The Most Prolific Ransomware Families: 2023 Edition
Share this entry
The ransomware landscape has changed significantly since our last post where we identified the most prevalent cybercrime groups of the time and examined the industries most impacted by their activity. Our previous post came on the heels of a series of high-profile ransomware events, and as such we reviewed the activity of the top ransomware groups at the time, including Conti, Maze, and REvil/Sodinokibi.
Since that post’s publication, there have been significant changes to the ransomware landscape and the groups that conduct ransomware activities – enough to warrant an update.
Executive Summary
- External forces have had a significant impact in reshaping the ransomware landscape
- Ransomware group activity and victimology is highly dynamic, requiring consistent monitoring of trends in targeting by group
- While still politically sensitive to some ransomware groups, recent campaigns against the healthcare, higher education, and government sectors are notable and alarming in their frequency
- As the ransomware-as-a-service (RaaS) model continues to evolve, groups are competing for top affiliates to their services, challenging historical attribution of threat actor activity
Reaction to External Forces and Notable Disruption Activities
Global business and geopolitical events play a strong role in shaping how these groups operate and how they respond to market conditions such as changing external forces. In order to continue to operate and profit from their malicious activities, ransomware groups respond quickly to new vulnerabilities facing victim organizations and rapidly pivot to ensure their operations continue to provide significant returns on their investments in this space.
At the start of the COVID-19 pandemic there was a perceived ‘thawing’ of historically adversarial relations between western law enforcement organizations and their Russian counterparts. This culminated in a US/Russia summit in 2021 between their respective Presidents, where ransomware and its associated activities were a part of the agenda. Arrests of members of the REvil ransomware group in January 2022 were closely watched by ransomware groups to try and understand the nature of this perceived new risk in their business models. Prior to those arrests, ransomware groups had largely operated under an understanding that if their operations did not impact victims within the Russian Federation, then the likelihood of domestic law enforcement actions against them would be minimal and did not pose a significant risk to their continued operations. Following the REvil arrests, we believe that many groups, including ICEID, Trickbot, and Emotet, amongst others, reduced or suspended activities while they sought to better understand the impact these changes in conditions might mean.
However, these concerns were short-lived as geopolitical influences overshadowed or eliminated them entirely, with the invasion of Ukraine by Russia in February 2022. While the groups’ hiatus didn’t last long after the invasion, it is notable to observe the way that they included such calculations in their business plans, a theme that can be seen many times over in their propensity to either rebrand as “new” entities in response to sanctions against a specific group, or to distance themselves from victim activities that drew too much unwanted attention, as in the case of the Colonial Pipeline event, Ireland’s Health Service Executive (HSE) event, and JBL Foods ransomware attack.
The most significant geo-political influence on the ransomware ecosystem is the previously-mentioned Russia invasion of Ukraine. While many actors associated with such activity reside in Russia, their operations, like their victimology, are global, with “team members” of many different nationalities and jurisdictions. The most high profile example of this is the impact of pro-Russian statements made in the early days of the conflict by members of the Conti ransomware gang. In the ensuing days after the invasion, strong pro-Russian and anti-west statements were posted by the group firmly aligning themselves with Russia. In quick order, the group tried to walk back those comments, but the impact of their proclamations would have a catastrophic effect on their operations.
Known publicly as the “Conti leaks,” a purported Ukrainian researcher, or possible member, retaliated by leaking a significant amount of data and internal documentation about the nature of their operations. This data provided a unique and previously largely unseen glimpse into the inner workings and business operations of such groups. Within weeks of the leak, a significant amount of Conti’s infrastructure had been decommissioned and shortly thereafter their existence as an organization was brought to a close. This had a dramatic effect on the ransomware ecosystem over the past year, with elements of the old Conti gang reforming into new operations, colloquially referred to as the “Sons of Conti,” and thought to include new players like Royal, Black Basta, Karakut, and Quantum.
Landscape in Early 2022
With thanks to the wonderful team and amazing data at ecrime.ch, we will review the current top groups by victimology. We sought to highlight the effects of the recent attacks on defenders and to understand the relationships between the various groups and their targeted industries or organizations. We will first review the top groups and targeted organizations from early 2022 and then compare them to the spring of 2023 – that is, from just after the invasion of Ukraine to now.
Top Ransomware Groups by Victimology
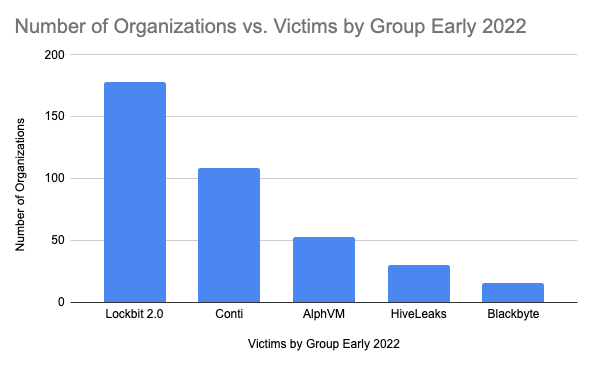
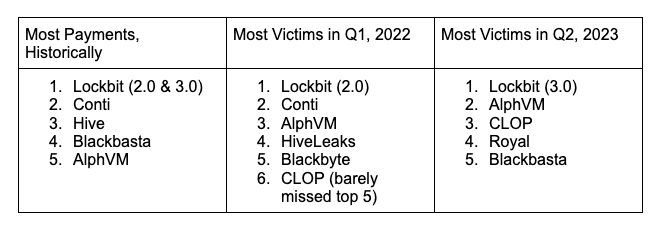
Figure 1, ransomware group activity from early 2022, illustrates the impacts that ransomware ecosystem changes have had on the various groups and their activity. Compared to previous activity in our blog from 2021, groups like Maze, REvil, Egregor, and others are no longer in existence, with only Conti and CLOP (ranked 6th just behind Blackbyte) maintaining a ranking based on victimology. New players like AlphVM, Karkakurt, and Blackbyte had only started to hit the radar screen. Of note is the ascendancy of LockBit in its various versions since our previous blog, a trend that has only continued to grow over 2022 and 2023.
Targeted Industries in Early 2022
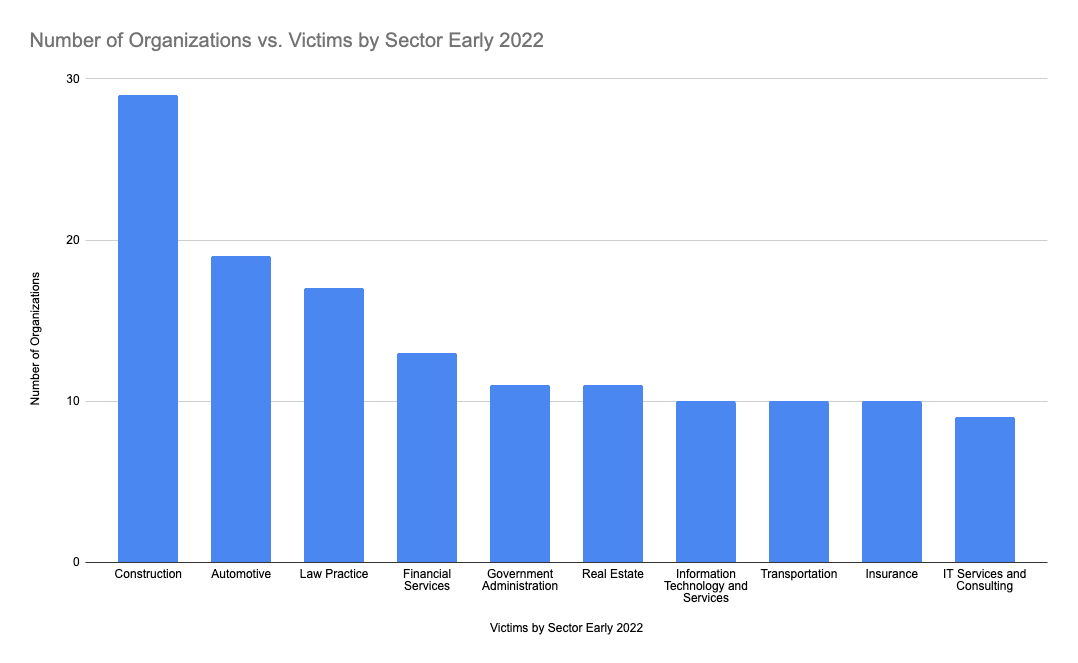
Again with the assistance of the data from ecrime.ch, we can see how the changing ransomware ecosystem impacts targeted industries in Figure 2. Largely due to the targeting choices from Conti, automotive and real estate industries form two of the top four industries impacted by ransomware activities. Also of note is the prevalence of organizations in the construction industry and law practices as well. These two industry segments continue to form a large segment of victims in more recent months.
The rationale behind the targeting efforts against these industries can in part be tied to the “double ransom” model virtually all cybercrime groups have adopted since we published our last blog post. In addition to historical encryption of victim networks, actor groups now exfiltrate the victims data in an attempt to apply further pressure on the victim for payment, with the explicit threat of publicly disclosing their data should they choose not to pay. Indeed, several groups are now publishing victim company information, or in some cases, employee or customer data directly to shame victims into paying.
For industries such as legal firms, the threat of disclosing private client information can be powerful leverage for actors trying to induce payment. Other influences on targeting relate to the size of firms in a particular sector, as well as the impact that such events have on their business operations. Actor groups routinely use publicly available information, such as ZoomInfo, to determine their initial extort demand, and threaten small and medium sized businesses with lost productivity or disruption of time sensitive projects to induce payment such as in the case of victims in the construction industry, for whom construction projects need to proceed without delay. For victims in the education sector, the public reporting of the suspension of classes or services to students is also a consideration from actor groups, with leaked internal actor chats suggesting that they send students on vacation early, knowing that such events have a strong impact on ransomware negotiations.
Cybercrime Landscape, Spring 2023
Top Five Groups by Victimology, Spring 2023
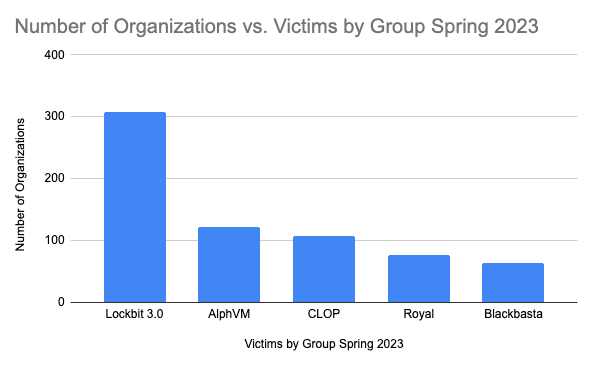
In 2023, the ascendency of Lockbit, AlpVM, and CLOP continues to grow with the three ransomware groups significantly outpacing the victimology of other groups such as Royal and BlackBasta. Figure 3 shows the new landscape with Lockbit still on top. With the release of their new 3.0 version of the LockBit ransomware, efforts to increase the number of affiliates in their ransomware-as-a-service (RaaS) model continue to build steam with advertising in forums actively seeking to build on their market share in this space, including their own bug bounty program. This effort continues to illustrate the organized and business focused nature of these actor groups. Better than most industries, they quickly adapt and pivot to new business opportunities to leverage the disruption and change in the ransomware space to their advantage. With massive cash still to be made, organizations that can provide reliable and effective services to their users can quickly garner significant new resources by which to cement and expand their place in the market. This is a trend we fear will pick up again over 2023.
Targeted Industries, Spring of 2023
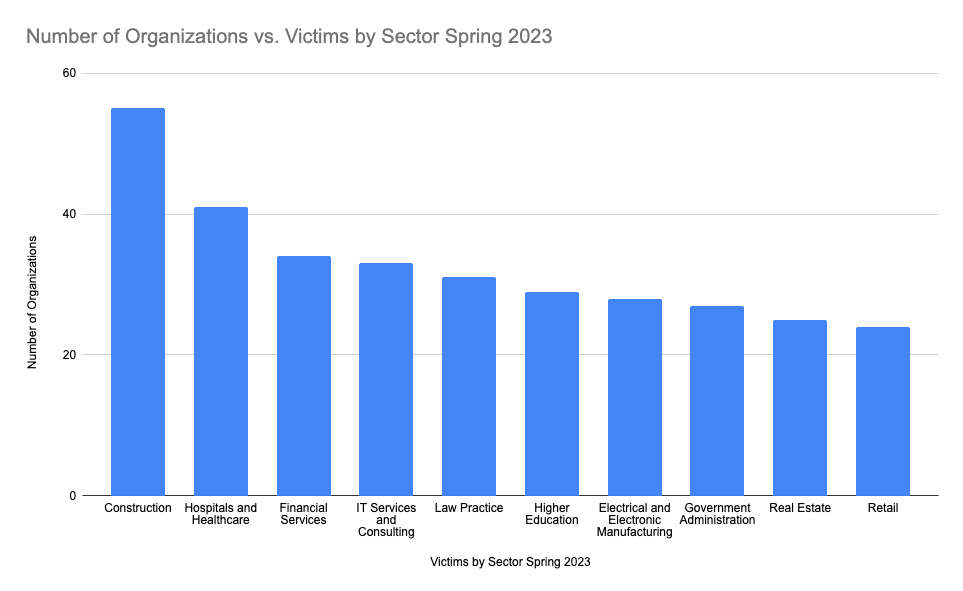
The consolidation of the top ransomware groups and increased activity levels has a profound effect on industry statistics and victimization. While the construction and legal industries remain prominent targets of such groups, Figure 4 shows other industries have risen in prominence where victimology is concerned. While not a new phenomenon, hospitals and the healthcare industry at large have also recently been the subjects of such attacks in greater numbers, jumping to the second spot. While healthcare attacks have increased, it remains a sensitive issue for ransomware groups. Following the Conti attack on the Irish Healthcare system and the late 2022 ransomware event with the Toronto Children’s Hospital, both Conti and Lockbit sought to publicly distance themselves, blaming affiliates for the attacks. The increase in a couple of the industries targeted, such as Healthcare, IT Services, and Government Administration, can in part be explained by the increase of activity related to CLOP which, as well as notable victims in the retail sector such as Saks Fifth Avenue which was added to their leak site in March 2023.
Influences on the Ransomware Ecosystem
Beyond the effects of geopolitics and its influence on the RaaS space, there are other interesting dynamics at play that have shaped and continue to influence the operations and activities of ransomware groups. Of note are activities by western law enforcement organizations to disrupt the services which ransomware groups use to finance and fund their business operations. In recent months, coordinated efforts to sanction and shut down illicit cryptocurrency exchanges have been one example of disruption activities aimed at helping to stem the activities of ransomware groups. Additionally, the sanction of individuals tied to the Trickbot group have also featured prominently in efforts to disrupt actors historically associated with ransomware activity. There have also been notable indictments and arrests as well which can change how these groups operate.
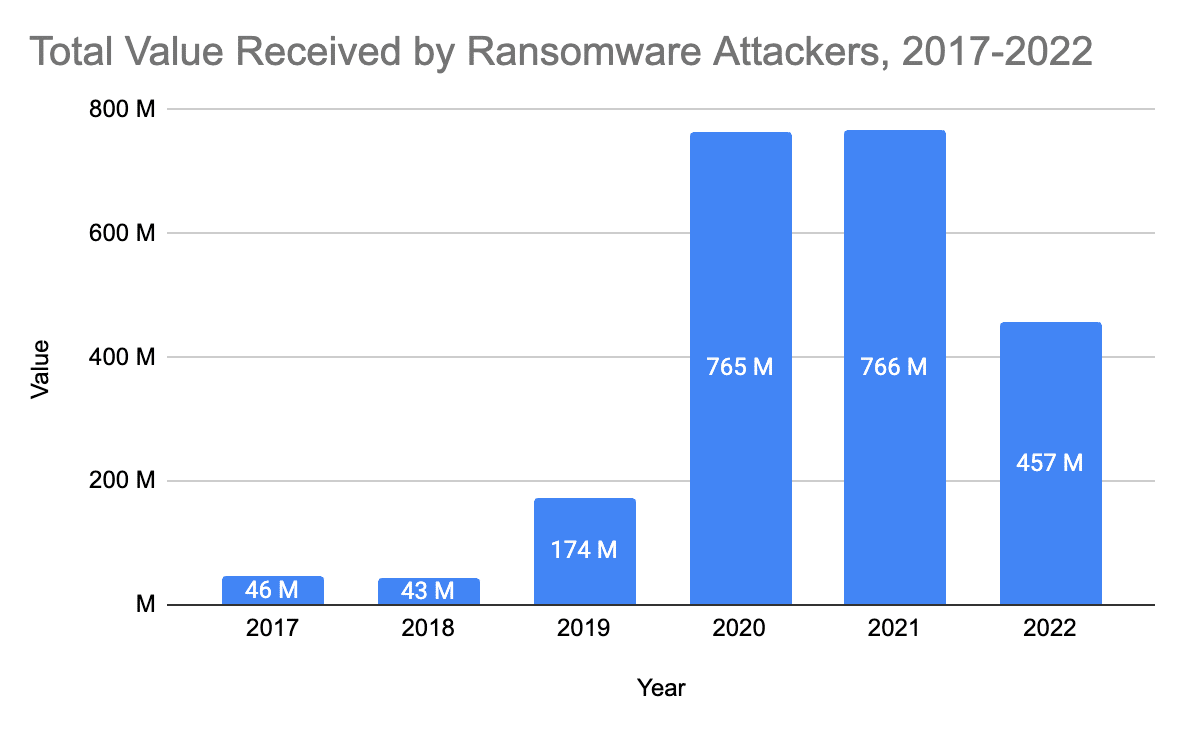
Also of note is the propensity of victims to pay ransoms when faced with extortion demands. As reported by Chainalysis and summarized in Figure 5, there was a drop in ransoms paid to actor groups year over year from 2021 to 2022, from $766 million in 2021 to $457 million in 2022. While there are many contributing factors, the propensity for victims to pay is an interesting and important development. In part, the security posture and ability for victims to restore from backup without needing to pay a ransom could be a positive sign of organizations securing themselves from such events. In addition, the influence of cyber insurance policies and the willingness for insurance companies to reject claims for such events has also been a trend in recent months and years.
What Does This All Mean?
These shifts in the ransomware landscape are fundamental and foundational. As shown in Table 1, the overall top group between 2022-2023 remains Lockbit. Conti, while historically a very large player in this space, has disappeared with other competitors growing quickly. What we don’t know, however, are the actors who are making up these new groups. Are these groups really new, or are they reformulations of older groups with new names? As mentioned above, there is evidence Blackbasta is composed of Conti members.
There are two trends we see: First, even though the total amount paid in ransom seems to be on the decline for now, the targets and risks are increasing. We see this both in the total number of victims growing since the start of the Ukraine conflict as well as in the broader set and changing set of target industries. Specifically notable are the rise in attacks against healthcare, higher education, and local government–industries where loss of services directly affect people’s lives and livelihood and where historically IT and security have been relatively underfunded. These are not industries where they have a lot of money to pay, but rather feel higher pressure to pay in order to restore services faster.
Second, the Ransomware-as-a-Service (RaaS) affiliate business model is now firmly established. This “professionalization” of ransomware suggests a robust and growing marketplace where affiliates using RaaS can isolate and target specific segments like healthcare or even specific geographic regions like Central & South America. Looking forward, however, a maturing marketplace could also mean a commodified one, where affiliates might “shop around” and compare different RaaS providers looking for better terms or improved support and services. A side effect of this means potentially higher quality ransomware to meet this market need, leading to a greater number of successful attacks against the rest of us.
Conclusion
As the ecosystem continues to evolve, it will be interesting to observe which new groups eclipse others as the revenue generators from ransomware activity going forward.
In relation to this, with a decrease in the number of organizations willing to pay, and associated revenues dropping, competition amongst RaaS offerings is likely to increase, as various groups jockey for coveted affiliates. This has already been observed with apex affiliates “shopping around” for their business and employing multiple different families of ransomware at any given point in time.
This poses a significant new challenge for defenders. As ransomware groups changed over 2022 and into 2023, TTPs were leaked and group members reorganized taking tactics, and in some cases source code, with them. The blurring of lines between TTPs, infrastructure, and code bases amongst ransomware groups will likely prove to be a significant side effect of all this activity, making attribution efforts more challenging, and the need for accurate information from threat intelligence companies more pronounced.






