Coming up this week on Breaking Badness. Today we discuss: Accounting for Propaganda, Ransom Where? Purported Extortion Results in Arrest, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Accounting for Propaganda
- When talking about disinformation with family members over the Thanksgiving vacation I noticed that most people are convinced that Russia is the only country doing these kinds of disinformation operations. While the Russian-state backed groups are prevalent this dump shows that Russia isn’t the only country paying organizations to run these operations for them. In fact we’ve got Mexico, China (of course), Tanzania, Uganda, and Venezuela.
- Accounts deleted by Twitter were mostly ones inauthentically amplifying state voices and objectives. This is what the Twitter research team really looks for and certainly we see multiple offenders such as the IRA—not the one of The Troubles, but the Russian one called Internet Research Agency that was responsible for so much of the 2016 disinformation discourse. You can learn a lot by looking at what governments are choosing to back as well.
- The IRA targeting Central Africa with pro-Russian viewpoints was certainly a surprise to me and shows their likely investment in the region, which I hadn’t considered. The PRC’s investment toward the Uyghur population cover up is par for the course, but it’s odd to see accounts tied to a specific company the PRC is pumping. I was a little surprised about them removing the Mexico public health accounts, but perhaps it wasn’t related to the good kind of public health messaging. Tanzania and Uganda are intriguing because I just wouldn’t expect the resources for those kinds of operations, but it makes sense in a world where now you just need one social media guy with a phone and a lot of free time. Lastly, Venezuela wasn’t a surprise per se but rather the fact that they had an app they had written called Twitter Patria that was pushing the abuse. Patria being the Spanish word for homeland.
- Deplatforming works, plain and simple and I hope Twitter more aggressively targets these groups blasting information around the Internet and inauthentically amplifying it. I’ve got no problem if it’s real retweets, but when it’s shadow accounts run by an organization that’s being paid it becomes suspicious. Anyways, these removals certainly have an effect.
- I think it’s easy one for native speakers to spot “manipulative” social accounts and two for them to be parsed once reported to Twitter employees. I think the hard part has to be combing the entire firehose and hunting for these tweets programmatically in every single language. There’s nuance and local dialects and slang being used plus I would assume the natural language processing isn’t up to snuff for languages outside the languages spoken by most of the world. There is certainly meta information which is likely useful for Twitter employees to make determinations, but I’d bet disinformation groups are getting good about spacing out registrations, using VPNs, and what not in their work.
Ransom Where? Purported Extortion Results in Arrest
- Ubiquiti may be best known to a lot of listeners for their enterprise WiFi gear, but they cover a lot of ground, from networking to IP cameras and other physical security products to VoIP phones. They have been around for years and are a pretty major player.
- The indictment from the US Attorney General included four counts in all. The first is Computer Fraud and Abuse—Intentionally Damaging Protected Computers. The second is Transmission of Interstate Communications with Intent to Extort. The third is Wire Fraud, fourth is Making False Statements. The case laid out in the indictment is pretty comprehensive.
- Sharp is accused of extortion as an insider, with stolen intellectual property as the bargaining chip. He downloaded quite a bit of sensitive information (the charging document says gigabytes), then sent a ransom message in which he posed as an external attacker, demanding 50 bitcoin for the return of the stolen data; he also said he would reveal a backdoor vulnerability upon payment of the ransom. When Ubiquiti refused to take the bait, he posted an excerpt of the stolen data on Keybase (which Ubiquiti was able to get taken down fairly quickly.
- Sharp employed multiple tactics to cover his tracks. He used his existing credentials to access a key that allowed for expanded credentials and access. He also took some of the basic steps you’d expect, namely to set up a VPN, in this case with Surfshark, to mask the address he was coming from when he copied the files he was stealing. But he also spread out these activities over several days in December of 2020—he grabbed the key that elevated his creds on the 10th, and then the big day was the 21st, which is when he SSH’d into Ubiquiti’s GitHub and started grabbing the files. The downloads continued until around the 26th, so about 5 days in all. So during this time, he also changed log retention policies on their AWS infrastructure to 1 day, to help cover his tracks. And then, as part of the IR team after the incident was discovered, of course he played dumb.
- But there were problems for him, probably most importantly that his real, home IP address was leaked a couple of times, at least once due to a temporary Internet outage at Sharp’s home. The leaks were brief but they were enough!
- When Ubiquiti received the ransom note, they said pound sand, and good for them in doing so; but there certainly was harm to them as a result, as we will see.
- Ubiquiti discovered the breach on December 28, and in January, they announced it, and they also fixed a backdoor (it’s not quite clear to me whether this is the one that Sharp mentioned in the ransom note, though).
- Ubiquiti’s refusal to fork over the Bitcoin, which would have amounted to around $1.9M at the exchange rates of the time, irritated young Sharp, so he posed as a whistleblower and went to the media, accusing Ubiquiti of downplaying the importance of the incident. As a result of the media attention, their stock fell by around 20%, which amounted to around $4b in capitalization. It’s been a rough ride for them—they haven’t recovered in terms of stock price. In fact, it’s a little lower today than it was after that initial selloff.
- In terms of limiting the risk of a similar fate, the one thing that’s a little difficult to tell about this case, which would have some impact on how I respond here, is what level of access Sharp had, versus how much he escalated his privileges in the preparation phase. But I see a few places where this could potentially be detected and thwarted.
- The amount of exfiltration could potentially have been better instrumented, to alert on these gigs of data going out to an unknown IP (regardless of whether or not it had been exposed as Sharp’s own IP) from their Git accounts.
- Conceivably, multifactor auth or stronger PKI (public key infrastructure) for authentication and authorization might have helped, but it’s really hard to say whether that would be applicable in this case without more info.
- They also could potentially have been alarmed by the changes to the log retention policy. Configuration change management can catch this kind of stuff. But again, it’s a little tricky, since someone with enough access could essentially keep going up the chain of controls to cover tracks (in this case, changing the change management so that disabling the log retention change alert would not, itself, cause an alert). But the challenge here (among many) is that if you turn up the sensitivity on configuration changes by legitimate accounts, you’re going to generate a LOT of noise. So in short, if the insider is smart about how they do things, it can be pretty tricky.
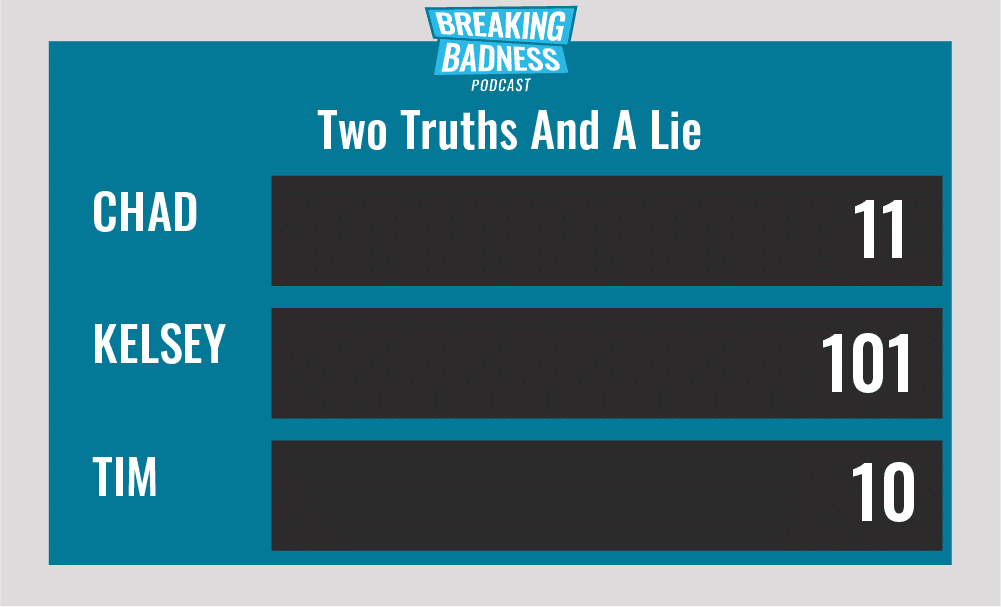
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Accounting for Propaganda
[Chad]: 3/10 Hoodies
[Tim]: 0/10 Hoodies
Ransom Where? Purported Extortion Results in Arrest
[Chad]: 8/10 Hoodies
[Tim]: 9/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!