Coming up this week on Breaking Badness. Today we discuss: BotenaGo On The Prowl, The QBot Thickens, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
BotenaGo On The Prowl
- The syntax of Go is sort of similar to C, but it has a lot of more “modern” features like static typing and run-time efficiency (like C), readability and usability (like Python or JavaScript), and high-performance networking and multiprocessing. Essentially, its creators got sick of C++ and created something better. Incidentally, its official name is “Go” rather than “Golang” but many people call it Golang because other people call it that and also because of its domain name. There are a few small projects you might have heard of that are written in Go, such as Docker, Kubernetes, and Terraform, and lots of popular services use it heavily, like this thing called Netflix which I think rents CD-ROMs or something, and Uber, and Twitch. So it’s safe to say it’s probably here to stay.
- BotenaGo is an interesting new botnet that is targeting the little things on the Internet, like IoT or Internet of Things devices and home routers. We’ll go into more detail about how it actually works in a moment, but as far as its discovery goes, credit there belongs to AT&T’s Alien Labs. (By way of background, a lot of folks may have forgotten that in 2018 AT&T purchased AlienVault and all that goes with it, like the Open Threat Exchange, or OTX. AT&T intentionally left AlienVault alone in large measure, so that’s part of why it’s easy to forget.) Anyway, this bot, written in Go, is a bit of a Swiss Army knife, with more than 30 different attack functions.
- BotenaGo basically sets up shop by mapping its various attack functions to the various vulnerable device types, and then it starts hitting local devices with GET requests, to pull back the server banner information that tells it if it has a targetable system. Now, what’s interesting about this report is that it seems that the way that it determines which victim IP addresses to target is interactive. It sets up listeners on backdoor ports, and then when it is given an IP to hit, it runs the exploit code that is appropriate to that victim device. And it can also run in a purely interactive mode where it’s listening for terminal commands. Why would it work this way? Good question!
- There’s reason to believe that this may be a beta version of the malware that has been leaked. Why? Well, in part because the payloads that could potentially be downloaded from C2 servers have all been removed by the malware creators. Also, the interactive nature of this malware naturally does not scale in any way. So it seems most likely that what we’re seeing is a piece of malware in development. Having said that, even though we have an excellent chance to potentially get ahead of it, I have the ominous feeling that Shodan won’t look all that different a month from now than it does today, in terms of numbers of vulnerable devices sitting out there waiting to be exploited.
- As you might expect, whenever you have a device with one of the vulnerabilities that are exploited by BotenaGo is presented directly to the Internet, it’s at major risk. And some Shodan searches will quickly reveal that there are many thousands of vulnerable devices out there. Also, as you’d probably expect, many of the CVEs that are associated with these exploits have been around for a while. In fact, the newest ones were from 2020, and the oldest from 2014. Most of them appear to be patched, but there’s at least one that I saw that affects devices that are EOL and no longer supported. Anyhow, from what I just described, you can probably surmise what the best fixes are: firewall yo’ stuff and patch yo’ stuff. If you spend any time at all with Shodan, it just sort of crushes your spirit because of how many devices are exposed directly to the Internet. Now of course some of these have to be exposed to the Internet: the routers. So no points off for those, but they do have to be patched. People should be familiar with the admin page for their home routers, and should regularly check for firmware updates. Some of them auto-update, some don’t. Take out your smartphone, pause the podcast, and set a calendar reminder to periodically check your router’s firmware! Then don’t forget to hit Play on the podcast again.
- The report from Alien also has a number of IOCs, so it’s not a terrible idea to do a little hunting on those in your network logs, if you for some reason have non-router type devices exposed to the Internet. There are a couple of hard-coded IP addresses in there that I would assume are going to get burned before long. And one IP doesn’t have any recent domains on it, according to passive DNS and the other has never had any domains at all. Those should be on VirusTotal soon if not already, and will make their way to various block lists. But I’m sure there are other IPs that will come and go for this botnet. See what I did there?
- According to Intezer, they say that they’ve seen malware code written in Go go up 2000% over the last few years, though of course there’s some law-of-small-numbers at play there. Still, one of the main explanations for the proliferation of Go-related malware is that it tends to be tricky for a lot of AV technologies to detect. So there’s a window of time, which we’re in right now, when it will be especially appealing to build malware in Go.
The QBot Thickens
- QBot (qakbot, quakbot) is malware, first discovered in 2009. It started as a Banking Trojan, stealing financial data, browser information/hooks, keystrokes, credentials, etc. Once deployed an actor can get a wide range of data from an endpoint, and can help persist an initial access as they wait for a good opportunity to strike.
- SquirrelWaffle is a recent malware loader that is distributed through malicious spam mail – with the purpose of infecting a device with second-stage malware such as cracked copies of the red teaming tool Cobalt Strike and QakBot, a well-known malware that started life as a simple banking trojan but has since evolved into a multi-functional framework with RAT (Remote Access Trojan)-like capabilities.
- SquirrelWaffle can provide threat actors with an initial foothold onto systems and their network environments that can then be used to facilitate further compromise or additional malware infections depending on how adversaries choose to attempt to monetize their access.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
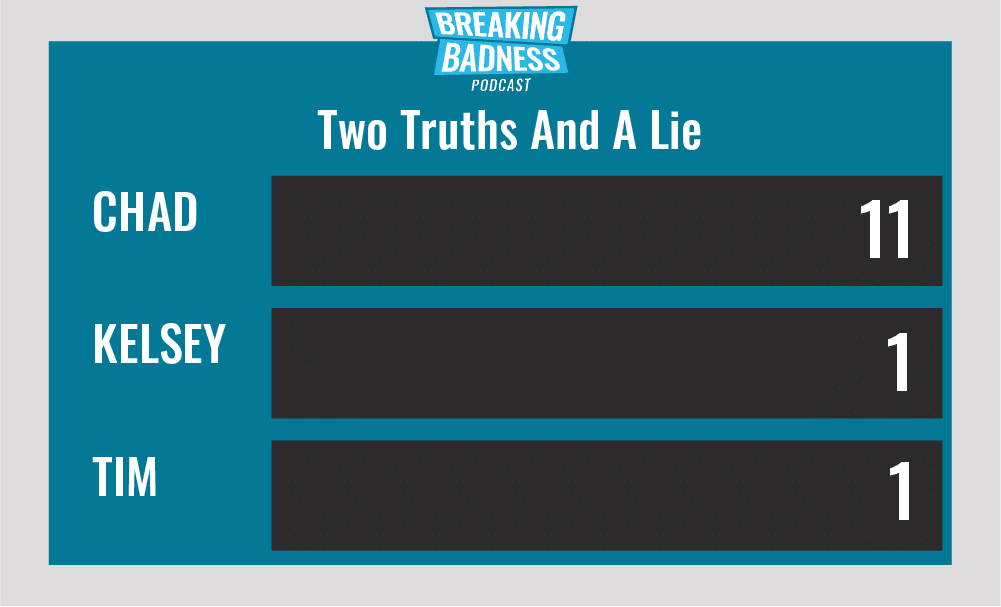
Current Scoreboard
This Week’s Hoodie/Goodie Scale
BotenaGo On The Prowl
[Taylor]: 4.3/10 Hoodies
[Tim]: 3.78/10 Hoodies
The QBot Thickens
[Taylor]: 7/10 Hoodies
[Tim]: 7.5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




