Teaching InfoSec in West Africa: A Lesson in the Value of Diversity
I recently had the distinct pleasure of returning to the African Institute of Mathematical Sciences (AIMS) in Mbour, Senegal as a visiting lecturer. This was my second time teaching at AIMS Senegal, and I was happy to return. AIMS is a pan-African network of Centers of Excellence for post-graduate training, research and public engagement in mathematics, physics, and computer science. After the inception of the first Center of Excellence in South Africa in 2003, AIMS Senegal became the second school based on the South Africa model under the framework of the Next Einstein Initiative. AIMS is feeding the STEM pipeline in Africa and internationally by training African students for a Master’s in Mathematical Sciences, including a co-operative option with a direct link to industry. AIMS Senegal is also home to a Research Center which supervises and funds doctorate and postdoctoral research.
The 2018 AIMS Cohort consisted of about 60 students, roughly half of those in the co-op program. Co-op students spend part of their academic career focused on big data and computer security courses and problems. The campus is situated on the Atlantic coast, just a few hundred feet from the shoreline. Walking between classrooms yields stunning views of the iconic Senegalese fishing boats out for their daily catch.

My course for November 2018 was Computer Security II: Network Fundamentals. I was asked to tailor the course toward the Cisco Certified Network Administrator (CCNA) certification, with as much security baked into the networking coursework as possible. I had 25 students in the course and 2-3 tutors for any given class period. The students had a variety of backgrounds and came from all over the continent. In this block, I had students from Benin, Cameroon, Ghana, Nigeria, Senegal, Kenya, Rwanda, Chad, Niger, Burkina Faso, Ivory Coast, Mauritania, Burundi, and the Democratic Republic of the Congo. This made for a teaching challenge in meeting everyone at their level of experience, but also a wonderful diversity of perspective and background.

In three weeks of intensive instruction and lab work, we were able to cover the open systems interconnect (OSI) model of networking; routing and switching algorithms including minimum spanning tree (Prim and Kruskal’s algorithms), Routing Information Protocol (Bellman-Ford algorithm), Open Shortest Path First (OSPF, Dijkstra’s algorithm), and the Border Gateway Protocol (BGP); spoofing attacks at the link and network layer; web application analysis, attacks, and defenses; network segmentation, firewalls, and access control lists; Internet infrastructure and geography; and a variety of materials about malware, botnets, and advanced persistent threats. Throughout the course, I sought to engage the student’s background in mathematics as much as possible (hence the focus on algorithms) and weave security and current events into the coursework. Thus, we were able to talk about Google’s new proposals for moving the common web protocol http (the hypertext transfer protocol) to use the stateless UDP (user datagram protocol). We were also able to talk about recent news of various BGP misconfigurations and hijacks.
We had the use of a computer lab that was maybe not as modern as I would like, but still got the job done. AIMS has a group of volunteers that maintains its own GNU/Linux distribution, based on Debian 9. Though this tends to be a little resource heavy for the computers the students have access to, they remain quite capable. We were able to do fairly complex network simulations using the open source GNS3 network simulator. This allowed students to configure, test, and troubleshoot technologies like virtual local area networks (VLANs), routing protocols like the aforementioned OSPF and RIPv2, as well as router ACLs and redundancy techniques like service level agreements (SLAs). GNS3 has a number of features that makes it an excellent instructional tool, including integration with docker so that students can run complex application layer protocols, and integration with Wireshark so that students can analyze traffic as if they were on a real network segment. We also used the mininet network emulator to analyze BGP route hijack attacks.

The students at AIMS Senegal are some of the best I’ve encountered. During my time at DomainTools, I’ve interviewed a number of recent graduates from undergraduate and graduate programs in the United States, and when I was at Argonne National Laboratory, I helped run the summer student programs for computer security. Though all the students I’ve had a chance to interact with in my professional life have been quite good, the level of curiosity, willingness to engage, and tenacity of the students at AIMS Senegal is truly impressive. It is only because of their dedication that we were able to get through the incredible amount of material we covered in my three weeks there.
As a final project the students were given a realistic set of network requirements along with a set of network design principles and were asked to design this network. We geared the project such that they would have to solve real problems that would be faced in designing and implementing an enterprise network. They needed to satisfy network connectivity, segmentation, redundancy, and security. In addition to the design itself, they were required to write a design document, explaining the motivations behind their designs and the controls they put in place to satisfy the requirements.
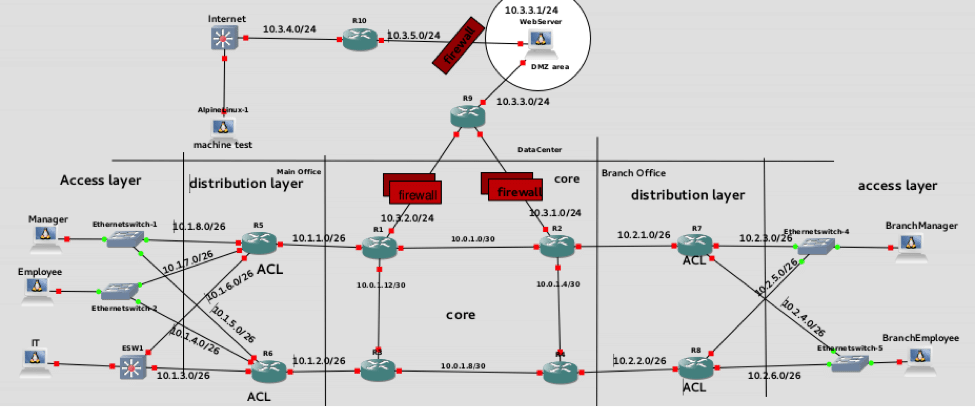
The students came up with a number of inventive designs, and though this project may not have had the “cool” factor of other projects I’ve administered focused on penetration testing or vulnerability analysis, the students really got to apply the skills that they learned in a problem space that many network administrators fail to observe and think about the subtleties of.

In my 15+ years working in technology, I’ve definitely experienced the value of education and experience first hand, both in my own work and in hiring and mentoring. However, the employees and coworkers I’ve had that were game changers weren’t those who came from a good school or had the best jobs on their resumes—they were people who brought different perspectives and problem solving skills to the table. In information security especially, we are frequently facing problems that no one knows how to solve… problems that often involve intractable compromises and battlegrounds that are asymmetric. What we need to solve these problems can’t be taught in a classroom. Instead, we need diverse backgrounds coming together to discuss, implement, experiment, and test. Classroom learning and experience are certainly important contributors to the success of any professional, but curiosity and grit are critical characteristics I look for in people I want to work with and for. In infosec, we need bold hypotheses, innovative approaches, persistence in the face of failure, and a variety of perspectives.
Students from programs like AIMS Senegal bring so much to the table that I do not see in my average applicant pool. In their lives, many of them have had to solve problems that most of us can only imagine, just by the circumstances of where they were born and raised. As parts of Africa continue to modernize, it is imperative that we as a technology community engage with this up and coming workforce and the infrastructure and environment that they are coming of age in. These students have vital perspective that we need to solve the difficult problems we face as an industry. If you are interested in sponsoring students for internships or careers, in volunteering, or becoming a sponsor of AIMS or the Next Einstein Forum, reach out to them directly, or contact me and I’d be happy to make an introduction.

I’d like to thank AIMS for welcoming me with open arms, and above all, the students and tutors I had the pleasure of working with in November of 2018.



