Coming up this week on Breaking Badness. Today we discuss: Good Cod! Another Spearphishing Campaign, You Reap What You Sow, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Good Cod! Another Spearphishing Campaign
- I monitor a number of oddities in VirusTotal with random sets of YARA rules. Whenever I discover a campaign I set up a YARA rule then another general one around it to surface any additional weird documents that may come into play. In this case the broader YARA rule was leftover from the Winter Vivern research we published about a year ago now that included some campaigns hitting the Vatican, Italy, Baltic States, and a host of others. When it first surfaced, the PDFs looked entirely innocuous since their only interesting feature was that they contained a URI object which is a link out to another bit of content. What stuck out as I saw many of these come in matching my rules is that each contained an email of a specific victim and all those victims turned out to be real people according to LinkedIn.
- Once I found the PDF, I threw it Into a virtual machine. I’m a big fan of the FLARE VM, fired up all the necessary telemetry, OpSec with that VPN to CYA, then poked at the site. Found that each one was down and that led me to wonder what Glitch was so I had to go sign up and do some learning there.
- Glitch is actually pretty cool but in its coolness is also a vector for attacks that’s seeing a lot more traction. Similar to Living Off the Land Binaries which make use of trusted system apps to do nefarious things there’s a bit now being called Living Off Trusted Sites which takes known, trusted sites that let a user run code and leverages that to phish or exploit users. In the case of Glitch they allow codespaces where users can run their own app, on Glitch’s services, for 5 minutes for free. It’s a cool concept, from the StackOverflow and FogCreek folks, but it’s super useful for nefarious purposes.
- Since each of these Glitch sites is ephemeral and lasts for five minutes, attackers can craft something, try and get a lure to work, then disappear. Glitch allows for account creation here with just an email address so it’s easy to anonymously host something like these credential spearphishing pages that mimic SharePoint in this campaign. It’s quick turnover and since Glitch is amongst trusted sites it will be unblocked by most corporate firewalls. There are plenty of legitimate uses for it amongst developers so it’s not like you can just blanket block the site and since the subdomains hosting these things last for only 5 minutes as well you can’t keep up with the whack-a-mole. A great situation for the aggressor in this case.
- SharePoint login claiming the file to be downloaded was some kind of important document. Once the credentials are entered it ships them off elsewhere and the site appears to redirect to the domain provided in the spearphishing target email. So if they were targeting Kelsey AT domaintools[.]com it would redirect to domaintools[.]com after entering any credentials. Does some other minor fancy footwork like claiming your password is too short if you type in garbage, things like that to make it seem a bit more real. Pretty run of the mill in the end though.
- If I looked for these campaigns more often as a goal I’d come across them daily. This Living Off Trusted Sites thing is becoming more and more common. Phishing campaigns for credential harvesting though are a daily occurrence if you know where to look and something that if you’re a defender I can guarantee you will find daily hitting your network. Spearphishing a little more rare since it’s targeted, but again a simple thing to look for if you hunt on potential targets in places like VirusTotal or in malspam repositories.
You Reap What You Sow
- We’re continuing to see some efforts to bring down the hammer of justice on various actors who participated in various forms of tampering with the 2020 election (not that they aren’t going after *all* US elections for anything above dogcatcher and maybe for that, too, but 2020 is obviously a big focus), and in this case the DOJ is indicting two Iranian nationals for a “cyber-enabled campaign to intimidate and influence American voters, and otherwise undermine voter confidence and sow discord, in connection with the 2020 U.S. Presidential election.” Familiar territory by this time, of course.
- They started off by probing and trying to gain access to eleven state election websites, and in one case they were able to get in and they proceeded to download information on around 100,000 voters.
- These suspects crafted a bunch of emails claiming that the Democratic party was going to “exploit ‘serious security vulnerabilities’” in various voting systems including “editing” vote-by-mail ballots, to tilt the election for Biden. These emails targeted Republican US Senators, House members, White House advisors, campaign officials, and members of the media. Oddly enough, it would appear that these emails, and others like them that undoubtedly were making the rounds at that time, were not dismissed by those officials as the obvious work of cranks.
- Probably the most infamous of their email campaigns, though, were the intimidation emails sent to thousands of registered Democrats, threatening them with strongly implied physical violence if they didn’t change their party affiliation and vote for Trump; and since the conspirators had obtained that voter information from the state whose infrastructure they infiltrated, they included these voters’ physical addresses, and stated that they had “all your information.” The news broke that this campaign was the work of Iranian actors a few months back, and this indictment is the continuation of that process.
- But the emails weren’t all. These indicted conspirators were masters of multimedia manipulation and made a vexatious video supposedly showing a pro-Biden hacker penetrating the perimeter of a vulnerable voter site, obtaining voter records, and fabricating fraudulent, bogus ballots by the bushelful. And it goes to show you just how much we’re living in the Upside Down that when they masqueraded this thing as the work of the Proud Boys, that also did not cause it to be dismissed out of hand as the work of cranks.
- These suspects were known to be contractors of an Iranian “cybersecurity company” (that’s in quotes on purpose, since the indictment uses that juicy hip hop word “purport,” and incidentally don’t you love how much carnage is sown in the name of “cybersecurity?”). These two individuals are reputed to have some 1337 h4x0r skillz.
- Well, as they say, money talks, and in this case, that would be a cool ten million real American dollars. That’s the reward the DOJ is offering for information on or about the activities of the two individuals, 24-year old Seyyed Mohammad Hosein Musa Kazemi and 27-year old Sajjad Kashian. That’s a pretty significant OSINT CTF challenge, no? So here’s hoping someone is able to claim that dough and get these two brought to justice.
- As far as how concerned I am as a citizen? I’m basically at DEFCON 2 or so. These misinformation, disinformation, and intimidation campaigns have been more effective than I could ever have imagined just a few years ago. I thought that people hated to be duped, but it turns out that about half of the country loves it, so Putin and the other architects of these campaigns are just living their best lives right now. It’s quite frankly terrifying.
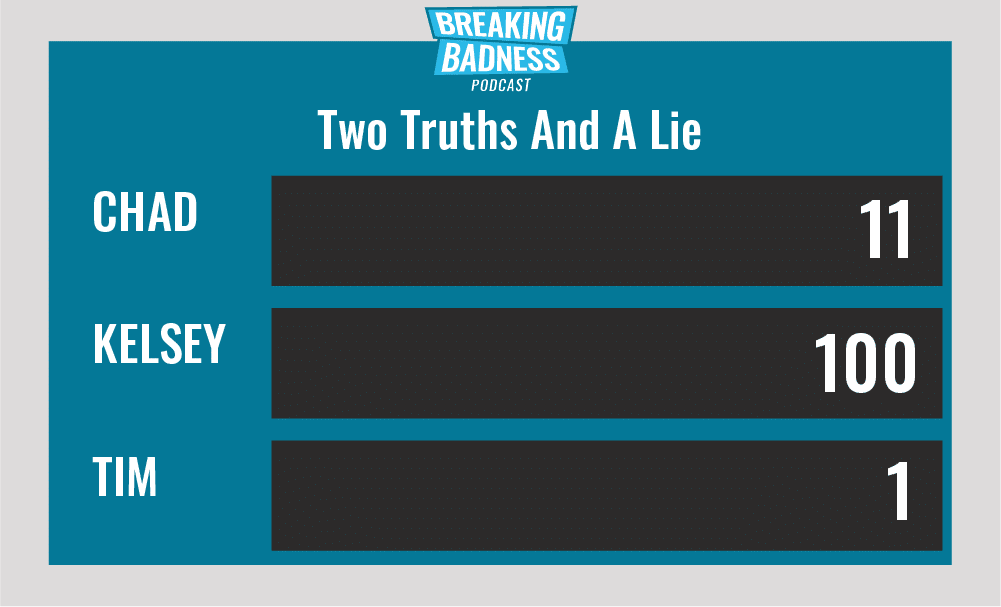
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Good Cod! Another Spearphishing Campaign
[Chad]: 5/10 Hoodies
[Tim]: 6/10 Hoodies
You Reap What You Sow
[Chad]: 5/10 Hoodies
[Tim]: 8/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




