Coming up this week on Breaking Badness. Today we discuss: Don’t Twilio Your Thumbs, Signed, Sealed, Malicious, and Two Truths and a Lie
Here are a few highlights from each article we discussed:
Don’t Twilio Your Thumbs
- It was the talk of the town at Black Hat – unknown attackers targeted Signal users after they broke into the systems of communications services company Twilio.
- By doing this, those hackers could see victims’ text messages and had a shot at controlling their accounts
- For those who don’t know, Twilio provides text verification services
- Any text you receive from a bank or a doctor’s office (just as two examples), likely comes from Twilio or a Twilio competitor
- Where Signal comes into play
- When Signal users register their phone numbers, they get an SMS verification code from Twilio to then share back to Signal
- Signal verified they were one of the victims of this hack and about 1,900 of their users were affected
- This means that hackers could intercept these SMS messages and impersonate their victims
- It’s not all bad news though
- Signal does have fail safes in place
- Hackers still don’t get access to critical information like message history, contact lists, or profile information
- Signal confirmed they do not keep copies of your message history (it’s stored locally on your device)
- They have created a Signal PIN which wasn’t affected by the hack
- The Signal PIN grants access to profile information, contact lists, etc.
- So hackers could potentially impersonate a victim, but wouldn’t be able to access the victims’ contacts or messages
- Is SMS verification safe?
- These incidents remind us that SMS is not as secure as we’d like and enabling other security measures is important
- How is Signal moving forward?
- The 1,900 victims will need to re-register their accounts (with provided steps)
Signed, Sealed, Malicious
- If job seeking wasn’t difficult enough, now there’s hackers to worry about
- The Lazarus group hailing from North Korea is using a signed malicious executable for macOS to impersonate the Web3 company, Coinbase
- This specific story is really kind of a tale of two malwares: a Windows version that has been making the rounds, and now this MacOS version
- It’s actually not 100% clear how widespread the Mac one is in the wild, however
- But it’s interesting any time there’s new Mac-targeting malware, because we hear so often about the Windows ones
- Who is Lazarus
- A fairly notorious North Korea-attributed group that has pretty much covered all the bases where malicious online activity is concerned—they’ve done DDoS, spear phishing, ransomware, intellectual property theft, espionage—you name it.
- Kind of a swiss army knife and they have a lot of capabilities
- What is Lazarus doing?
- This is a pretty well-designed social engineering attack
- It’s a form of phishing, though to our knowledge it’s not explicitly over email; it seems to go over LinkedIn
- They approach the would-be victim with a job opportunity with Coinbase, and they try to get their mark to download a PDF document explaining the job opportunities there
- It’ll display what appears to be a “real” PDF, but loads a malicious DLL that allows the bad actors to infect the device
- It installs these three files:
- The bundle FinderFontsUpdater.app
- The downloader safarifontagent
- A decoy PDF called “Coinbase_online_careers_2022_07” PDF (same as the Windows malware)
- It installs these three files:
- This isn’t the first time Lazarus has done this either – they ran a similar campaign in 2021 with a different PDF
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
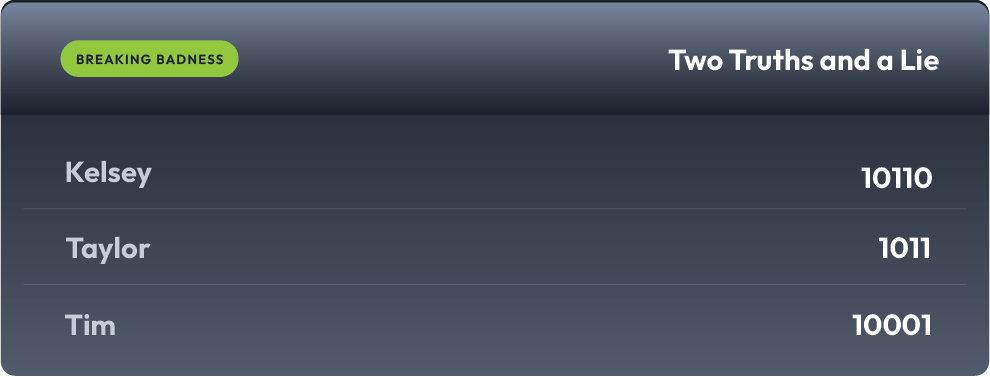
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Don’t Twilio Your Thumbs
[Tim]: 4.5/10 Hoodies
[Daniel]: 3.5/10 Hoodies
Signed, Sealed, Malicious
[Tim]: 3/10 Hoodies
[Daniel]: 3.5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




