Coming up this week on Breaking Badness. Today we discuss: All The World’s A Multistage, Passkey To My Heart, and Two Truths and a Lie.
Here are a few highlights from each article we discussed:
All The World’s A Multistage
- New malware was discovered by AT&T Alien Labs targeting endpoints and IoT devices running Linux operating systems
- The malware downloads and executes Metasploit’s “Mettle” meterpreter to maximize control over infected devices
- For those who may be unaware, Metasploit is used by both bad actors and ethical hackers to find vulnerabilities on networks and servers
- Chain, chain, chain (like the song)
- The Shikitega malware uses a multi-layer infection chain with three stages
- Stage 1 is small and contains an ELF file that’s about 370 bytes divided into modules. And although small, each module has a task including downloading the Metasploit meterpreter mentioned above
- In this step, privileges are escalated
- When execution is complete, the command and control (C2) server steps in with a shell command to begin executing on the target machine
- Five different shell scripts are downloaded and executed and persists in the system by setting 4 crontabs
- In the final stage, Shikitega downloads and executes the XMRing miner
- An additional crontab is set to download and execute a crypto miner for the C2 server
- The Shikitega malware uses a multi-layer infection chain with three stages
- What about mitigations?
- The recommended mitigations are pretty standard
- Keep your software up to date
- Have antivirus or endpoint detection response (EDR) installed in all endpoints
- Use a backup system to backup server files
- The recommended mitigations are pretty standard
Passkey To My Heart
- The promise of ending the use of password-based logins has been broached for years and Apple is making strides toward that goal with the launch of iOS 16 on September 12 (which was our recording day!)
- The problem with passwords
- Well, this goes back to ancient Rome, where Caesar invented the Caesar cipher and while it seemed like a great idea at the time, it became apparent after not so long that it was relatively easy to crack, especially if you held a knife at just the right angle at the throat of the one who knew the password
- We really haven’t evolved that far, except the knife is now called “social engineering,” but that’s only one aspect of the problem
- The most popular passwords are still ones like “123456” and “password.” and other variants that people apparently think are quite ingenious like “password123456” or “Passw0rd.” In other words, passwords that, if they weren’t so guessable in the first place, are trivially easy to derive with a dictionary attack
- Then there are the practical issues. People forget passwords. People write passwords on whiteboards and then go on international TV with said whiteboards in the visible background
- So Apple is implementing its password-less feature known as passkeys
- Passkeys are an implementation of PKI – Public Key Infrastructure
- This is a technology that has existed in one form or another for a couple of decades now—where an authentication is completed by the relationship between a public key, which sits on a server in a public place and anyone can get access to, and a private key, which is held confidentially by the user
- Only with both keys can encrypted data be decrypted
- Possession of a private key, when the circumstances under which the private key was generated, is a form of authentication. That authentication is strengthened by possession of a specific device that holds that private key
- So the way this works is that when you go to sign into a service, with these latest versions of MacOS and iOS, you are prompted to create a passkey, and the generation of that makes use of further authentication such as face ID or touch ID (or probably, I suspect, a plain old password). So once you have created your passkey, as long as you’re in possession of your Apple devices, you then have a passwordless way to access resources
- Passkeys are an implementation of PKI – Public Key Infrastructure
- Who created this concept?
- While Apple is rolling this out, they are not the inventors, though they’ll get the credit for a mass implementation of them that should be relatively seamless for most users to implement
- For many people who don’t study these things, that will be functionally equivalent to “inventing” it, but it’s been around for a while
- There’s an industry consortium called the FID Alliance (FIDO stands for Fast ID Online) that has been working with various partners to promote moving beyond the password for several years now. This is a big boost for their work
- How does the concept of a Passkey enhance security?
- It’s definitely the case that it’s not a panacea, among other things because it doesn’t solve the problem of a malicious actor with physical access to the protected device. (now, at some level, that’s not going to be much of a solvable problem, except via some very cumbersome continuous-authentication concepts that aren’t likely to be mainstream any time soon if ever)
- The big advantages here are that these private keys are long blobs of random text that are not guessable in any meaningful sense, and you can’t choose a lame one that everyone else can guess, the way you can with a password. PKI has proven to be quite durable and practical. Basically, this technology can help solve *one* of the major problems with passwords, which is poor password practices by humans
- Can the Passkey be used between devices like your iPhone and a Windows laptop?
- No, remember the FIDO Alliance? They are platform-independent. So, while the public keys reside on Apple servers, these passkeys can be used on other devices
- The typical way that would happen is that the challenge sent to your device is in the form of a QR code that you scan with your phone. Your phone then communicates to your Windows laptop via Bluetooth—not over the TCP/IP network. That’s really important, because it means that an attacker can’t just hijack that QR code and then import your passkeys. The possession of your iPhone, unlocked, is critical to making the cross-platform model work
- Reception of this implementation
- We think it’s going to give this technology a good launch, because a lot of people do recognize that passwords are a big hassle—even if they don’t care about the security flaws with them
- But, here’s the major caveat—the online services that you might authenticate to with these passkeys have to support them. That won’t happen overnight. But this being a feature of Apple’s latest operating systems will create a lot of pressure on services and apps to support the passkeys—a lot more pressure than, say, Linux or Solaris implementations. Or Amiga. I jest.
- And let me add that at least one password manager, Dashlane, has announced support. Others will follow, I’m sure.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
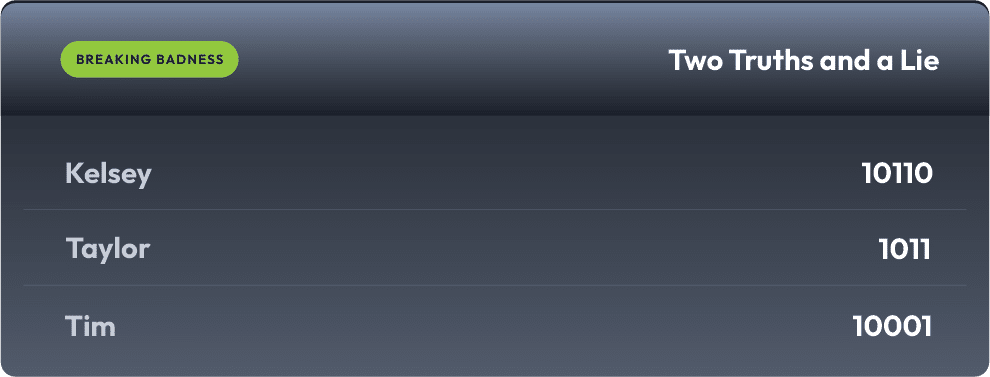
Current Scoreboard
This Week’s Hoodie/Goodie Scale
All The World’s A Multistage
[Taylor]: 4.5/10 Hoodies
[Tim]: 5/10 Hoodies
Passkey To My Heart
[Taylor]: 8/10 Goodies
[Tim]: 6/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




