Coming up this week on Breaking Badness. Today we discuss: The Voice of Treason, Flip The Script on Credential Stuffing, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
The Voice of Treason
- Like many services from our friends at Google, Voice is a handy application. It allows you to use a phone number for a variety of things, including tying in with Voice over IP telephony systems, or as an alias that will forward calls from your Google Voice phone number to your mobile or desk phone number. Let’s say you want one of those super sexy 212 area code numbers even though you live in Paducah, Ky. Google Voice can help you with that. And by the way, it’s useful not just for voice calling but for text too.
- Let me begin by saying that this is not a technical kind of scam. I thought this one was interesting because it’s a reminder of how we need to have our security-awareness shields up against many different modalities of social engineering. So why is Google Voice useful to scam artists? Well, two main ingredients in this particular stew: impersonation, and abuse of trust. It’s very easy for scammers to impersonate someone via their phone number, and it’s also easy for them to use phone capabilities to establish trust—fraudulently in this case.
- What cybercriminals are doing here is using your phone number as a phony authentication method to raise your trust level in them. And this is another part of this scam that I wanted to highlight: the psychology of social engineering is becoming more subtle and, arguably, more effective. What the scammers will often do, when they are using Google Voice for these scams, is they’ll tell the victim that they (the scammer) are trying to protect themselves against being scammed. “I’m just like you,” they’re saying. “You can trust me because we share this interest in protecting ourselves against those evil scammers.” Brilliant! So what they do is tell you that they’re going to send you an authentication code, via SMS or voice, and that’s how they are abusing Google Voice. And this gets to the part of your question about having your phone number out there on the Info Superhighway: that’s how they know how to reach you to send the authentication code. Once they have that code, what they are actually going to do is hijack your phone number to use it in other scams against other victims—when they’re scamming you, they probably have the Google Voice control panel open, because it’s actually Google who sent the verification code. When you read it to them, they have the last piece they needed to imitate you with Google.
- There are a couple of things cybercriminals can do with a hijacked Google Voice account. One is they can now impersonate you to carry out various kinds of schemes, probably a lot of the usual account-hijacking or billing fraud, etc, kinds of activities. They can use it to gain access to your gmail account, which can lead to all kinds of other shenanigans, as you’d imagine, and/or they can pose as you in order to scam other victims down the line.
- There are a few things you can do if you are a target of such a scam. Of course the FBI would appreciate it if you dropped them a line (ironically, from your now potentially compromised phone number, calling your local FBI office, or you can visit ic3.gov to report it. But you should also do some of the same blocking and tackling that you’d use when you think you’ve been scammed: change passwords, set up multi-factor authentication NOT using SMS, but instead something like an authenticator app or a fob; keeping an eye on critical accounts to catch any suspicious activity as early as possible, and so on.
Flip The Script on Credential Stuffing
- Credential stuffing has been around for a long long time. In Infosecurity, credential stuffing is taking a known username/password combination and throwing it up against as many different services as possible to try and gain access to accounts that have re-used passwords.
- What prompted the New York’s Office of the Attorney General investigation was really a recognition of the volume of attacks faced by users and businesses
- According to a recent study, there are more than 15 billion stolen credentials circulating on the Internet.
- This enormous cache of credentials has fueled a dramatic rise in credential stuffing attacks. The operator of one large content delivery network reported that it witnessed more than 193 billion such attacks in 2020.
- These attacks are extraordinarily costly for both businesses and consumers. The Ponemon Institute’s Cost of Credential Stuffing report found that businesses lose an average of $6 million per year to credential stuffing in the form of application downtime, lost customers, and increased IT costs.
- According to the OAG, their findings indicate that "over a period of several months, the OAG monitored several online communities dedicated to credential stuffing. The OAG found thousands of posts containing login credentials that had been tested in credential stuffing attacks on a website or app and confirmed to provide access to a customer account. Members of these communities were free to use these validated credentials to break into the customer accounts themselves, or use them for their own credential stuffing attacks on other companies’ websites and apps.”
- After reviewing thousands of posts, the OAG compiled login credentials for customer accounts at 17 well-known companies, which included online retailers, restaurant chains, and food delivery services. In all, the OAG collected credentials for more than 1.1 million customer accounts, all of which appeared to have been compromised in credential stuffing attacks.
- The OAG found 4 areas where businesses can focus their improvement efforts:
- 1. Defending against credential stuffing attacks (bot detection, CAPTCHAs, etc)
- 2. Detecting a credential stuffing breach, (WAF, monitoring fraud)
- 3. Preventing fraud and misuse of customer information. (forcing a re-auth at the time of purchase, which they aren't going to want to do)
- 4. Responding to a credential stuffing incident. (investigation, remediation, customer notification)
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
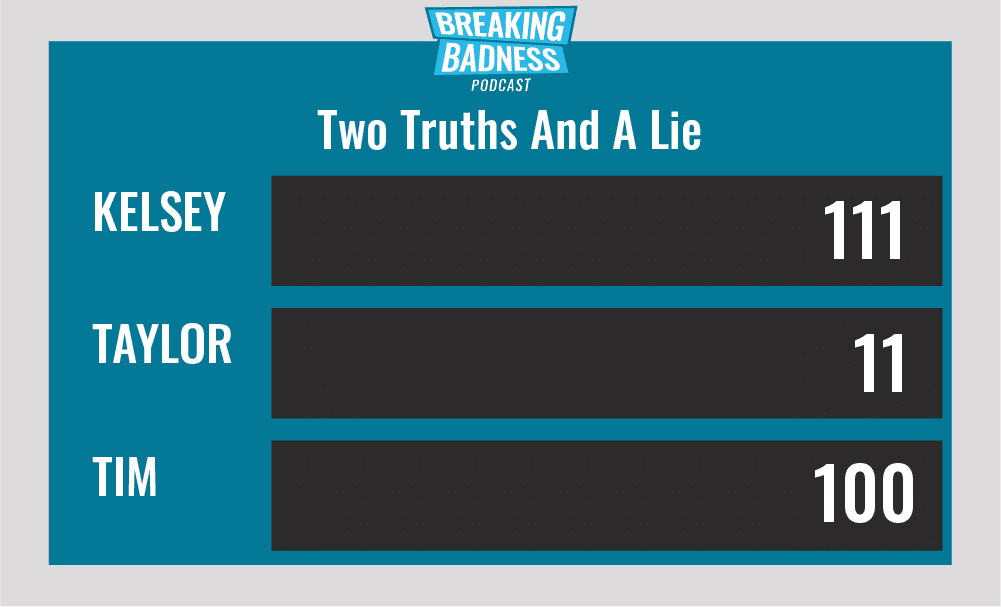
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Voice of Treason[Taylor]: 2/10 Hoodies[Tim]: 2/10 Hoodies
Flip The Script on Credential Stuffing[Taylor]: 2/10 Hoodies[Tim]: 3/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!


