Coming up this week on Breaking Badness. Today we discuss: Double Double Extortion and Trouble, OldGremlin, New Tricks, and Two Truths and a Lie.
Here are a few highlights from each article we discussed:
Double Double Extortion and Trouble
- A BlackByte ransomware affiliate is using a new custom data stealing tool called ‘ExByte’ to steal data from compromised Windows devices quickly.
- The kudos for discovering ExByte goes to Symantec, which does pretty consistently great research. Specifically they credit their Threat Hunter team
- According to Symantec, BlackByte is a RaaS – ransomware-as-a-service – operation that is run by a cyber-crime group that they call Hecamede
- We first saw wide attention to this group in February of 2022 when the FBI issued an alert stating that BlackByte had been used to attack multiple entities in the US, including organizations in at least three critical infrastructure sectors
- In recent months, they say that BlackByte has become one of the most frequently used payloads in ransomware attacks
- While February was when it got widespread attention early this year, the gang actually seems to have emerged back in July 2021, when it began exploiting vulns to target corporate victims worldwide
- BlackByte had some initial success, hitting manufacturing, healthcare and construction industries in the US, Europe and Australia, things got less fun for them when the good folks at Trustwave released a free decryption tool. Anyway, as we can see, they’ve been evolving their toolin
- And while we have to give the usual attribution-is-hard disclaimer, there’s some decent evidence pointing back to Russia for this group—their tooling has been observed to be coded not to encrypt the data of systems that use Russian or CIS-languages. But that’s somewhat speculative, and of course since it’s RaaS, the malicious actors actually hitting victims could be quite varied
- We’ll start with a quick overview of data exfiltration and its importance in double-extortion attacks
- As context, double-extortion ransomware, which has been popular for a few years now, is a method where the malware does two things: it encrypts target files – the first extortion candidate – and it exfiltrates data into the hands of the malicious actors, where they usually threaten to sell or post it on underground forums: the second method of extortion
- Tim actually heard something interesting about this at the mWISE conference last week – some folks in the security community are starting to see ransomware actors not even bother with encryption, going straight to exfiltration
- Exfil used to be the second method, now it’s perhaps the first one in some cases, but this seems to be a traditional double-extortion scheme
- What are the functions of the ExByte data exfiltration tool?
- Basically it’s built for speed. Its goal is to get the exfiltration done as swiftly and reliably as possible
- One of the things that’s interesting here is that the exfil target is the Mega.co.nz cloud storage site
- Mega is legitimate, though there’s certainly been plenty of sketchy stuff on there over the years—what can you expect with a free upload/download site?
- But that makes detection of the exfil perhaps a little less easy, since the exfil traffic could potentially hide within legitimate traffic, especially in a larger environment where you might have benign traffic to Mega
- Having said that, it’s not hard to imagine that some shops could choose to block Mega – my guess is that there’s not a lot of organizations that rely on that site for business-critical file transfers
- This tool performs checks to see if it’s running in a sandbox environment, but what if that were actually the case?
- This has been common for a lot of malware ever since not too long after sandboxing became a popular defensive tool
- What the malware authors are doing here is attempting to prevent detection of the malware, and tipping their hand. So there are a bunch of files and processes that it looks for to make the determination about whether it’s in a sandbox or not
- Examples would be sxin.dll, avghooka and avghookx, pstorec, dir_watch, and a bunch of other dll’s. It also looks for a bunch of analyzer and debugger tools. Anyhow, these “what environment am I in” checks are pretty routine now
- If it’s not in a sandbox, it then sets up shop with tooling for several different functional areas like shutting down certain kinds of alerting to bypass EDR, disabling local firewalls, looking for target files, and getting the upload path established
OldGremlin, New Tricks
- OldGremlin, one of the few ransomware groups attacking Russian corporate networks, has expanded its toolkit with file-encrypting malware for Linux machines.
- For those who are unfamiliar, here’s a quick overview of who OldGremlin is:
- They are a hacking group that has been identified to target Russian companies – finance, oil, etc.
- They have Russian-speaking members
- They first doxxed in 2020 and continued their operations to today, popping up in March, June, and August of this year, with ransomware – initially just windows machines, but recently did an expansion of their skills to target Linux machines as well
- OldGremlin is known to carry out fewer campaigns per year, but those carried out are incredibly lucrative – they demanded $17 million off one attack this year and may have netted $30 million so far this year alone
- They’re known for taking breaks and coming back to the surface
- In the campaigns they typically perform, the gang pretends to be a financial organization, a real estate company, or a consulting group
- They began these campaigns with a phishing email, but updated the malware delivery method
- The group uses their own custom toolkits, but they’ve also been known to use open-source tools like PowerSploit and Cobalt Strike
- They are a hacking group that has been identified to target Russian companies – finance, oil, etc.
- Why does OldGremlin target Russia when typically other bad actors tend to avoid it?
- Well, they’re zigging when everyone else is zagging
- But in all seriousness, they found a winning strategy to crack these orgs open and get revenue. The thinking is, the easy targets will run out and they’ll go after other targets
- Well, they’re zigging when everyone else is zagging
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
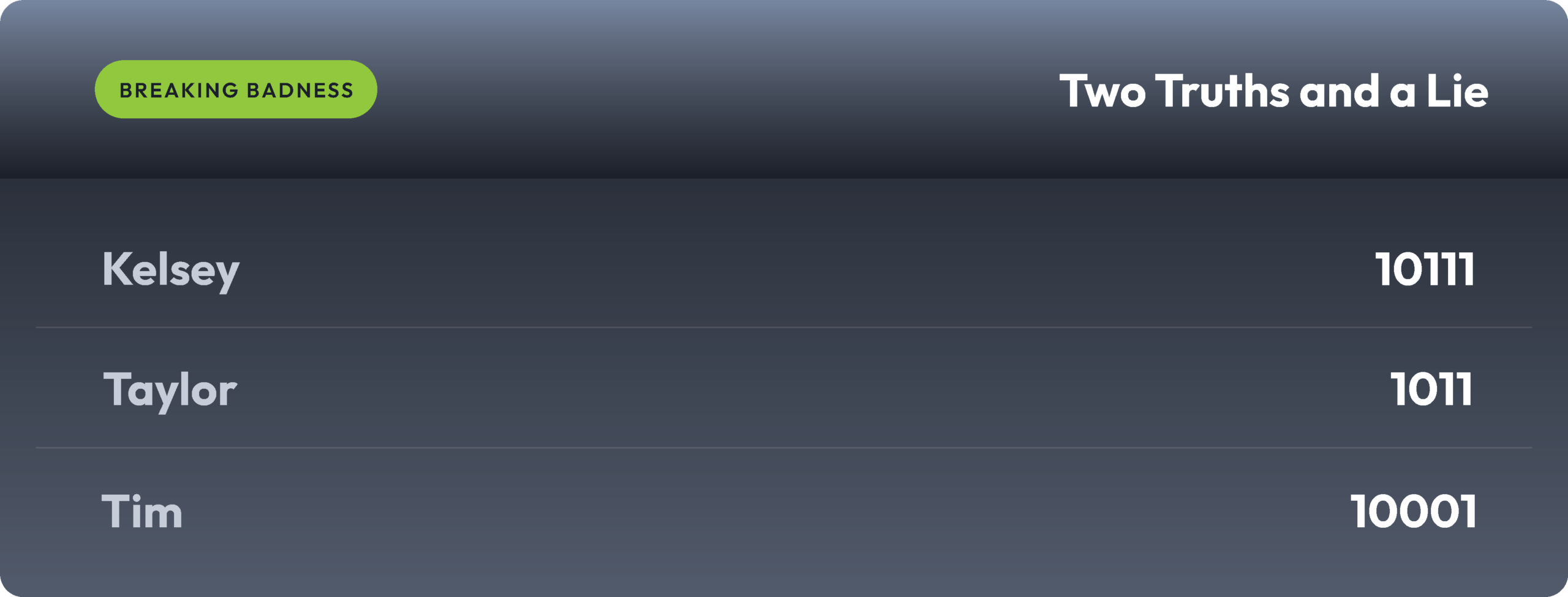
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Double Double Extortion and Trouble
[Taylor]: 4.5/10 Hoodies
[Tim]: 4/10 Hoodies
OldGremlin, New Tricks
[Taylor]: 5.5/10 Hoodies
[Tim]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




