Coming up this week on Breaking Badness. Today we discuss: Will a $10M Bounty Be the Quicker Picker Upper of the DarkSide Gang?, Apple Patches the "Shrootless" Flaw, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Will a $10M Bounty Be the Quicker Picker Upper of the DarkSide Gang?
- DarkSide as a group was first noticed in August 2020. They’ve known to be looking particularly professional both in their website and the way they communicate. They also have attempted to partner with journalists and have done a number of interviews, trying to foster a type of Robin Hood image where they just target large corporations and refuse to attack schools, governments, and hospitals. Their most notable attack was probably the Colonial Pipeline which is why they’re getting targeted so heavily here by the Bureau. As a ransomware group they’re the typical affiliate program and their affiliates have been known to do quite a bit of living off the land, using local binaries trusted by the system to move around and operate. They also share quite a bit of code with the REvil or Sodinokibi ransomware variant so many have thought that DarkSide was a rebrand of REvil.
- They put up a wanted poster, and it’s quite a ridiculous one. The lock on the keyboard with all the cash on it. Should’ve at least thrown in a bitcoin or something to make it look slightly legitimate. Anyways, definitely an NFT of it floating around out there. They probably made it.
- These groups keep doing rebranding and as we saw in previous Bureau statements like we talked about last week the Bureau prides itself on its long, long memory. Eventually rebrandings aren’t going to help anymore and the deflection to a new group isn’t going to be easy for them. In any case, at the end of the day, the people writing the ransomware are highly unlikely to get caught if they play their opsec right and the only people at risk are the affiliates. If anything the ransomware game will dry up because they’ll run out of competent hackers if arrests start happening more frequently.
- The Transnational Organized Crime Rewards Program was started in 2013 and allows for up to $25 million in awards for qualified law enforcement objectives. The program is managed by the Department of State and allows for a number of law enforcement agencies within the United States to put up these awards whenever it involves international organized crime groups.
- People think it’s interesting that $10 million is also what we were offering for the capture of ISIL members. So we’re seeing a reward here that’s on par with how we view terrorist organizations. That in and of itself shows the financial implications here and how important this is to the current administration. As for whether or not arrests will happen, I think most people in the infosec industry are so burnt out dealing with these things that it’s hard for them to say anything positive. I’d agree with the feeling that there just isn’t going to be any meaningful change in this space until there is a change in the financial incentives for these ransomware groups. WHat that looks like, I just don’t know. I do know it would be less of a problem if companies just followed basic security advice like network segmentation though and quit dumping tons of money on new security products.
- I think there is a point where ransomware could see a labor shortage if enough affiliates get arrested, but these groups are smart and are probably already training up new groups of affiliates to take over for some that get arrested. Additionally they have to already be thinking of a post-ransomware world. The last evolution right was double-extortion—what’s their next evolution? I’m sure we’ll see as the ransomware space continues to firstly get more saturated and secondly if the long arm of government starts getting involved with more sanctions and arrests. All in all, I don’t think we’ll see much of an effect other than a migration to new techniques and better opsec. That’s the cat and mouse game of offense and defense though.
Apple Patches the "Shrootless" Flaw
- Along with being realistic (they mentioned 3 other bypasses for SIP, after all), the MSFT team has a lot of OS X ground to cover between their application support, MS defender for Mac support, and their own internal users. Though I’m sure the marketing team is glad this isn't a Windows vulnerability.
- Back when they released Yosemite in 2014, they added some kernel level filesystem flags that prevent even root-level access to stuff like /system /usr / bin /var etc. These flags are stored in NVRAM and can only be changed on boot. System Integrity Protection is designed to allow modification of these protected parts only by processes that are signed by Apple and have special entitlements to write to system files, such as Apple software updates and Apple installers. They call this rootless… because the microsoft team got around this via some fun shell games they called their CVE ‘shrootless’.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
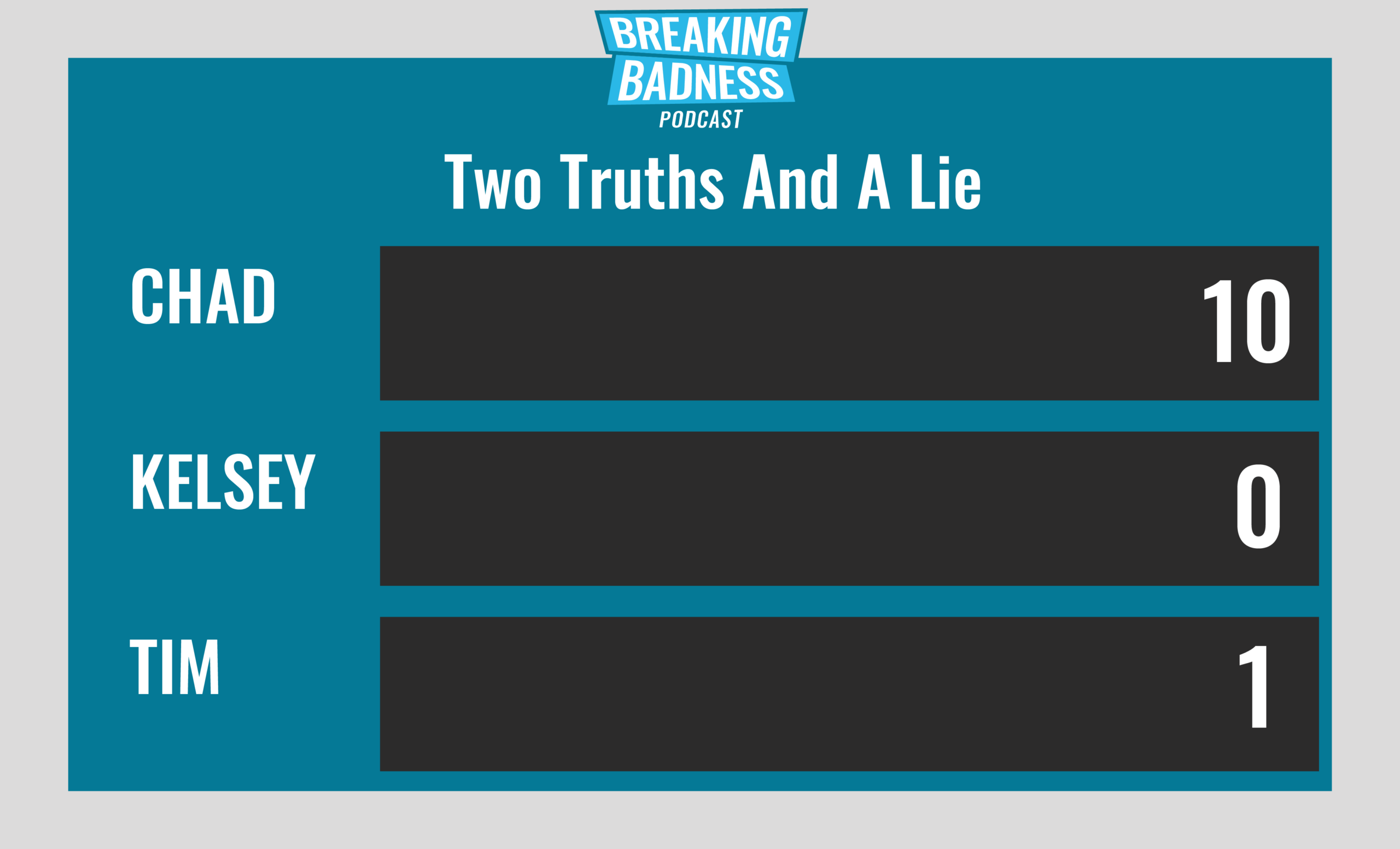
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Will a $10M Bounty Be the Quicker Picker Upper of the DarkSide Gang?[Chad]: 4.53/10 Hoodies[Taylor]: 4.5/10 Hoodies
Apple Patches the "Shrootless" Flaw[Chad]: 7/10 Hoodies[Taylor]: 7.sleeve/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

