Coming up this week on Breaking Badness. Today we discuss: Time To Spill The Conti, Attackers Kick Up a DDoS, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Time To Spill The Conti
- Please note this is an evolving story and additional details may surface between when our podcast was recorded to when it’s published.
- Two weeks ago, a Ukrainian researcher leaked nearly two years of internal chat logs from Conti.
- Conti is the name of a ransomware group that came around in late 2019 operating out of Eastern Europe. They’re extremely aggressive and a good number of their attacks are focused on the healthcare sector. For example, they recently tied up the Irish healthcare system.
- The Conti organization itself appears to have about 60-70 people employed, but that number is fairly nebulous. We can see there are individuals associated with the organization, but may not officially be on their payroll for extended periods of time.
- We can see there appears to be a hierarchy within the organization complete with middle management. They also have budgets and make decisions when to outsource work. They do appear to have target markets.
- In terms of their budget, it does look like they make allocations for things like anti-virus software to check against their malware as well as virtual private servers.
- People are so intrigued and interested in these leaked chat logs because it’s not often we get to see a look on the inside of these types of operations.
- We can also see what associations Conti members make with those outside their organization - specifically journalists and negotiators - which as a victim of a malware attack would be frustrating to learn.
- In terms of what this means for defenders: we’ll see the fallout from this in the coming months. This leak may not slow them down a whole lot, but it at least gives us a window to what they’re doing currently and how they operate.
Attackers Kick Up a DDoS
- Researchers from security vendor, Akamai, published a report this past week highlighting a new technique to amplify DDoS attacks.
- DDoS (distributed denial of service) attacks are carried out with networks of Internet-connected machines. The name of the game seems to be how big a DDoS, in terms of total bandwidth, you can pull off. It’s all about setting records because in general, there’s nothing new or novel about DDoS, but that’s where this story is interesting because there is indeed something new going on here.
- Akamai has seen a new way for threat actors to boost the effectiveness of their DDoS attacks *using this one weird trick*. The technique is known as TCP Middlebox Reflection and was discussed as a theory 6 months ago, but unfortunately they have detected it in the wild for the first time.
- The term “middlebox” is a newer term - even to us - when this story broke. “Middlebox” in this instance refers to things like firewalls or other kinds of filters, which are designed to accomplish various tasks, but in particular, the example that came up a lot in the discussions of this attack technique were wide-scale web filters a la the Great Firewall of China. “Middleboxes” are configured to reply in a certain way to various kinds of connections and conditions. What the researchers found was that specially-crafted packets could trigger an unexpected reply from the middlebox. The issue is that the affected middleboxes don’t take TCP stream states into account when attempting to enforce content filtering policies, so they can be made to respond to out-of-state TCP packets. Which doesn’t refer to what license plate the packet has on its car.
- This is such an effective technique for DDoSers because of the amplification factor. The DDoSer can realize a more than 6000% amplification in terms of bandwidth. This means they can create a huge amount of disruption with much lower resources than was possible with earlier techniques. It’s a force multiplier.
- It is typical to see attackers abuse UDP reflection vectors. UDP amplification has been more prevalent than TCP. The other hall of fame DDoS methods that you’ve heard of like NTP, RIPv1, and more recently the memcached vulnerability, all were UDP amplification, just with lower amplification factors than this one.
- The attack in question has been observed over the last few weeks - late February, early March 2022. Akamai observed multiple campaigns targeting banking, travel, gaming, media, and web-hosting industries. They said that while the observed attacks leveraging this technique thus far are still small compared with other vectors, they appear to be growing in popularity and size. They’ve seen attacks that started around 50 Mbps, but soon after that they saw much higher bandwidth, as high as 11Gbps. It’s clear to them that they’re watching the actor basically sort of sharpen their skills—the major attack hasn’t occurred thus far.
- The good news for defenders is there are steps you can take to configure how the box handles various parts of a TCP handshake to make it much less susceptible to this kind of abuse. A lot of firewalls and other such gear do have configuration options for how they handle low level network stack stuff like this. Other methods would be using a combination of anti spoofing and out-of-state mitigation configurations that would be able to thwart the attack easily and using signature tools like snort to drop cleartext patterns as seen in the response traffic. Firewall ACLs can also be used to block the known incorrect patterns; for example, a rule like:
- Deny tcp any eq 80 host x.x.x.x match-all +syn -ack packet-length gt 100
- This rule would drop any SYN packets destined to port 80 with a packet length greater than 100.
- The frustrating thing about this story is that, at least in what we’ve read, no one is yet publishing a list of which boxes are susceptible to this kind of abuse and which are not.
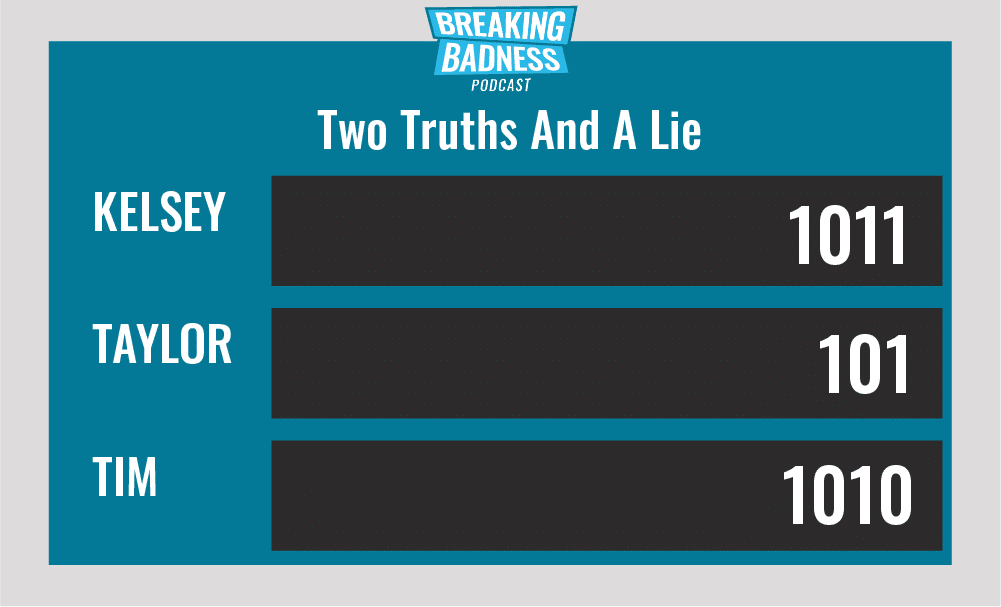
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Time To Spill The Conti[Taylor]: 2/10 Goodies[Tim]: 1/10 Goodies
Attackers Kick Up a DDoS[Taylor]: 3/10 Hoodies[Tim]: 3/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

