The Power of DNS OSINT in Detecting Supply Chain Compromises

NOTE: Iris Detect has supplanted PhishEye, with dramatically expanded capabilities. Please explore Detect for your brand protection, anti-fraud, and spoof infrastructure analysis needs.
Introduction
The SolarWinds incursion was first announced about four months prior to this writing, and its full extent is still not known and may not be for years. While there is absolutely nothing good about the event, or the follow-on events it may have enabled, it did force the infosec world to pay a lot of attention to supply chain shenanigans, and to think harder about what we need to do to protect ourselves against them.
We place a lot of trust in supply chain partners because we have to. Even with a zero-trust philosophy, once we actually have vendor- or partner-supplied services or infrastructure in our production environment, we are ipso facto trusting them, whether we like it or not. Most security operation centers (SOCs) have more than enough to do in keeping an eye on their own assets; they trust partners to be doing the same within their domains (pun semi-intentional).
And yet, anything that has a tight integration into our ecosystem, whether via automated processes or via human interactions, must be accounted for in threat modeling as if it were part of our own environment, since it effectively is. SolarWinds provides valuable network monitoring and management solutions and as such is deeply integrated into the fabric of the network. In a different way, companies such as Salesforce and ServiceNow have their own integrations, though these touch different parts of the ecosystem than the likes of SolarWinds. Consider other parts of a supply chain, too. If you are a producer of consumer electronics or other goods, there is a high probability that you use contract manufacturers for some or all of the assembly of what you sell. You may or may not have integrations at the level of automation with them, but you certainly exchange sensitive data, such as design documents or other intellectual property. The threat models that account for all of these varieties of supply chain are different, and they’re all important.
Spoof Domains: Think Beyond Your Own Brand
Many companies, especially larger ones, devote significant resources toward monitoring the Internet for spoofs of their brands. The nature of the spoofs varies with the type of organization, or with the intent of the actors creating the impersonating domains. Luxury brands are besieged with counterfeiters selling knockoff goods, undercutting the brand and causing potential reputational harm. Financial institutions fight off cybercriminals looking to harvest credentials from customers. Companies in every vertical face spoofs of internal, employee-only domains used for VPNs or corporate email access, where criminals hope to swipe credentials of those who work at the company itself (as opposed to its customers). To include such activities in threat modeling is just common sense.
But if the supply chain is a trusted extension of our own environment, doesn’t it make sense for our threat modeling to encompass what happens if one of those organizations is compromised, as well? This suggests an augmentation of the common brand-protection threat model to include keeping an eye out for imitators of the trusted partners. It’s not hard to model out ways in which a successful spoof of a partner could lead to a bad day.
- If an attacker were able to hijack automated processes to point from the partner’s infrastructure to attacker-controlled infrastructure, they could disrupt or halt the processes depending on that connection.
- If the attacker spoofed a business partner via social engineering, whether email phishing, smishing, or similar, they could convince a victim to transmit sensitive data to them.
- If the attacker spoofed a ticketing system or other business enablement platform and phished credentials, they could gain visibility, and from there perhaps control, of various parts of the victim organization’s operations.
You have probably thought of a couple of other models to add to this, just in the time you’ve read the last couple of paragraphs. But let’s look at a hypothetical example.
The Sad Cautionary Tale of Acme Grommet
Suppose you work for Acme Grommet Company (the world’s greatest grommeteers, to be sure). Suppose, further, that your manufacturing depends on your longtime partner Amalgamated Tool and Die (AmTodCo). Each time you develop the season’s latest must-have grommet, you send CAD files to Amalgamated, which they use to create the masterpieces that you sell.
If your brand protection and threat hunting operations have become adept at watching for spoofs of your brand, they’ll catch the various “acmegr0mmet” domains that come along from time to time, and deal with them. But if they’re not likewise looking out for “amt0dco” domains, they might miss the domain that phishes your design department, hijacks the designs for the grommet-to-end-all-grommets, and sells them to your archnemesis SuperGromCo. That’s a bad day, and to add insult to stock decline, it was preventable, with a bit of adjustment to your threat modeling and spoof monitoring.
And Now for the Not So Hypothetical
The following screenshots from DomainTools Iris were taken in April, 2021. The domains in them were all under two years old, many of them less than 6 months old. You can be sure that they weren’t registered just for grins. If this were a blog about Iris, we could follow the various pivots connected to several of these domains and expose larger operations with many illicit domains in use. The high risk scores on these domains show that the DomainTools Risk Score found similarities or connections between these domains and others already on popular block lists. (If you’re not familiar with our risk scoring, suffice it to say that scores in the 90s represent extremely high confidence that the domain is malicious.)

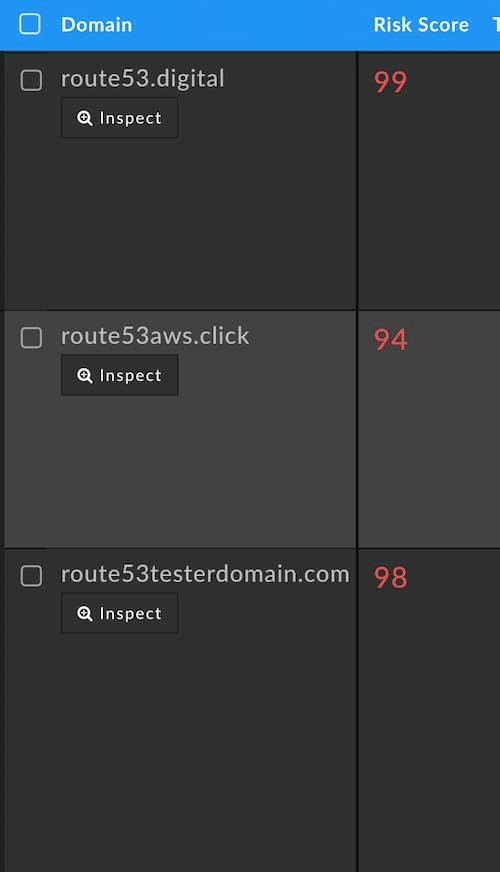
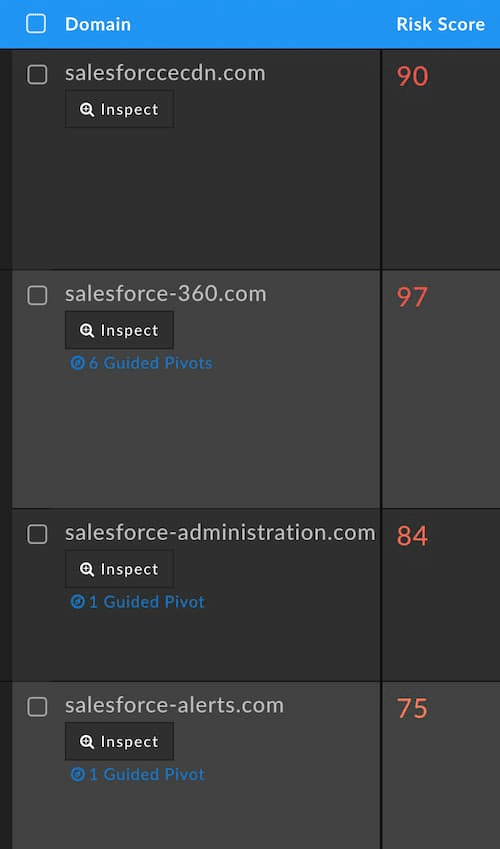
PhishEye and the Supply Chain
DomainTools PhishEye is designed to flag domains that spoof a given keyword and bring them to the user’s attention. It uses a suite of fuzzing algorithms that identify many different tricks that malicious actors use to create look-alike domains, including some (called homoglyphs) that can be extremely hard to spot, even when you’re carefully looking for them. Companies tend to use PhishEye to monitor their own brands; but PhishEye doesn’t care what brand you input into its search box. Therefore, it’s an ideal tool for identifying spoofs of your partner companies and vendors.
The workflow might look something like this:
- Determine which organizations you have the most sensitive relationships with, and add these to your threat modeling
- Add their names (including their various sub-brands) for monitoring in PhishEye
- Review PhishEye’s daily reports
- When spoof domains are found by PhishEye, check your DNS, web proxy, SMTP, and other relevant logs for evidence of any traffic from your environment to these domains. Or build detections to flag any future hits.
The PhishEye API can be used to automate the gathering of the newly-found domains, to streamline your processes.
Actual traffic from your trusted environment to one of these spoof domains would be a big deal, and your IR team would want to be all over it. In most environments, this would be a low-probability event, but its impact could be high. Given that the expansion of the threat modeling, and the detection/hunting necessary to catch such spoofs are not overly complex, the adjustments may be well worth considering.
Conclusion: An Ounce of Prevention…
Monitoring for spoofs of your trusted partners is far from the only important way to help guard against supply chain attacks, but it is one that is but a minor expansion of an already-familiar pattern (monitoring your own brands). If you are already a PhishEye user, try inputting some keywords related to your ecosystem, to see what spoofs are already out there. If you use Iris but not PhishEye, you can get partial results (minus the clever fuzzing algorithms) by using the “Domain Begins With” or “Domain Contains” operators in the Advanced Search controls, to cast about for spoofs of your partner companies. Neither of these takes long to do, and the results could be eye-opening.
Be safe out there
Tim


