Unraveling A Telecom Billing Fraud Campaign Targeting UK Users
Introduction
In the day-to-day activity of the DomainTools Security Research Team, we regularly monitor our domain collection and discovery efforts for intriguing terms and sites that may lead us down new investigative pathways. One site that came through recently was account-help-online[.]com. To the trained eye, this domain is clearly nefarious but to the intended targets of the phishing campaign, the domain appears legitimate. Since the domain has not yet appeared on a blocklist, we decided to use Iris to investigate further.
Digging In – The Strengths of Passive DNS
An initial look into this domain shows that there is no IP address assigned to it yet in Iris. We just check the apex domain for an assigned IP in the pivot engine, but more on that in a minute. In addition to no IP to pivot on there is no registration information due to GDPR redactions. At first glance it would seem that this investigation is a dead end.

However, one of the most useful tools in the post-GDPR world is our Passive DNS (pDNS) data. The research team here finds the pDNS integrated into Iris Investigate to be an essential tool to find additional pivot points as pDNS provides us with additional hostnames and IPs that would normally go unnoticed without doing speculative DNS queries. In this instance, by searching for all records available on this domain we can see this is a clear phishing campaign targeting PayPal users.
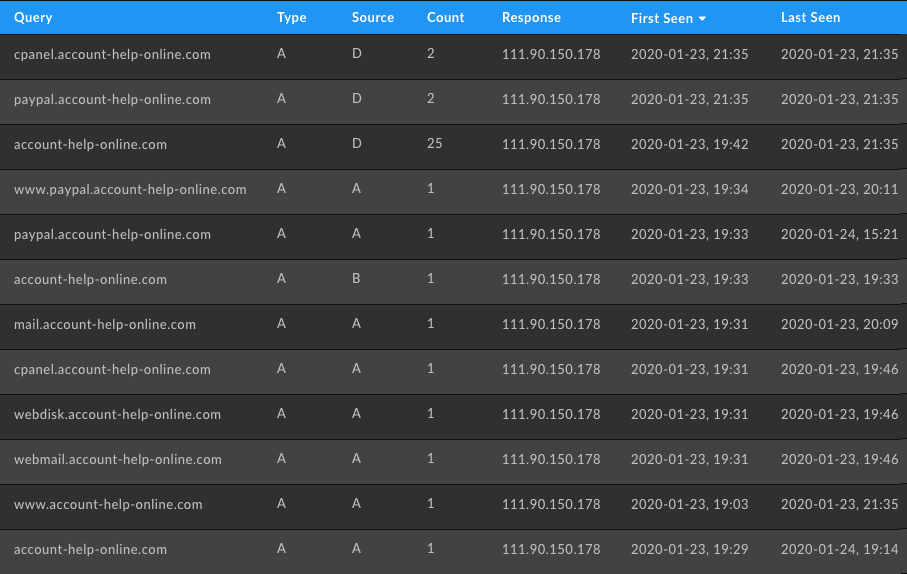
We then took that IP address and threw it into the Pivot Engine to reveal 120 malicious-looking domains starting with the terms “billing” or “ref” and ending with a sequence of numbers. Typically phishers will create hundreds of domains so they can cycle through infrastructure during their attack. When one domain gets flagged as malicious and added to blocklists, they have another and can immediately continue their operations. Amongst all these domains one stood out to us: ee-customer-support[.]com.
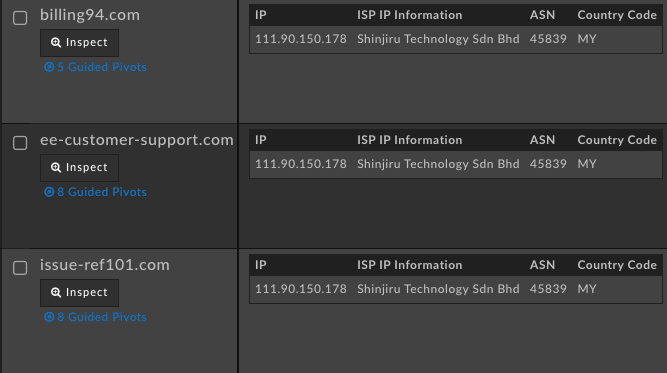
EE is a UK telecommunications company that is a part of the BT Group which makes up just under 30% of the UK market share. At this point we can see that most of what is being served off of this malicious IP is actually billing fraud targeted at UK consumers. While many of these domains are blocklisted, a good chunk of them are not, but our machine learning classifiers in DomainTools Risk Score have accurately rated all of the domains at or above a score of 99—the most dangerous rating a non-blocklisted domain can receive.
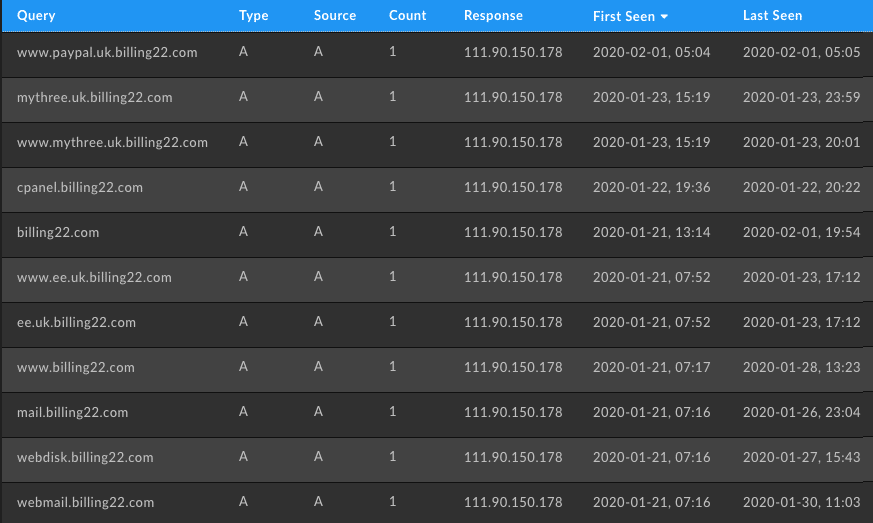
Looking at the apex site for those domains reveals an empty cgi-bin folder which is usually an indicator of a phishing kit’s scripts. Unfortunately without an actual sample we cannot access the files as the HTTP request is blocked with a 403. Using URLScan, however, we can find scans from previous users for these domains containing the proper full URI that reveals what is going on with those domains. In the case of the domain billing22[.]com we see that the phishers are also attacking 3 which is another UK telecom.
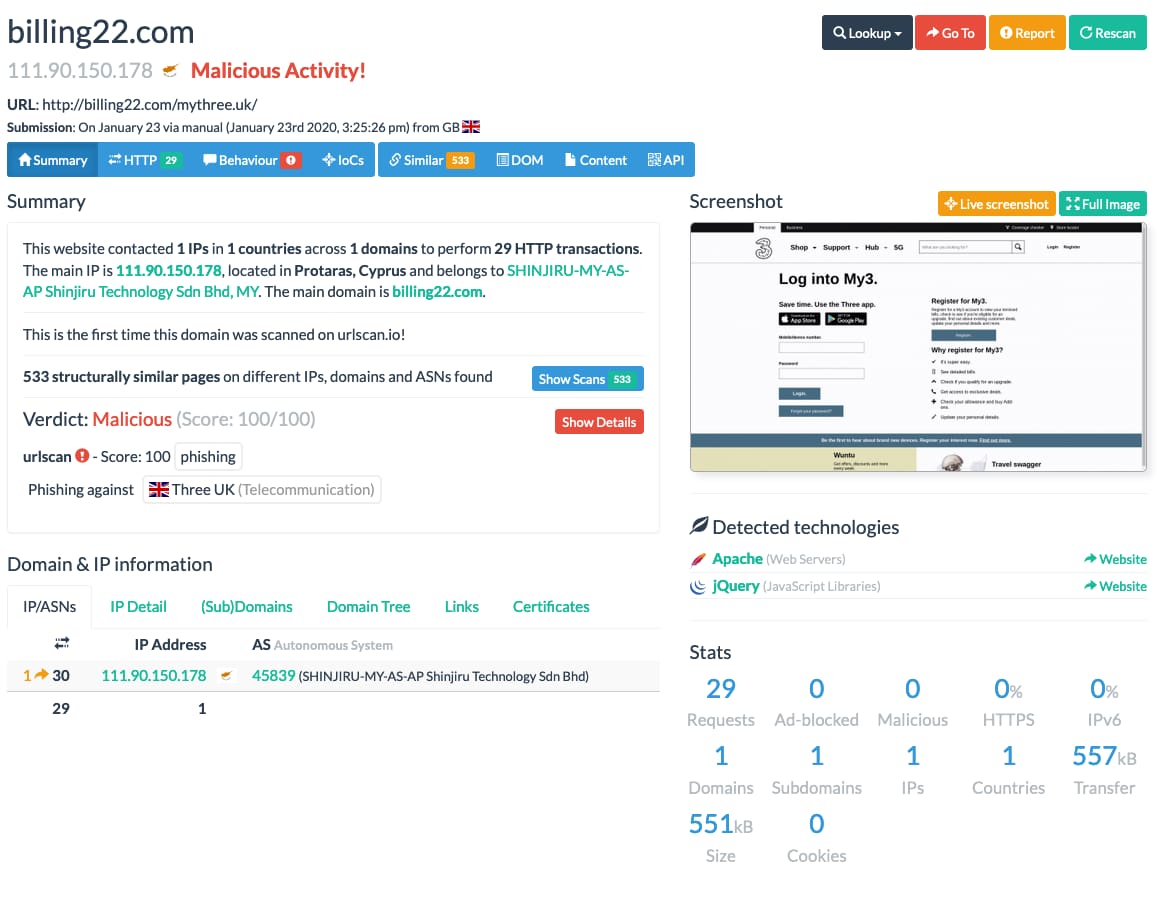
At this point we were curious what other providers and services may be targeted so we decided to query for the wildcard domain name in pDNS data within Iris Investigate. From what we can tell it’s mostly targeting telecom and PayPal customers, but they hosted a number of Apple phishing domains on the same IP address, so we consider it safe to assume that Apple users are being targeted as well.
From here we tried to expand and find out as much as we can about this phishing campaign and see if we could unravel the campaign in its entirety. We pivoted on both the MX and Nameserver IPs listed across the domains we found in pDNS and were able to uncover an additional 203 domains. From there, we filtered domains on a blocklist and those that were inactive which resulted in a total of 75 currently active domains in this campaign. Running some analysis on those domains we could see that only in-use domains for active phishing were pointed to a specific nameserver at lion[.]hvt[.]li and simba[.]hvt[.]li. This gives us a final list of active phishing domains to block.
Summary
This search narrows us to 18 domains that are actively being used to target UK telecom customers. Those currently active domains look to be targeting specifically EE customers as of the time of this writing in February of 2020, but that is subject to change. Active domains are switched to the hvt[.]li nameservers during the campaign then switched off afterward. They all share one of the few IP addresses. This makes them relatively easy to track their evolution in Iris Investigate. Included below is the Iris search hash that will allow investigators and responders to query these specific parameters to get a constantly updated list of active phishing domains for this campaign through the Iris API.
Iris Investigate search hash:
U2FsdGVkX1/H+rTuMIMCymT2QrD1gnvKPJlKJBsxzq8Ws9C3H6vQHOVYVZNWhQBLMg1noYkRFmjJOaZx8/GOmkMSTc9CrUc6p88gldxGWDkzj7r6kJzGigRZOHi/3mH5iqZjxE09Vz8Rk6S+qLI+VpcT+G7/VhmL3LCjC58xyjW5bKA/sRvEtQh/cihmMZwHivQYWPhAX/PGsI2h3FMLiDDF1jTX+flvdK3IbRZvn/3gLztTx0OTnZ19y0RRdBscm1yJeN7dSU+dpyIRbLXQrQU+1VGgm2zuLLtwCT92ydgOIyDWRg2cfphJWJBHWrLsKuZGV/aqrHSqT4+HTRa9C3rQm1xeC6ySkMiwHexGv7wud0Txcc5yhV5ZRWy3fWx1u6BmQdXw0TBIbBpERb+y/zHsYaiVGOOPzsJBfn1IO8RJBZsdf0BUhcNHfBcXT8HhoJZw3IRu3q5ptafTIV2WX6LEFesVE9Sy9xRMyRULcwY+bL3SgKMqEIolUerUiWDBTCmOinRjc31Ca/sgZlkVroathBZdiiARE/kpsAt0slBoDpuBdra7BQq7u1E+r6rgknVm/2u84W/sTR+8DfTxUYYWBWtpBcgqnoNEdOrXTNTRDUzH7ehF02st5Nu2Uw/Yk+bzgd4a/zo8JFa+M3BIMMUfYxPrDWCpMLpNsWaAFQSj8Sp2NcoB5Qy5Aqa5uk1/L4ndAu6cwAgjGLlgABSPMmWLzATK2e1GqJ//Sa6gp7Erm+nni6cprJBcLnIL7Lx7