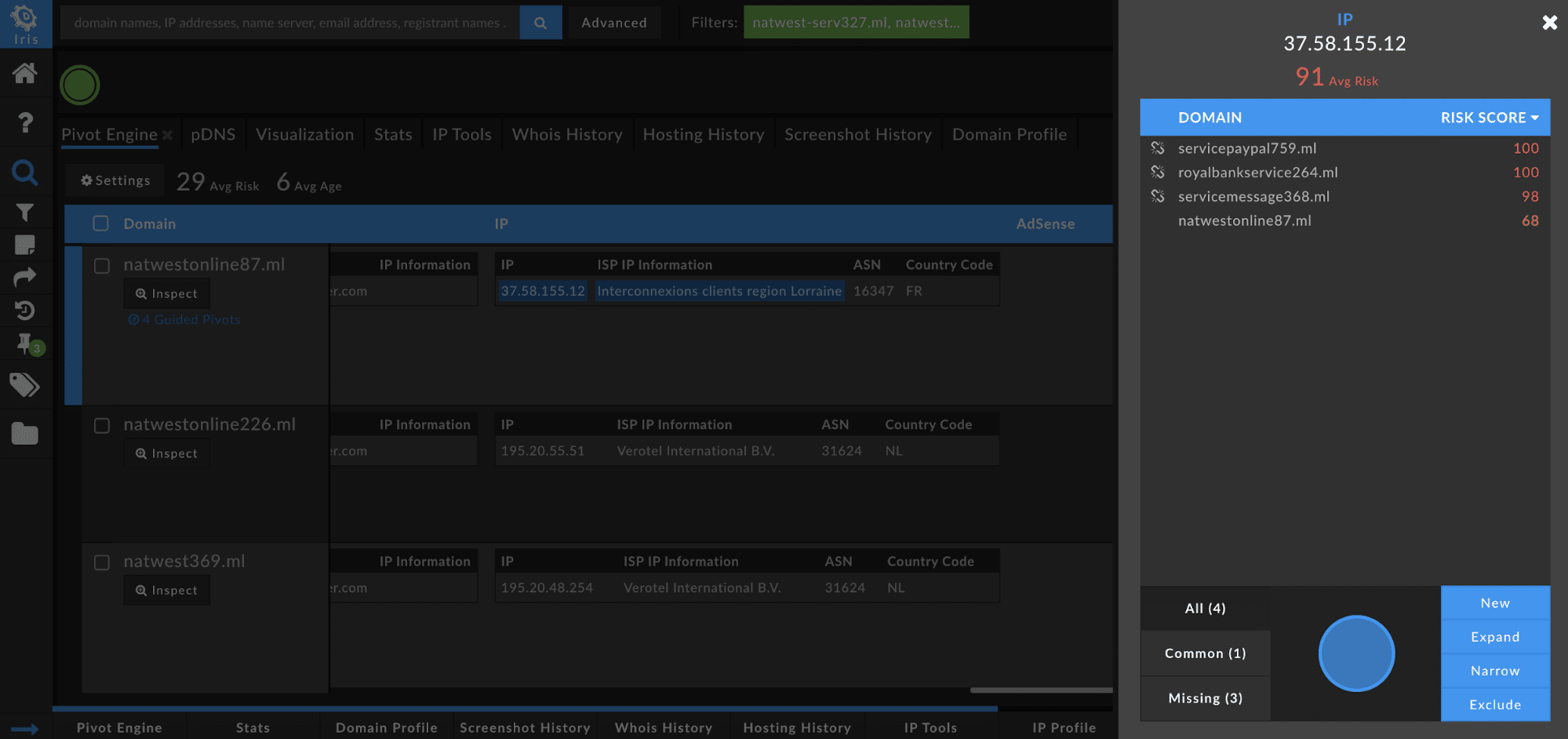
- ISP IP Information: Interconnexions clients region Lorraine
- 21 domains share this value, with an average Domain Risk Score of 25 and average age of 2,486
- Generally, if the Domain Risk Score is this low for the set of associated domains, and the average age is this high, I will not encompass these results into my investigation.
- 21 domains share this value, with an average Domain Risk Score of 25 and average age of 2,486
- SSL Hash: 3cbc9c587866f18551fa72bcd4e0a4853ac8d5c2
- SSL Subject: CN-jeumont.fr
From the original set of 291 domains, I decided to focus in on natwestonline87[.]ml so I selected all of the domains then filtered to exclude all but natwestonline87[.]ml.
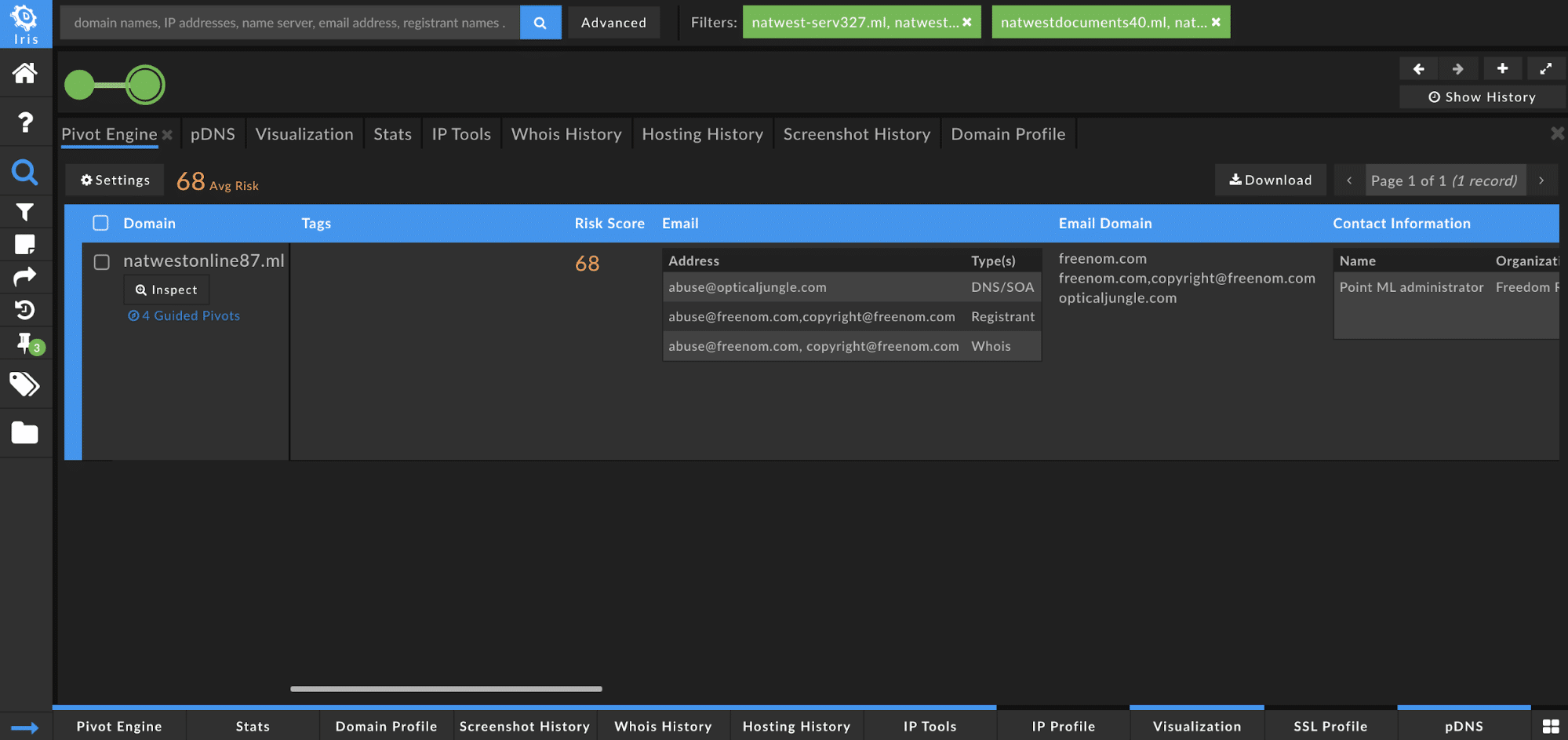
Then, I decided to include to expand my investigation on the IP, rolling in the following domains:
- servicepaypal759[.]ml
- royalbankservice264[.]ml
- servicemessage368[.]ml
To this investigation, I also want to add a Tag so that when I share this with fellow researchers, or these results show up in Splunk, Splunk Phantom or IBM Resilient they will be able to see the tag and know that there is qualifying evidence. I like to tag domains with qualifying evidence, but this should be decided on by your cross-functional teams (IT, Security, etc.).
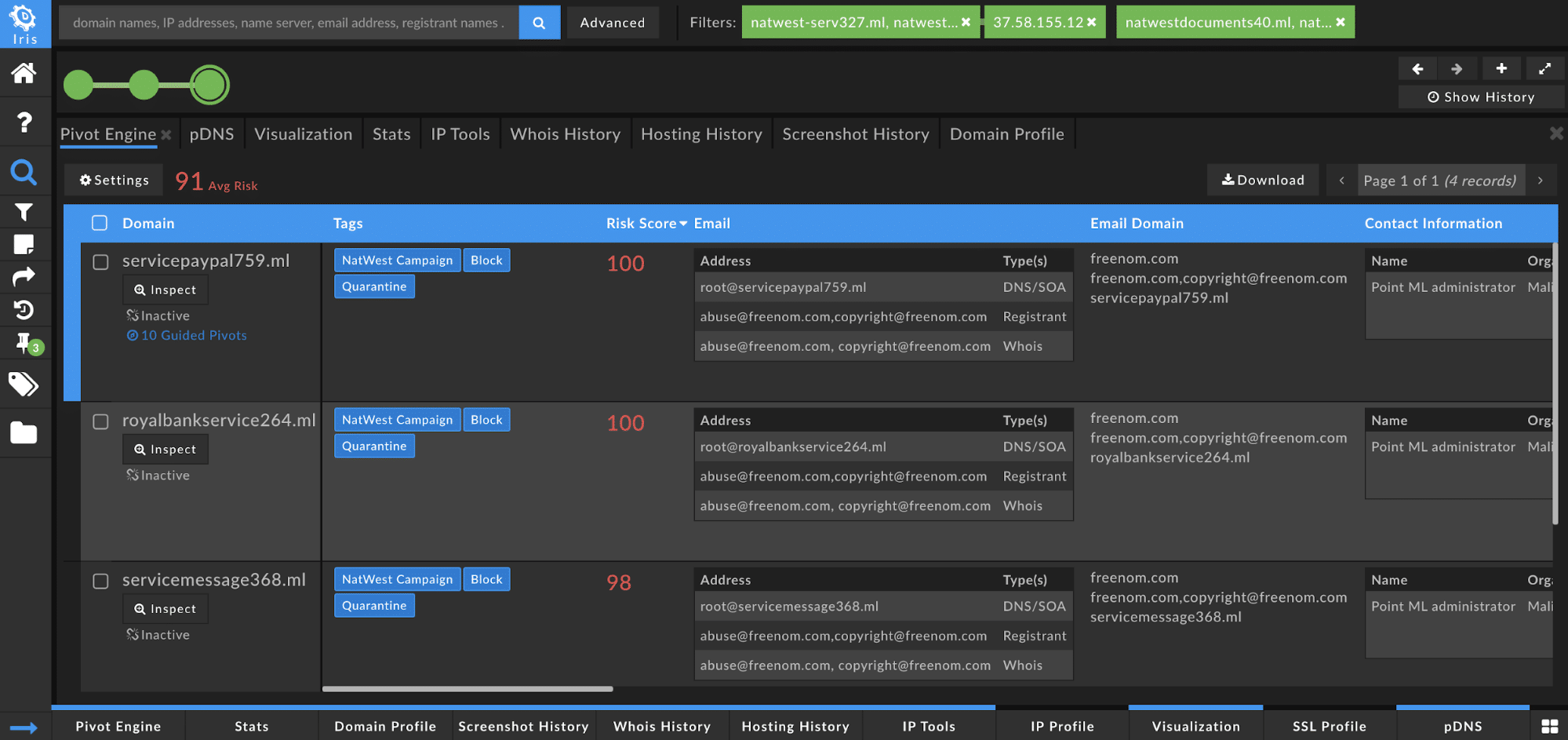
From servicepaypal759[.]ml, there are 10 Guided Pivots, and although the domain is marked as Inactive, I still want to look at the connected infrastructure behind the domain to see if I can uncover any active domains that are still part of the campaign. I also want to start to look for the duration of the campaign and more qualifying data.
- Name Server Hostname:
- ns1.invoicefax[.]com
- 443 domains share this value – average risk 99
- All inactive domains
- X domains that are not on an industry blocklist (100)
- 443 domains share this value – average risk 99
- ns1.invoicefax[.]com
- ns2.invoicefax[.]com
- Same for ns1
- Name Server IP Information:
- 193.151.15.19
- 442 domains share this value – average risk 99
- 37.1.204.190
- 442 domains share this value – average risk 99
- 185.25.50.251
- 119 domains share this value – average risk 99 (all spoofed PayPal domains)
- 185.25.50.252
- 119 domains share this value – average risk 99 (all spoofed PayPal domains)
- 5.45.87.115
- 442 domains share this value – average risk 99
- 193.151.15.19
- ISP IP Information:
- Interconnexions clients region Lorraine
- 21 domains share this value – average risk of 25
- Interconnexions clients region Lorraine
- SSL Hash: 3cbc9c587866f18551fa72bcd4e0a4853ac8d5c2
- 4 domains share this value – average risk of 91
- SSL Subject: CN=jeumont.fr
- 5 domains share this value – average risk of 73
11/14/19
natwestonline87[.]ml moved from a Domain Risk Score of 68 to 69 and it looks from the screenshotter, that the page is resolving to an adult site.
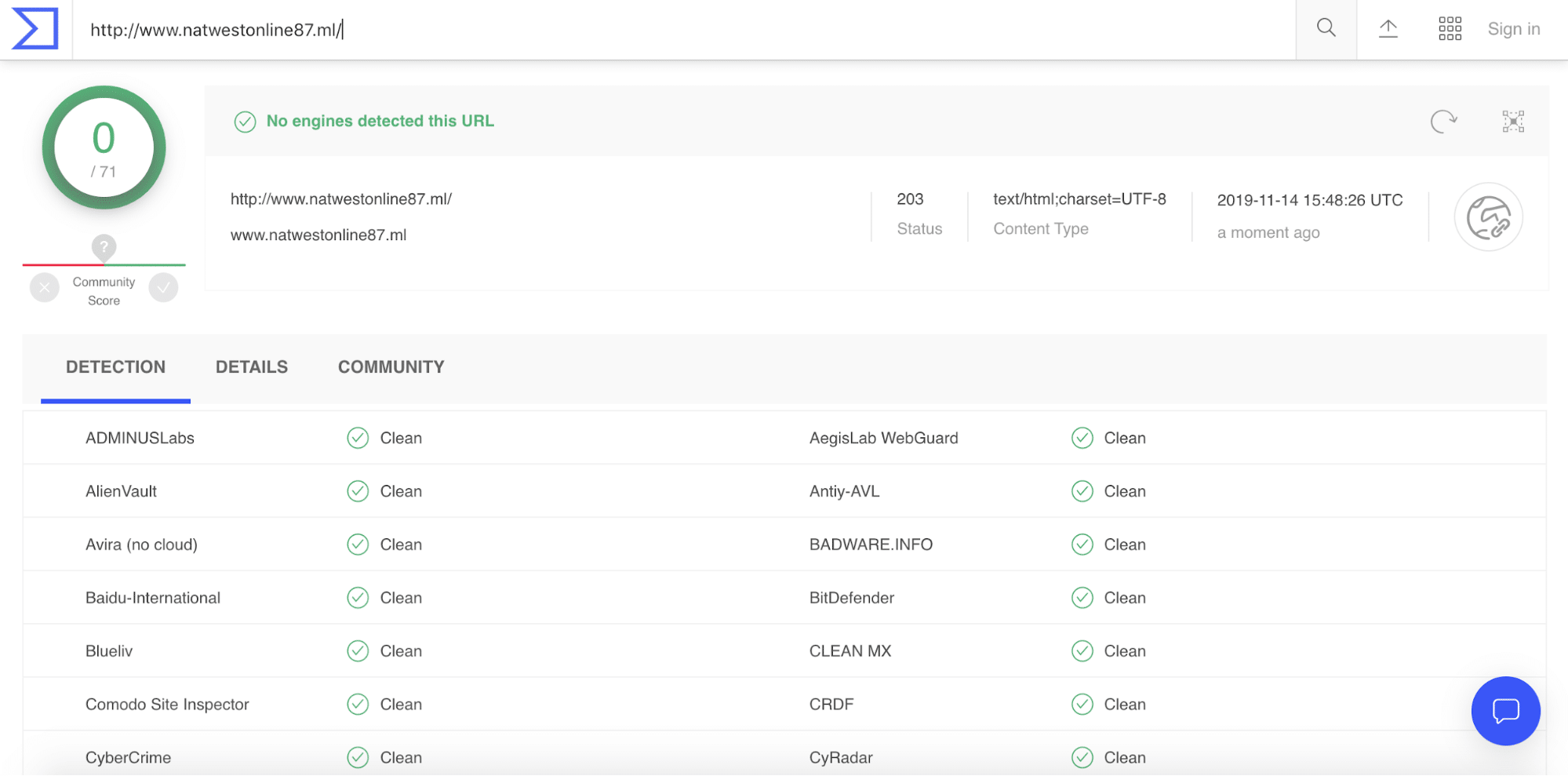
When digging for more information, I looked at the Passive DNS for the last seen data. I was able to find that the domain is resolving to mail.natwestonline87[.]ml and www[.]natwestonline87[.]ml.
I took the www site and leveraged the free version of VirusTotal to see if other sources were marking this site as malicious. They were indeed not, and the overall score was 0.
Conclusion
I’ll be keeping a close eye on the infrastructure and if I uncover anything of value, I’ll be sure to include updates on this blog post. This investigation illustrates the value of having different datasets. In this case, I mapped connected infrastructure using name server hostname, name server IP information, ISP IP information, SSL hashes, and SSL subjects. Furthermore, having more artifacts allows organizations to continue to monitor this nefarious actor to potentially uncover their motivations, create a threat model to most effectively protect your most valuable assets, and proactively block attacks.


