Warzone 1.0 RAT Analysis Report

Abstract
The cybercrime space has been evolving into a profitable area for several years. Malware authors now commonly sell malware as a service, dramatically reducing the technical barrier-to-entry for criminals to have those capabilities. One of the more popular pieces of malware for sale are RAT’s (Remote Access Trojan), including the Warzone RAT. It has a rich set of functionality and offers a low cost point with it’s monthly subscription rates.
In this report, I will go over analyzing the capabilities and features of the Warzone 1.0 RAT that was recently cracked and released to the public on a popular hacker forum as well as different open-source communities. My goal is to educate defenders on how Warzone 1.0 operates so they ensure they have security controls to detect and respond to it.
Contents
Introduction – 0x1
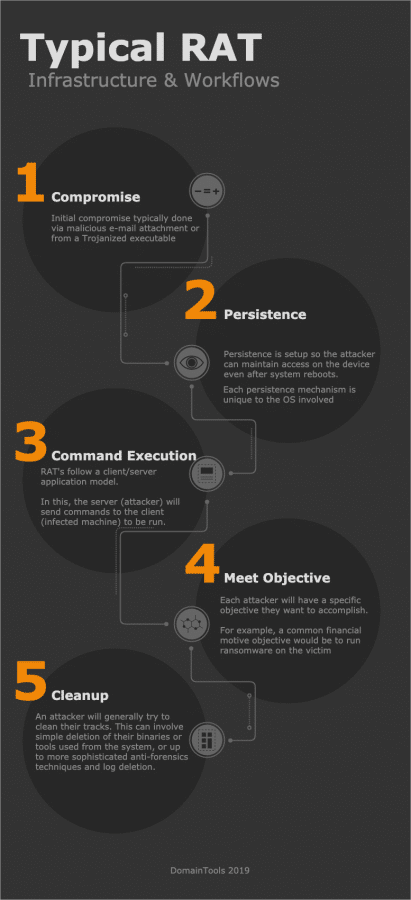
RAT’s are a type of malware that provides a common set of capabilities to an attacker. These generally are similar across all RAT types and variants: keystroke logging, reverse shells, file management (uploading/downloading of files), generally RDP access, screenshot capturing and often webcam access.
The Warzone RAT is a commercial tool for sale (https://warzone[.]io/), written in C++ and is compatible with the Windows operating system platforms. This would be for Windows XP all the way to Windows 10, both 32-bit and 64-bit. At the time of this writing, Warzone is catered towards only Windows machines.
General Information – 0x2
The Warzone commercial RAT is for sale and has a monthly price structure for access to the license to operate it. The latest version is 2.20. In approximately April of 2019, version 1.0 of the Warzone RAT was cracked by an individual with the alias of ‘CrackedXakFor.Net’, who is also known as ‘XakForNet’. ‘XaxForNet’ is a popular and public software cracker, with their own dedicated YouTube channel and forums.
Since Warzone 1.0 is now considered publicly available, I will cover the process of analyzing the RAT and it’s capabilities. From there, I will review the means to detect and mitigate Warzone 1.0 in your environment.
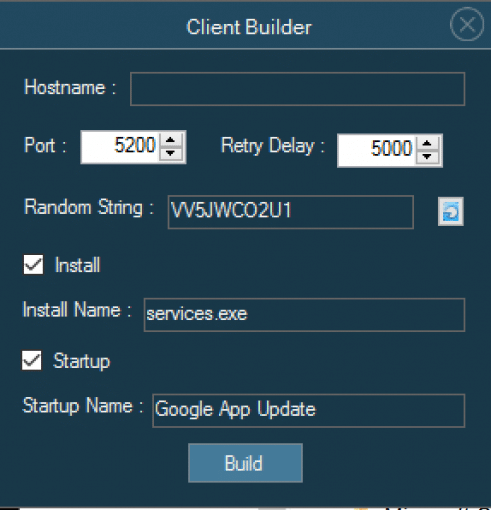
Building Warzone – 0.2a
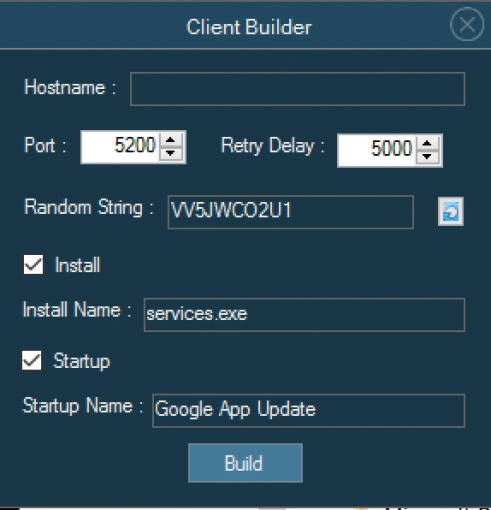
Warzone 1.0’s Command and Control console provides the attacker with several options, one of which is building out ‘clients’. The Warzone client built here has some limited configuration options.
The C&C (Command and Control) server’s listening TCP port (default: 5200), the domain or IP address of the server, as well as the time delay in re-establishing a TCP socket connection are the only networking based values you can change. If you want to setup a network proxy configuration, you will have to do it on the server-side.
Interestingly, there are no options to adjust the protocol or add any encryption in networking communication. Just straight up TCP sockets.
Warzone does offer some basic non-networking configuration options, like defining the executable name and the Windows registry run key used to establish persistence on the victim’s machine.
Unfortunately (or fortunately depending on your perspective), Warzone 1.0’s builder does not come with any options to pack or encrypt the executable that gets built.
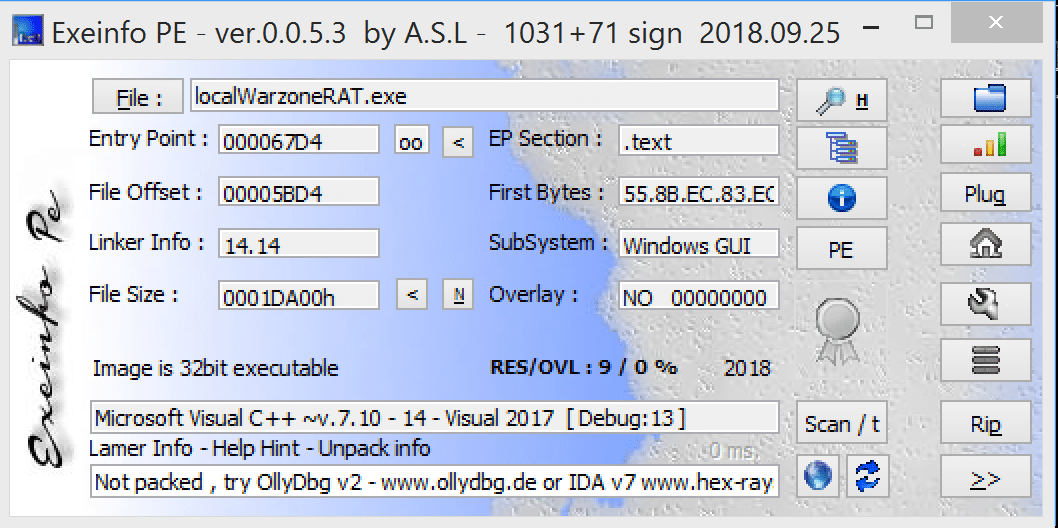
Most decently sophisticated attackers will understand why that’s an issue and look towards a paid packer or crypter service. Attackers that are on the lower side of the sophistication spectrum would likely build the client and not attempt to use a crypter or a packer, which would increase the odds of being detected by anti-malware solutions tremendously.
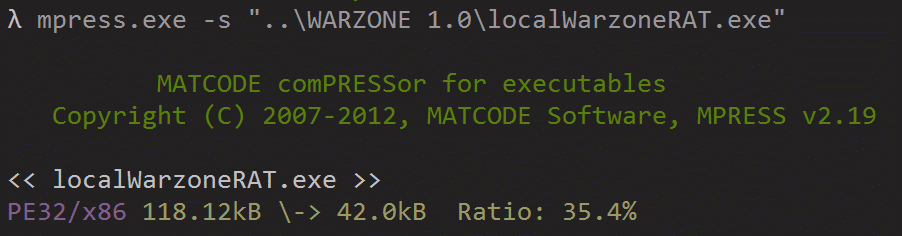
You can see that using a free packer like MPRESS benefits the attacker including reducing the size of the executable as well as making it relatively resilient against some static analysis techniques. A smaller executable size will help out when used in Trojanizing applications or being injected into a malicious document file.
Without being packed, it’s pretty trivial for automated systems (and humans) to glean the capabilities of the Warzone RAT. Below you can see some strings output, and we can see VNC, file manipulation and remote shell functionality.
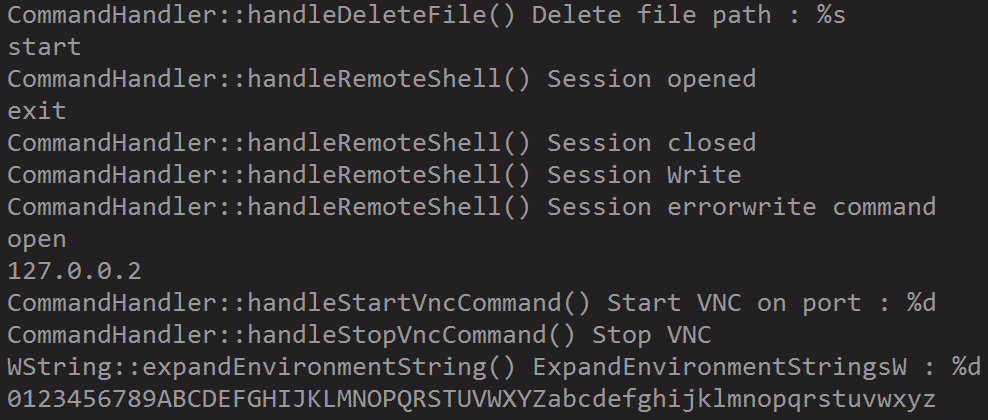
The folks at FireEye have contributed a lot of great open source tools to the security community, and I’m going to take a second to showcase their newly released tool StringSifter.
I really like this tool. Below you can see the output of StringSifter with the options of ranking the strings and showing me only the top 20.
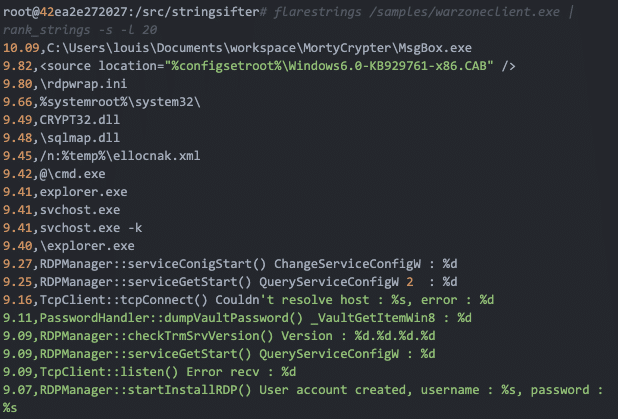
We can glean a lot of capabilities of Warzone 1.0 quickly leveraging StringSifter, as opposed to standard strings output.Packing Warzone is not that effective when put up against more sophisticated anti-malware vendors. Warzone’s client file packed with the MPRESS packer gives a 33/68 detections on VirusTotal which is not that effective.
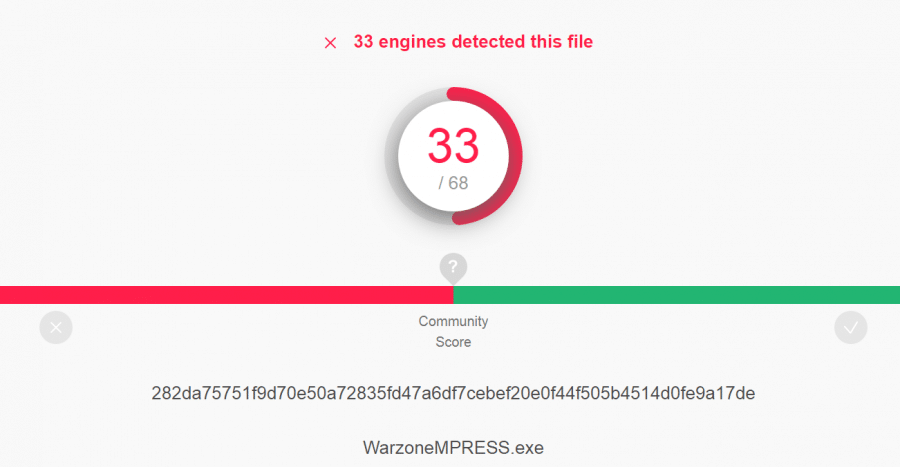
The goal here for the attacker is to make the Warzone binary as close to FUD (Fully Undetectable) as possible amongst malware analysis vendors. And to do that against a moderately sophisticated target, an attacker will likely have to use a closed-source crypter service against the Warzone RAT stub.
Windows Defender with Cloud-Protection enabled was still able to detect a packed Warzone run through a free crypter service. Interestingly, Defender was not able to detect it locally without the Cloud-Protection service enabled.
Any good business will see a demand from their customers and provide a solution, Warzone’s author is no different.

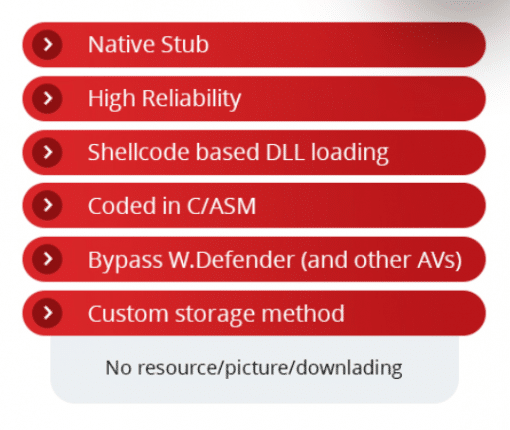
Warzone’s author provides a dedicated Crypter that claims it can bypass Windows Defender and other AV’s.
I would imagine this would continue to be relatively true until the crypter gets leaked or detection signatures/mechanisms improve.
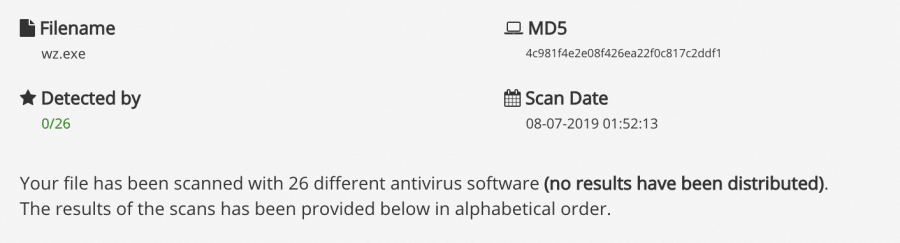
One member on a hacker forum mentioned that the latest version of the Warzone Crypter (as of 06-2019) was detected by ‘AntiScan.me’ with a 7/26 ratio. Although, with a continual goal of staying FUD (Fully UnDetectable) and financially profitable, Warzone’s author makes changes to the crypter service to stay ahead of malware detection services. You can see below a screenshot as of ‘08-2019’ showing this.
Capabilities & Techniques Overview – 0x3
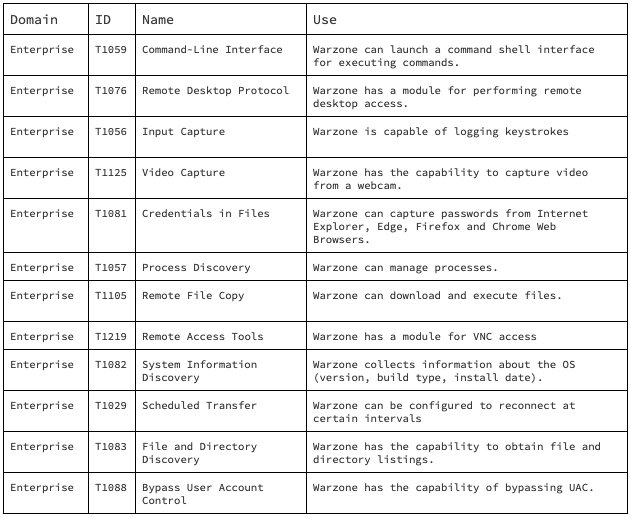
I’ll discuss the capabilities of the Warzone 1.0 RAT in relation to the MITRE ATT&CK matrix.
Warzone 1.0 Capabilities & Techniques ATT&CK Matrix
Behavioral Analysis – 0x4
Warzone 1.0’s client that gets built from the console has its core functionality executable as an embedded PE (with another embedded PE in that one) in the resources section of the binary.
Examining the resource section of the Warzone binary with Resource Hacker, it was simple to detect an additional binary embedded in it. The obvious hexadecimal representation for the magic of a Windows PE file is 4D5A.

We can see the infamous ASCII magic signature of “MZ” here. In addition, this executable contains another embedded executable.
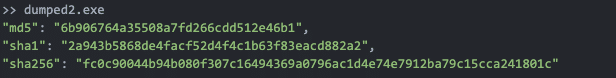
For namesake, I’ll refer to the Warzone embedded child PE’s as ‘dumped1’ (being the first one extracted) and ‘dumped2’ (being the second extracted) executables.
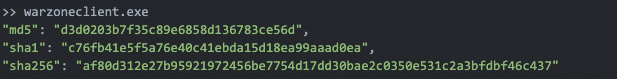
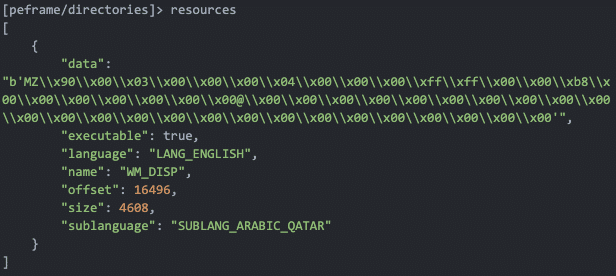
Warzone (‘warzoneclient.exe’ in this case) contains two embedded executables in resource section. You can alternatively use the Python ‘peframe’ package to inspect resource contents of an executable. You can see detecting an embedded executable here with ‘peframe’, once again noticing the infamous ‘MZ’ ASCII string in the data section.
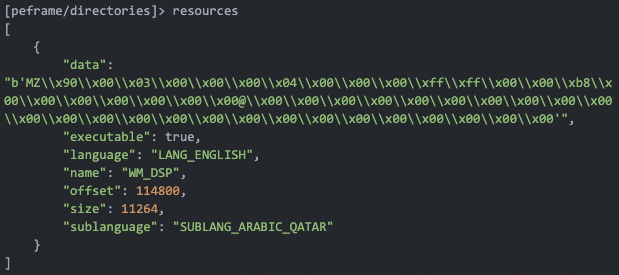
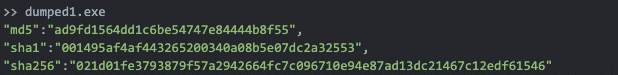
This is where the core functionality of each of the Warzone modules is contained. References to privilege escalation, keylogging, and all the other Warzone features are detected in this executable.
‘Dumped1.exe’ extracted from the initial Warzone stub client contains ‘dumped2.exe’ as an embedded resource.
Functionality such as file management is contained here, such as the ability to write itself to other paths.
‘Dumped2.exe’ appears to be the means for Warzone to inject/create itself into a new process and process management. Process32First, Process32Next, CreateProcess, TerminateProcess and CreateToolhelp32Snapshot functions are all called to do such from the executable.
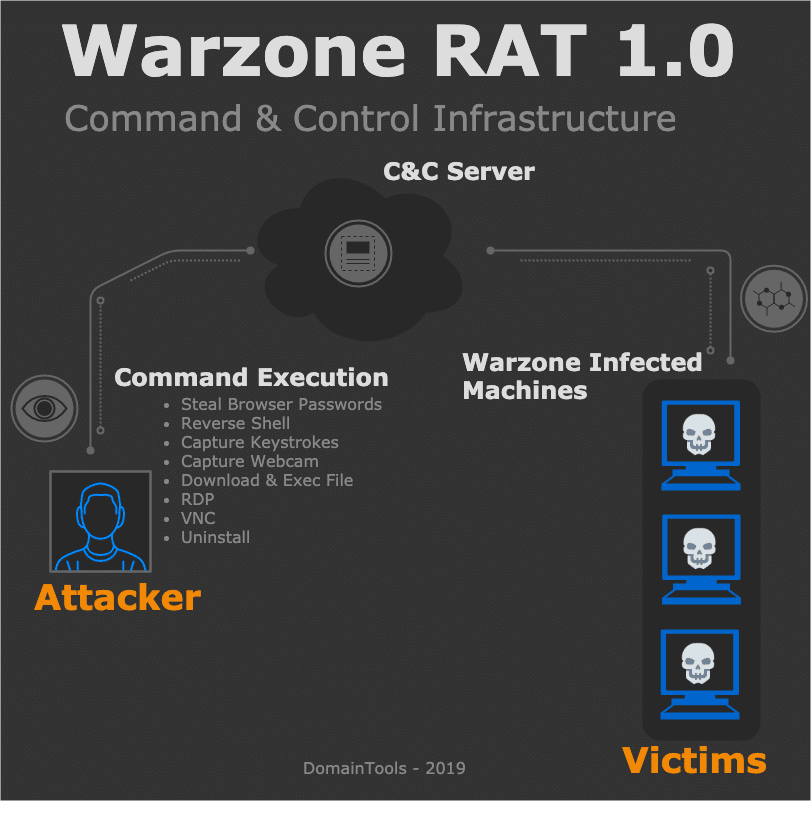
After Warzone 1.0 successfully executes on the victim, the attacker has the ability to perform file management capabilities. This includes the ability to download and delete files. This is one of the main data exfiltration methods that attackers using Warzone will leverage.
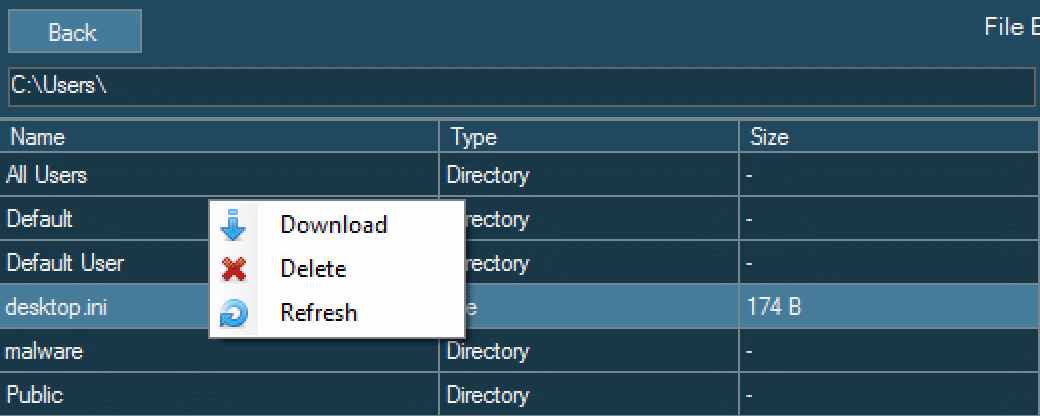
What does file transfer look like with Warzone from a network perspective?
After the TCP session with the Warzone C&C has been established, and the attacker sends the command to manage files on the victim machine we can glean what data is being accessed trivially. This is because Warzone 1.0 communicates over plaintext TCP sockets with no encryption.
Below is the hex & ASCII dump of opening the directory ‘C:ProgramData’ on a victim machine.
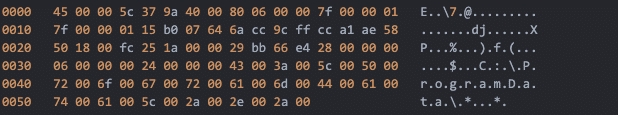
Downloading a copy of the 112KB Sysmon configuration file from my victim machine, the data payload in the TCP packet is completely inspectable and available for analysis.
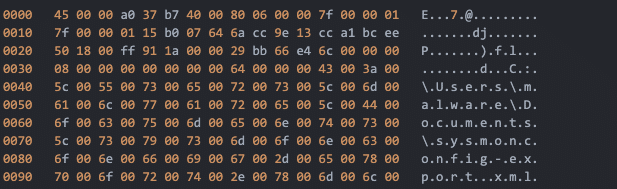
When an attacker using Warzone issues a command, it’s a pretty simple command shell child process that gets spawned from the copied Warzone executable (‘services.exe’).
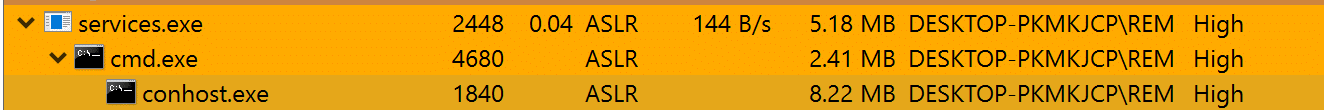
Monitoring API calls made by the Warzone client, we can see various commands being sent/received from the C&C over a TCP socket connection.
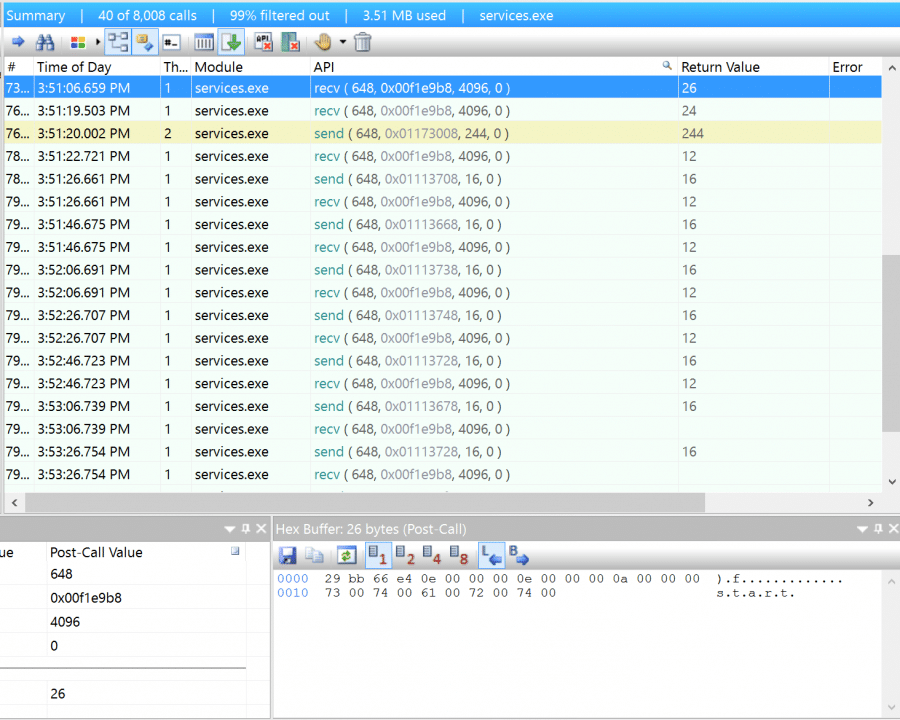
Since command execution is all done via TCP sockets, it’s trivial to inspect commands going back and forth between the attacker and victim. We can see the ‘start’ command and output, for example, in ASCII cleartext transmitted between the Warzone C&C and client.
Warzone also has the ability to act as a downloader for the attacker. It really depends on the attackers goals or motivations to determine how this would be leveraged. If an attacker is looking for financial gain, it would be very common to see ransomware be downloaded and executed on the victim through this channel.
These capabilities are something detectable thru static and behavioral analysis of Warzone.
Inspecting Warzone’s imports with PE-Bear, we can see the URLDownloadToFileW function being imported from the urlmon DLL, and ShellExecute from Shell32.dll.
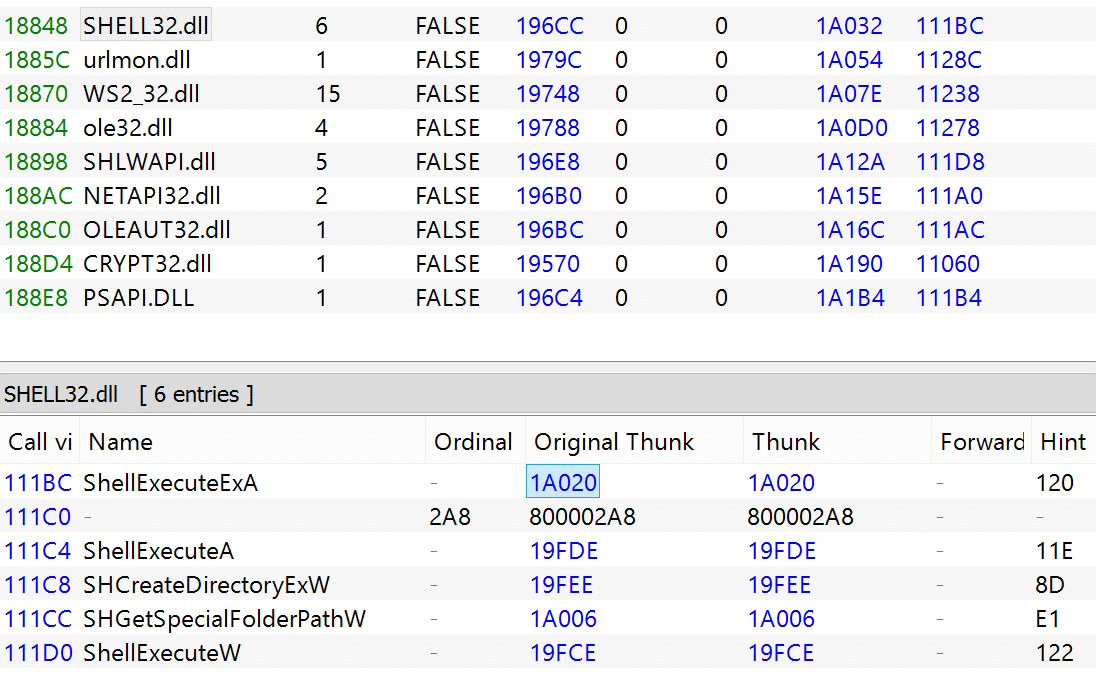
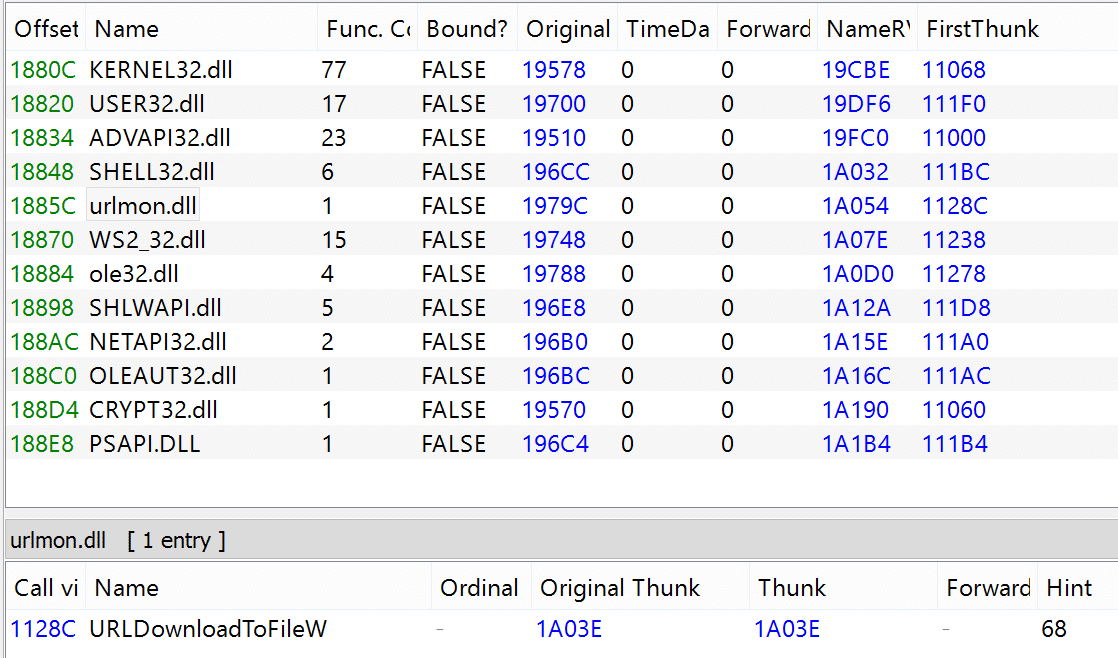
Seeing these two being imported on a malicious binary is usually highly indicative of dropper capabilities.
We can see an overall execution flow for Warzone with this diagram combining registry, process, file creation and networking information.
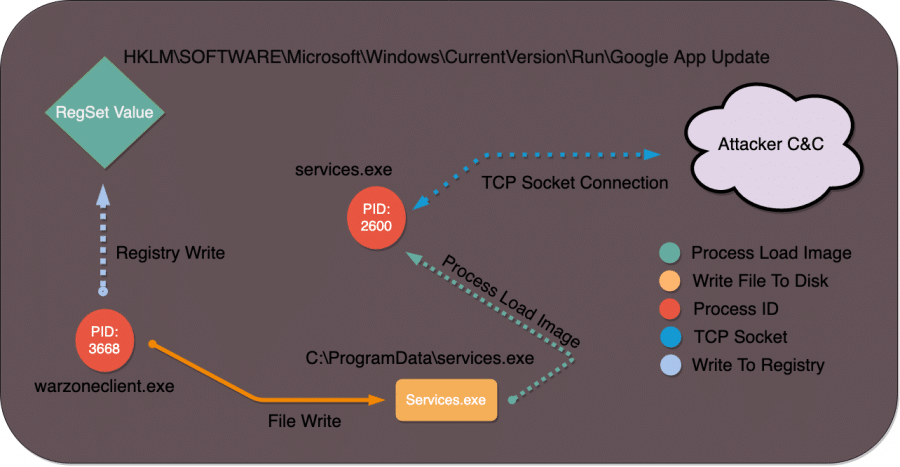
Upon initial launch of the Warzone client (‘warzoneclient.exe’), we can discern several things.
First, we see that Warzone uses the value used by the server when building the client for it’s persistence mechanism, the Windows Registry run key name value. In this case, the default is ‘Google App Update’. It’s common for attackers to choose benign sounding name values for different persistence mechanisms, and the default value for Warzone is no exception.
The value for the executable to be called from the Windows Registry run key value follows the name given by the Warzone builder. After Warzone establishes a persistence means, it then copies itself to a different directory under the executable name declared in the builder.
An interesting value that isn’t an option for the default Warzone builder is the location where the Warzone executable gets copied to.
I noticed that there were at least two common paths: ‘C:ProgramData’ and ‘%HOME%AppDataRoaming’. Both of these paths have their own purpose, ‘C:ProgramData’ being a location for non-user specific application data and the other not.
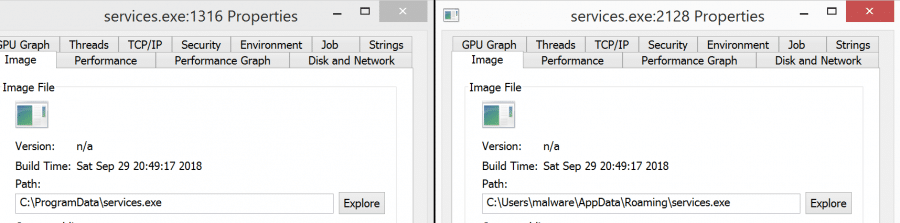
Essentially, each time Windows is started Warzone’s executable will be run thus ensuring the attacker can maintain control of the machine.
From a networking behavioral perspective, Warzone 1.0 is extremely simple.
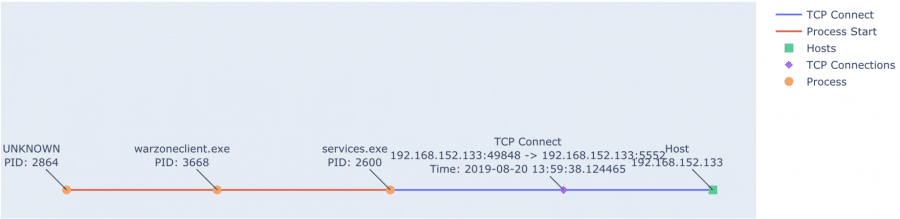
We can see the Warzone client (‘warzoneclient.exe’) process start and copy itself to a new process that gets executed. From there, a TCP session is established with the C&C server (in this case, my server ‘192.168.152.133’).
Warzone 1.0 builder does not offer the option to route network traffic over a proxy, or to choose a different networking protocol.
When it comes to Warzone’s credential stealing capabilities, we can glean how that is done several ways. One method is looking at the import table of the Warzone binary.

We can make out that the Windows Credential Vault DLL being declared, in addition to the common functions used to interact with it. The Vault DLL being declared, and those functions imported from it, are the means that Warzone enumerates and steals a users saved credentials. These credentials stores are for all common Web Browsers, such as Firefox, Google Chrome and Internet Explorer/Edge.
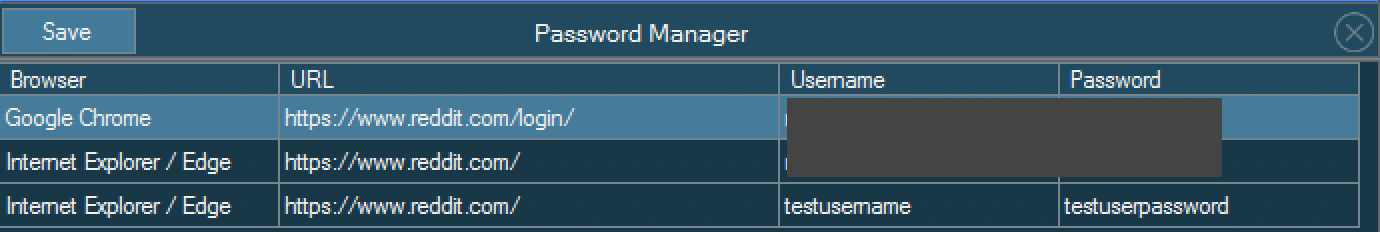
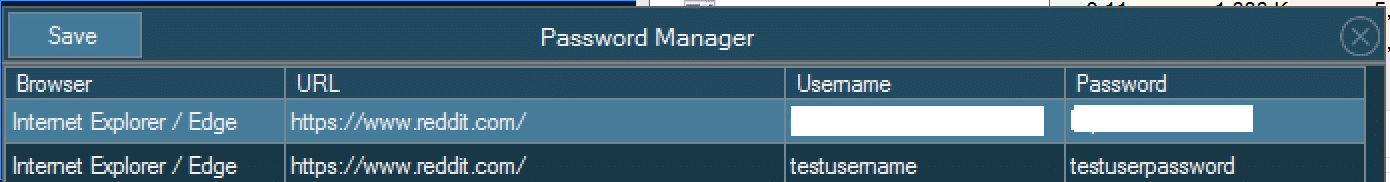
The attacker can send commands to remove itself from an infected machine. Once the command is delivered to the victim, Warzone is very straightforward on it’s removal.

Warzone begins by querying the Windows Registry where it declared it’s persistence values (“HKCUSoftware…RunGoogle App Update”) and the Warzone client, and removes them.

It’s interesting to note that Warzone 1.0 doesn’t actually delete itself from the infected machine, but only removes it’s persistence mechanism. That may or may not be intentional by the Warzone author. From a defender perspective, the more artifacts that are left behind the better evidence we have to understand the compromise. From an attacker perspective, it’s not a good idea to leave the executable on the machine since analysis on the Warzone artifact can lead back to your C&C infrastructure.
Warzone does not offer any anti-forensics capabilities either. Therefore, from a forensics perspective it’s trivial to detect all of Warzone 1.0’s operations when building a forensic timeline from NTFS file system artifacts.
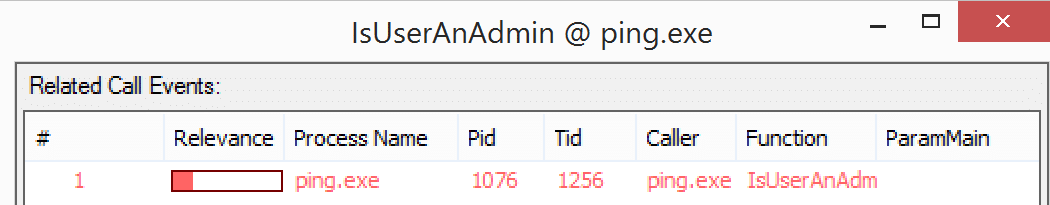
Warzone 1.0 also has privilege escalation capabilities. When monitoring Warzone’s behavior, it was observed that the Warzone process (‘warzoneclient.exe’) attempts to check if its able to escalate to an Administrator. If not, Warzone spawns the ‘ping.exe’ process to call the ‘IsUserAnAdm’ function. This function is a wrapper for CheckTokenMembership and is used to call directly to determine Administrator group status.

Analyzing the Warzone 1.0 clients build from the cracked console I’ve noticed there aren’t any other matches with known Ave Maria YARA rules or signatures. Warzone 1.0 can occasionally get misattributed to the Ave Maria ransomware malware, and that’s because of code “reuse” from Ave Maria to Warzone.
Specifically, with the string:

In part 2 of my Warzone write up, I’ll discuss different techniques on how to detect and mitigate Warzone in your environment.

