Coming up this week on Breaking Badness. Today we discuss: Valid Target Acquired, 0ktapus’s Garden, and Two Truths and a Lie
Here are a few highlights from each article we discussed:
Valid Target Acquired
- The North Korean ‘Kimsuky’ threat actors are going to great lengths to ensure that their malicious payloads are only downloaded by valid targets and not on the systems of security researchers
- From a marketing perspective, Kimsuky gets it – going after the most valid targets just makes good business sense
- Kimsuky is a state-sponsored threat actor group attributed to North Korea
- According to CISA they’ve been around since approximately 2012, and their primary objective has been intelligence gathering
- They go after groups like think tanks, government organizations, or even individuals who they see as having high value intelligence
- What does “valid” mean to Kimsuky?
- They primarily target South Korea, Japan, and the United States
- Typically the individuals they go after include politicians, diplomats, university professors, and journalists as the victims of a spearphishing campaign
- Now, we don’t know exactly how they decide which specific people to go after, but presumably they have people who spend a lot of energy researching who would make a good target
- They primarily target South Korea, Japan, and the United States
- As mentioned above, Kimsuky carries out their scheme via spear phishing and as so often is the case, the email contains a link
- But here’s where it gets interesting: what the would-be victim actually gets to from that link depends on whether they are one of the targets on the list
- The link goes to a C2 server which checks some parameters like the recipient’s email address, their OS, and it also uploads a text file. Then a second stage does additional validation, checking their IP address. So here, some logic decides whether it is a valid victim or not. If it is, it downloads a malicious document; if they are not, it downloads a benign one. Clever!
- It’s a lot of if/then statements on Kimsuky’s part, but as of right now, we don’t know what that benign document for non-victims looks like
- But even though Kaspersky indicates that the blogs are innocuous, they still defang the URLs for them, and we don’t have a VM handy to go look at them
- Folks at Kaspersky weren’t able to get the final payload because they weren’t able to imitate the parameters of what would be considered a valid victim
- This indicates the scheme works pretty effectively because we would expect Kaspersky’s team would be good at spoofing a victim
- We wouldn’t be surprised if we saw more of this because of its effectiveness
0ktapus’s Garden
- Multi-factor authentication is often brought up as a good method for security, but research shared by Group-IB shows what happens when it’s intercepted by bad actors
- This attack began in the shade! But seriously, sometime around March, Oktapus began setting up domains targeting corporate okta instances and other single sign-on mechanisms with new domains such as mailgun-okta[.]com and okta-tmobiie[.]org
- We can see a big uptick in those domains starting June 8th or so, and it first hit our radar actively on June 13th – Ian had set up an okta monitor in Iris Detect after the Lapsus breach but hadn’t been checking it so he could let it soak a bit
- Once he checked it on the 13th, it became clear that a coordinated campaign targeting okta instances was going on across a bunch of different companies and industries, but especially centered around service-centered companies (mailchimp, hubspot) cryptocurrency companies, and telecommunications companies like T-Mobile
- We focused on the T-Mobile domains in particular at that point, which you can see in the at-securitysnacks account that put the intel out there
- Once phished, some remote administration gear was delivered, along with info-stealing malware that reported back to a particular Telegram channel. Through monitoring at Group-IB was cleverly able to tell just who had credentials phished
- Publicly, we don’t know who is behind the attack yet
- Group-IB was able to do some substantial detective work that led them to a possible identity of a principal actor but that hasn’t been released yet
- It’ll be interesting to see what comes out given that some of the initial analysis pointed to a less-sophisticated actor, but their ability to so quickly pivot through Twilio and their targeting of a journalist in particular may speak otherwise
- There’s a great breakdown of targets by sector regarding this attack
- Software companies dominated at 53%, telecoms at 22% and business services at 21%. From there it broke down further across finance, education, retail, and more
- The big focus was definitely software, telecoms, and business services, not just to compromise them directly but to act as whole waterfall in which early compromises created the opportunity for hacks further downstream
- We’re only just beginning to see the effects of this attack
- The real knock-on so far is Twilio – a service that assists with authentication methods, including sending text messages of one-time passwords
- The actor was able to intercept one-time pads from multiple services, including encrypted messaging app Signal – in fact, at least one journalist has already come out and stated his Signal account was taken over for a 14-hour period, likely as a result of this hack
- We’ve seen downstream effects on Cloudflare as well, and just today DoorDash came out with a statement admitting compromise
- Recommendations for mitigations in this situation
- Ian’s going to sound like a company guy here, but he does a thread of shady-looking domains every Monday or so on twitter that takes half an hour or an hour to put together across a whole bunch of companies and industries he likes to watch
- One corporation could pretty easily defend all its brands with a set of DomainTools Iris Detect monitors an hour or two a week – that’s the easy button option for detection and investigation coordination. You can also go closer to source and do things like Aaron Gee-Clough suggested, getting access to the .com, .net, and .org zonefiles from Verisign and doing a daily diff – unfortunately that doesn’t cover a lot of top-level domains that don’t publish zone files
- But long story short, if you establish and test your own monitoring, you see campaigns targeting your assets and services pop up, and can respond in a much more timely and surgical manner, including warning your employees and userbase, takedown requests, and further investigation to identify bad actors
- Another really good mitigation here is pre-emptively registering domain names around your brand and software you use, so for instance if Ian was T-Mobile, registering a bunch of combinations of Okta and tmobile across a bunch of top level domains to make it harder for a bad actor to register and use a believable domain name
- Since the 0ktapus details came out we’ve seen a huge increase in companies doing pre-emptive registrations around okta and similar so they control them from the start
- We’ve also seen Twitter doing similar for months – proactively registering a ton of support/help/security-related domains with twitter in them to prevent bad actors from using them. But it’s very much a whack-a-mole process, so monitoring is extra important
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
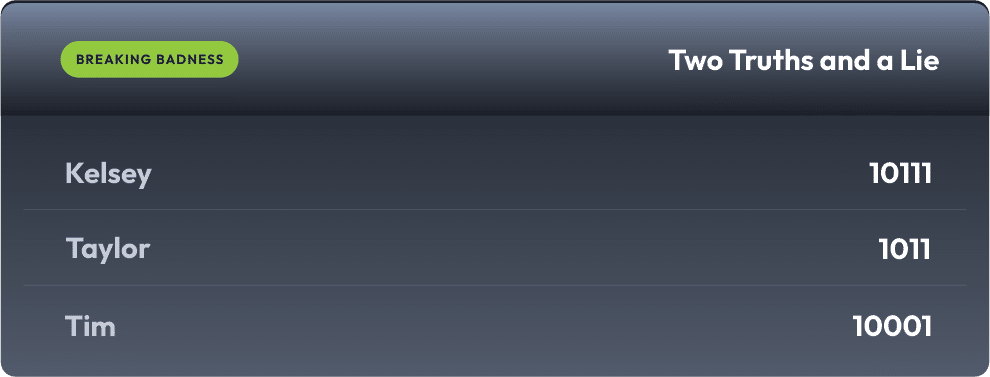
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Valid Target Acquired
[Ian]: 7/10 Hoodies
[Tim]: 1/10 Hoodies
0ktapus’s Garden
[Ian]: 5/10 Hoodies
[Tim]: 6/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




