Stop That Phish!

In a recent blog, I sounded a note of caution about not letting the frequent (and alarming) headlines about ransomware wrest too much attention away from other, less spectacular forms of compromise such as BEC (business email compromise) and other simple phishing attacks. “Simple” in this case refers to attacks where phishing is not merely the initial stage of a much more involved operation.
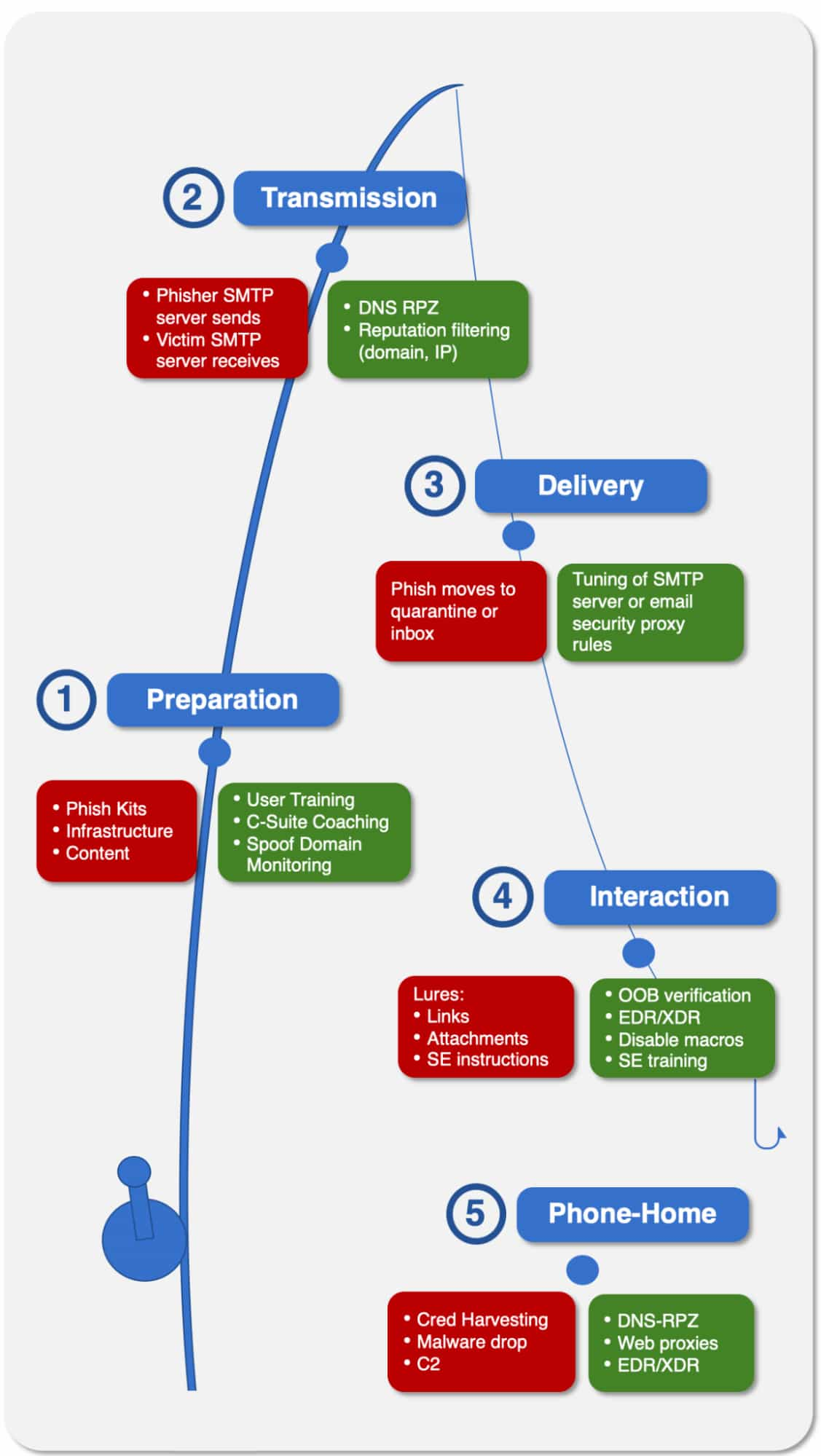
The Phish Chain
The Cyber Kill Chain (CKC) model is a useful framework for understanding how attacks unfold, and what defensive options are available at each stage. Phishing certainly receives its due in the CKC and in similar frameworks such as MITRE’s ATT&CK. But if we zoom in on phishing, we can see that it, too, has its own chain. And as with CKC or ATT&CK, there are various technologies and methods that can help defend against phishing at different stages of that chain. Let’s walk through this chain; along the way we’ll see where a BEC has some different features from other species of phishes.
- Preparation: the phisher sets up infrastructure to support the campaign. There are many discussions of phish kits, so to summarize, this stage involves components such as mail servers, domains, look-alike login page templates, attachments, and C2 (command and control) servers.
- Transmission: the phishing email is sent, using infrastructure prepared in the previous stage, and it is received on the target mail server.
- Delivery: the email is processed into a destination. This could be the victim’s inbox, a quarantine folder, or a spam folder.
- Interaction: if the phish has made it to the inbox, and the victim does not delete it, this is where things start to go “boom.” The victim may click on a link or an attachment, initiate a wire transfer (in the case of a BEC), or reply to the phisher.
A larger attack may have more stages than these, but once we get to here, we are moving past the realm of the phish itself and into later phases of the attack. But let’s dive deep on tools and techniques available to defenders that address each of the stages in the phish chain.
Preparation
At first, it might seem like we would have to be psychic to thwart a phisher before they have hit SEND on the email. But that’s not quite true. There are several ways to get ahead of phishers before the campaign is actually launched.
- Phishing Awareness Training. While acknowledging that users are part of your risk profile, it’s critical to remember that they also can be an important part of your early warning system. Invest in well-executed training, and repeat it regularly. Use incentives to instill a desire to be good phish-detectors (a $5 coffee card for a successful phish detection is a very small price to pay for averting an attack). “Benevolent social engineering” can help spread good habits; publicly congratulate users who report phishes (or even false positives). It’s also very important not to shame people for falling for a phish. It can happen to anyone. With quality training, you can execute your own preparation stage before any emails have been sent (other than your phishing test emails).
- C-Suite Coaching: Encourage your C-suite to welcome out-of-band verification of requests such as wire transfers or gift card purchases. Out-of-band means not using the email thread where the request originated, but instead having the recipient phone or DM the executive whose name is on the request email (or even, in an office environment, walking over to their office and asking for verification). On this topic, it is vital to point out that if the C-suite has fostered a culture of intimidation, subordinates may be less likely to question a request, which could increase the risk of a successful BEC.
- Spoof Domain Monitoring: during the phisher’s preparation phase, they may be registering domains designed to fool the target into thinking that they are interacting with your company, or an organization with which you have a close business relationship. By monitoring new registrations of domains imitating your own and those belonging to your “inner circle” of vendors, partners, etc, you have an opportunity to put up defenses before such domains are used against you. Many BEC phishes use spoof domains either in the sender’s email address or in links within the email body. Tools such as DNS RPZ, web proxies, and SMTP proxies can all cross-check traffic against lists of suspicious or malicious domains, thereby potentially stopping a phish during later stages of the chain.
Transmission
You can’t stop the phisher from hitting “SEND,” but you do have some tools to disrupt the phish chain at the point of receipt of the message – before it even has the chance to make it to a quarantine or inbox.
- DNS RPZ (response policy zone): if you use DNS RPZ in conjunction with spoof domain monitoring and/or ingesting risk scoring of domains, you can prevent your SMTP server from completing a connection with the phisher’s server. RPZ prevents protected hosts (in this case your SMTP server) from resolving hosts on the Internet (i.e. the phisher’s server).
- Reputation filtering: the effect of this filtering is quite similar to RPZ, but the mechanism is different. Some SMTP proxies, firewalls, or installed packages directly on SMTP servers can perform reputation lookups of domains and/or IP addresses of servers sending inbound mail. These tools can block the SMTP exchange itself before inboxes are even part of the picture.
Delivery
If the phish is not stopped at the transmission phase (and many are not), there are many technologies that can prevent it from landing in a would-be victim’s inbox.
- Delivery rule configuration and tuning: one of the advantages SMTP has over other protocols such as HTTP/S is the spectrum of available responses, based on rules in the server (or email proxy). Reputation filtering as mentioned above can also act on the delivery phase, with configurable scoring thresholds for different dispositions such as discard, quarantine, or deliver. This is also the phase in which scanning of email body, links, and attachments can detect suspicious features. Such scanning may use a variety of methods, from simple signature matching to more complex analysis, sandboxing/detonation, etc. Because of the power of these technologies, it’s worth investing time in tuning the rules engines. Popular mail servers such as Microsoft Exchange, and vendors of purpose-built email security gateways, have extensive documentation on optimization. This can be time consuming, and it’s not a set-it-and-forget-it operation since phishing techniques evolve constantly. However, well-tuned SMTP rules can really pay off in preventing delivery of malicious content.
Interaction
If the phish has made it this far, it is either in an inbox or a quarantine folder. Quarantine does offer another line of defense; many quarantine rules disable links and block attachments until the user positively releases the email to the inbox. When the phish is in the inbox, there are yet more ways in which the attack can be thwarted. User education, of course, becomes user action at this phase if the user recognizes the suspicious nature of the email and deletes it, forwards it to a designated security inbox, or simply reports it without clicking on anything. But there are other ways in which the interaction phase can be secured.
- Stay up to date on social engineering techniques. Phishers are using novel approaches, many of which do not involve links or attachments in initial emails. The well-known BazaCall campaign, for example, instructs victims to call a phone number to cancel an unwanted (but fictitious) subscription.
- Out of Band Verification: another place where user education or company policy is enacted. The would-be victim contacts the necessary person(s) to determine whether a request is valid. By the way, this verification should also extend to third parties such as supply chain partners, creditors, government agencies, etc.
- EDR/XDR (Endpoint/Extensible Detection and Response): these technologies can prevent executable code in a malicious attachment from firing. They can also be configured to prevent user actions such as enabling macros in documents.
Phone-Home
If the user has clicked on a link or an attachment that initiates a connection to adversary infrastructure, there is one last line of defense in the phish chain: stopping that connection. These connections are typically over HTTP/S, but depending on the specific attack, could also involve other techniques such as DNS tunneling.
- Web proxies and DNS RPZ: if the phish contains a link, a web proxy or the aforementioned DNS RPZ can prevent the victim’s computer from establishing a connection to adversary infrastructure. EDR/XDR technologies can also act at this stage, if they include features to check domains or IP addresses against risk or reputation scoring databases.
Conclusion: It’s a Tough Fight, but Worth the Effort
Obviously, if there were a silver bullet against phishing, things would look very different in infosec. But there are a lot of different tools available to thwart phishing. While it’s correct that security can’t be “solved” by throwing technology at the problems, it’s equally true that a lot of skill and ingenuity have gone into technologies that can help at all of the stages of the phish chain. Don’t lose hope!


