Up to Your Gills in Phishing Attacks? This Research May Help.
NOTE: Iris Detect has supplanted PhishEye, with dramatically expanded capabilities. Please explore Detect for your brand protection, anti-fraud, and spoof infrastructure analysis needs.
Phishing activity is at an all-time high, causing significant financial and brand damage. In fact, (just in case you don’t have the numbers handy!) fake website and phishing scams cost the average-sized organization nearly $4 million annually, according to a recent report by the Ponemon Institute. What’s more, the Anti-Phishing Working Group (APWG) observed 466,065 unique phishing sites in the second quarter of 2016 alone, up 61 percent over the previous quarter and almost three times the number observed in the fourth quarter of 2015. With phishing attacks showing no signs of slowing down, proactive monitoring solutions which leverage DNS data have never been more necessary for organizations of all sizes and industries.
Two industries that are exceptionally vulnerable to phishing attacks are financial services and retail. These two verticals house large databases of valuable user information that act as potential gold mines for hackers. With this in mind, we leveraged our phishing detection solution, PhishEye, to explore malicious domain spoofing amongst the top financial and retail institutions and brands.
Species of Phish
Before we dive into the research, let’s cast a wide net to understand some of the phishing techniques and tactics that were likely utilized in the campaigns exposed by PhishEye. While most phishers won’t be able to register the primary domain names of their intended targets (unless the victim organization accidentally let a valuable domain lapse), they can and do register an almost limitless variety of look-alikes. If you consider the number of possible variations on a given term, and then multiply that number by the more than 1,000 top level domains, you begin to see just how large an ocean these phish swim in.
Cybersquatting
Also known as domain squatting, cybersquatting is the act of registering a domain name with the purpose of getting monetary benefit from a trademark that belongs to someone else. These look-alike domains are often used to trick victims into handing over personal data and credentials. The hacker can redirect the victim to various kinds of scams including pay-per-click ads (often for services from the victim company’s competitors), for-profit survey sites and affiliate program abuse, or more nefarious content like ransomware or other forms of drive-by malware.
One of the more popular ways to generate phishing domains is to add certain words (called affixes) like “account,” “login,” “online,” or countless others to the domain names, in order to make the victims believe they are either visiting the legitimate site or receiving a trusted email. Adding affixes has the advantage (to the phisher) of allowing them to spell the victim organization’s name correctly. For example, the (fictional) Acme Grommet Company may have registered acmegrommet.com but never registered acmegrommet-login.com, leaving it available to potential phishers. While people are getting better at spotting obvious character substitutions such as acmegr0mmet.com, they don’t usually have a handy list of which affix-enabled domains a large brand may actually control, to check against. Add to that the fact that phishers are becoming extremely adept at “scraping” code from legitimate sites so that the spoof is a virtual carbon copy of the original, and it can become genuinely tricky to tell the bad domains from the good.
Nonetheless, it may be useful to get acquainted with this list of identifying characteristics (which is representative but not exhaustive):
- Extra added letters in the domain, such as Yahooo[.]com
- Dashes in the domain name, such as Domain-tools[.]com
- The letters ‘rn’ disguised as an ‘m’, such as modem.com versus modern.com
- Reversed letters, such as Domiantools[.]com
- Plural or singular forms of the domain, such as Domaintool[.]com
DomainTools Research and Methodology
As I mentioned previously, one way to combat phishing attacks on your organization is by proactively monitoring for phishy domain name registrations. For research on top financial and retail brands, we used PhishEye’s proprietary algorithms to identify and surface some examples that are targeting large corporations (and those corporations’ customers).
From the 27th – 31st March 2017, the DomainTools Research team monitored the top UK-based banks and US-based retailers for high risk domains spoofing the respective banks and retailers. The domains identified as “high risk” are domains that received DomainTools Reputation Engine scores of 70 or higher. Scores in that range indicate that the domains are closely connected to other domains that have already been included on an industry blocklist for spam, malware, or phishing. We indicate how many high-risk domains we discovered during the monitoring period for each brand, and show a few examples to give an idea of how the phishers are constructing the domains. Remember: these aren’t the numbers of all-time existing domains spoofing these brands – you’re seeing the results of just a few days’ worth of new registrations.
Financial Services: The DomainTools research team analyzed domains mimicking the UK-based brands Barclays, HSBC, Natwest, Lloyd’s and Standard Chartered. By simply entering a keyword (such as “barclays”), PhishEye finds existing domains that abuse the keyword, and initiates a monitor that finds new spoofs as they are registered. In total, there were 324 domains identified as high risk that spoofed the banks’ brand names. Examples include:
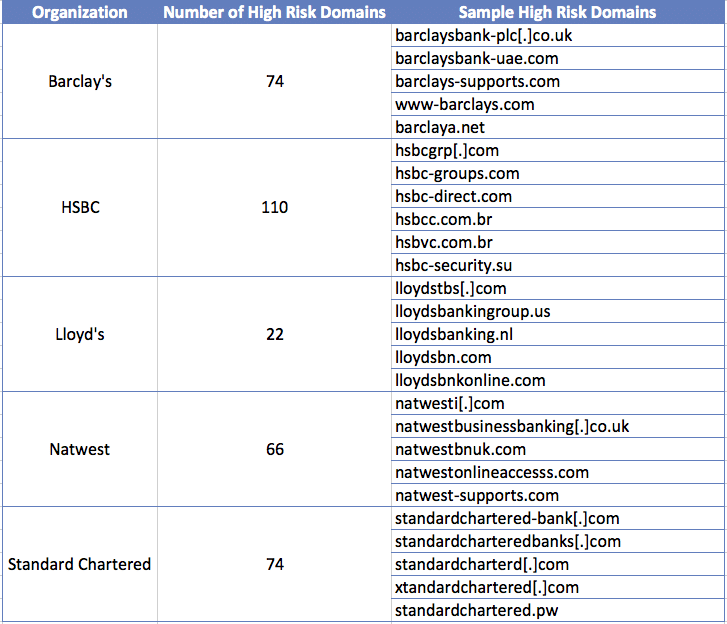
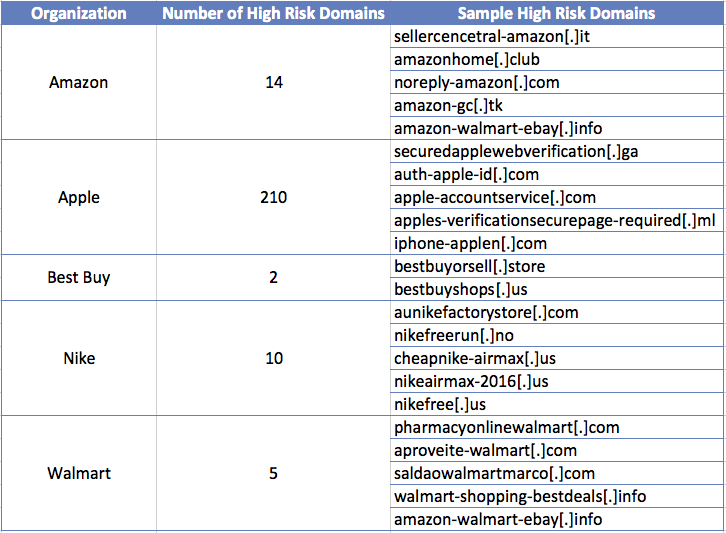
Retail: In the retail realm, the DomainTools research team dug into domains impersonating the top US-based retailers including Amazon, Apple, Best Buy, Nike and Walmart. While the volume of net new spoofed domains differed across retailers, Apple was the number one most mimicked retailer. In total, PhishEye uncovered 241 domains with risk scores in the danger zone (cue Kenny Loggins…). Examples include:
How can you defend your organization against phishing attacks?
Minding the “phishing gap” is no walk in the park. Phishing is an alluring attack vector for malicious actors because it exploits the trust that well-known brands have established with consumers. The bottom line is that organizations need to continue to not only invest in training for employees, but in a proactive security model to help avoid potential phishing attacks. Those companies that have fought brand abuse most effectively have built a chain of processes to protect themselves. They have iron-clad corporate domain control protocols. Many have taken to defensively registering their own typo variants and searching for other existing domains that contain their brand name. It is much better to own your own typo domains than to leave them available to someone else. At an average of £12/$19 per year per domain, this is a relatively cheap insurance policy. To fight phishing, companies have implemented domain monitoring that reviews all new domain registrations that match or typo their brands, and they have also invested in employee training.




