We need an American Girl who bolsters cybersecurity
Share this entry
While we are late to this meme trend, the sentiment remains the same as we’ll share in this article.
As described in our Best Practices Guide, the retail sector often faces threats that rely on fraudulent domains imitating a retail company’s name and associated brands. Retail brands need to be proactive regarding this type of activity for several reasons:
- Regularly monitoring your brand’s intellectual property (IP) protects your organization in multiple ways including market differentiation and competitive advantage, the ability to attract investors and partners, international expansion, and more. Adhering to this practice ensures your organization can continue to grow and foster new innovations without the fear of easy replication of the product along with ensuring legal recourse is possible if needed.
- Bad actors can use spoofed domains for fraud or diversion of revenue from their target. If the victim already spent their money with the spoofed domain, they may not have the funds to course-correct and shop with a legitimate brand.
- Too many spoofed domains can erode the trust customers and prospective customers have with your brand. If a brand isn’t proactive in taking down these spoofed websites and protecting their trademarks, they’re effectively leaving their fans vulnerable.
Spoof There It Is: An Example of a Spoofed Domain in Retail
There are a number of ways to monitor your brand, but the scenario I’m about to lay out begins in the wild on a fan subreddit. As a backstory, I am a big fan of the American Girl (AG) brand, and I don’t know how much the worlds of Information Security (infosec) and AG overlap, but you can bet when I was recently scrolling through r/americangirl, I was intrigued to see the following post:
With the reignited nostalgia for American Girl since the start of the pandemic, not to mention its popularity as fodder for Saturday Night Live, adult fans of the brand have unabashedly revisited their youth, hauling out boxes from their parents’ attics, refurbishing old dolls to their former glory, and scouring the Internet for retired or discontinued items. This can be a timely and costly endeavor, so when you’re able to find that rare item AND at an affordable price, it may seem too good to be true. Unfortunately, that old adage is a cliché for a reason.
I took a look at the website in question and at the time of my inquiry, the homepage looked like this:
A few initial indicators of possible malfeasance include the domain “USGirlShop” masquerading as AG (i.e. using the AG logo – a slightly older logo at that) along with verbiage claiming exclusivity on a coveted discontinued item. Other indicators include minor misspellings, odd spacing, and that ampersand code in the navigation bar. Personally, I wouldn’t feel comfortable sharing personally identifiable information (PII) or my credit card information with this website, and luckily the advice from others in this subreddit aligned with my feelings. I wanted to learn more, so I looked in Iris Investigate to see what else I could find.
Protecting Your Retail Brand Using DNS
usgirlshop[.]com has a proximity score of 100, and the highest of these four scores in the image above gives you the Overall Score. But backing up slightly, the Proximity score uses an algorithm to look at how a given domain is related to known blocklisted domains (i.e. its proximity to known maliciousness). A score of 100 generally indicates that the domain has been blocklisted by a reputable block list.
The domain was registered by a user out of China, with a Create Date of 8/12/22, but we would expect an established brand to have an older Create Date. As expected, if I use Iris to look at AG’s domain (americangirl[.]com) I can see that its Registrant is American Girl, LLC and the country of origin is the United States with a Create Date of 3/25/1997.
The user who registered usgirlshop[.]com has a few other potentially spoofed brands linked to them including two shoe stores and two women’s clothing boutiques.
Another interesting element is that the actor changed SSL certificates frequently. It’s common to see switches every three months for SSL certificates, but more than that is slightly questionable. In this case, the actor could be trying to avoid fingerprinting, or perhaps their website was taken down from one registrar requiring migration to another. It’s not indicative of anything by itself, but hopping from one SSL certificate to the next when they don’t need to update it is odd.
More indicators followed: it is not out of the realm of possibility, but the fact that usgirlshop[.]com utilized Cloudflare obfuscation from the beginning, including Cloudflare nameservers and Cloudflare-issued SSL certificates, raises concern. Rare is the independent retailer with either the need or the savvy to engage with Cloudflare from the beginning, whereas it can be a circumstantial indicator of criminal intent.
While Cloudflare hosting meant the IP address was shared among tens of thousands of other sites, pivoting off the Registrant of usgirlshop[.]com and narrowing the search down to sites that also shared Cloudflare protection (an easy task thanks to Iris Investigate’s Advanced Search functions) immediately surfaced another four websites engaged in either fraud, the sale of what appear to be counterfeit products, or both. This pivot also exposed that all five sites shared the same Create Date, adding another parallel campaign indicator to the emerging domain profile.
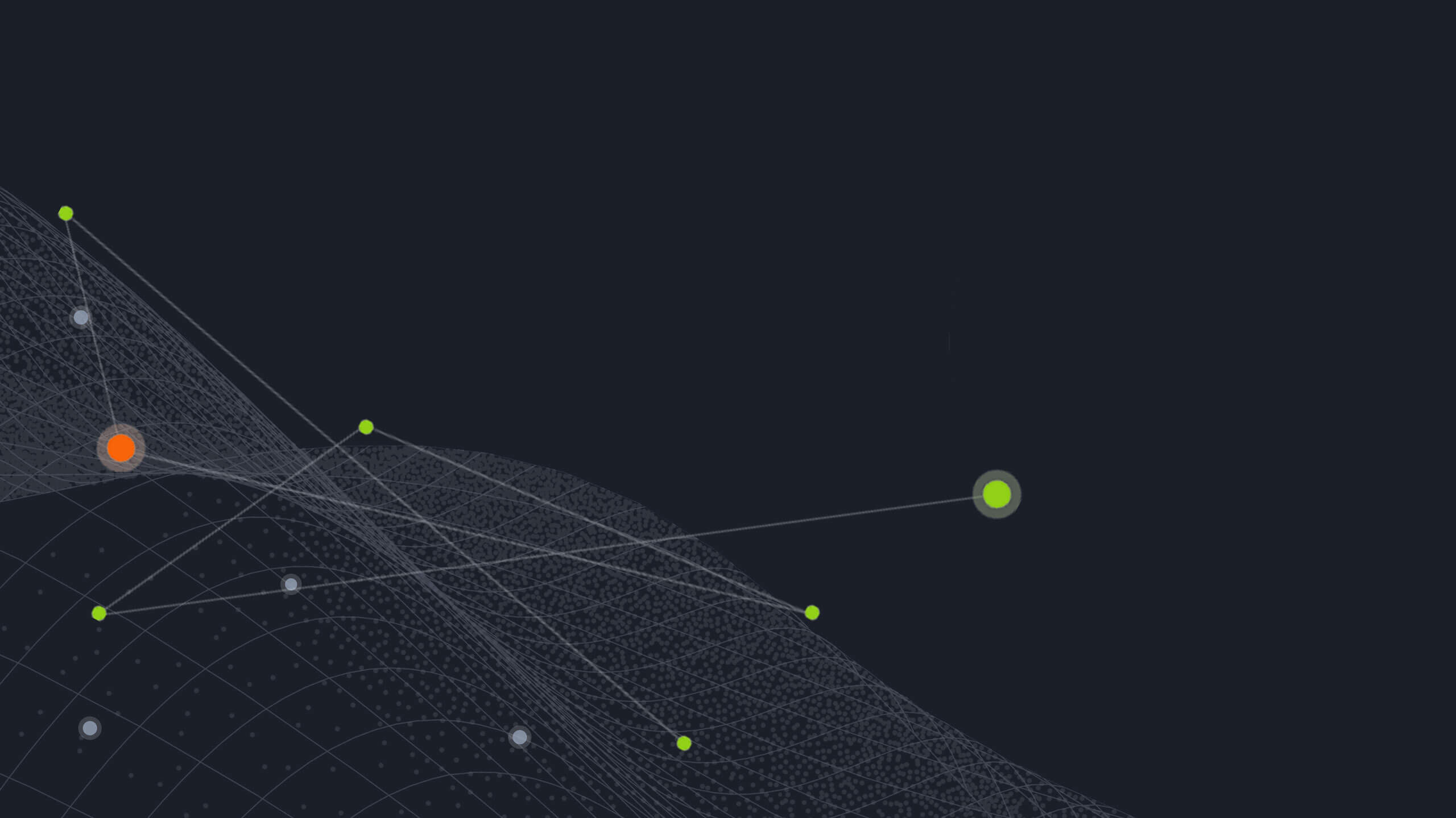
Iris Investigate’s Visualization function makes the interconnections more apparent:
Starting with one suspicious brand-infringing domain, I discovered four others within a few clicks, underscoring both the ease with which Iris allows for these investigations and the massive scale at which brand spoofing and infringement contribute to fraud in the online marketplace.
Conclusion
I shared this specific example because the AG brand is owned by Mattel, who also owns the Barbie brand. With the success seen in the Barbie movie, Mattel is unsurprisingly making more movies within their intellectual property, including Hot Wheels, Polly Pocket, Thomas & Friends, and you guessed it – American Girl. My hypothesis is that if movies on these beloved entities are as successful as Barbie, the drive for merchandise, both new and discontinued, will incentivize bad actors to spin up infrastructure for fraudulent or counterfeit purposes.
Even without the support of the film industry, retailers are targeted by malicious actors in an effort to commit fraud or divert revenue. Luckily, there are techniques brands can use to monitor their IP, which ensures customers receive the product requested at the quality they expected and that we in the industry are giving bad actors more bad days.