Coming up this week on Breaking Badness. Exclu-se You, Let Me Speak To Your Hypervisor, and Two Truths and a Lie.
Here are a few highlights from each article we discussed:
Exclu-se You
- The Dutch police announced this past Friday that they dismantled the Exclu encrypted communications platform after hacking into the service to monitor the activities of criminal organizations.
- What exactly is the Exclu platform?
- At its core, Exclu is a European encrypted messaging app with some other bells and whistles.
- It claimed an ability to remotely wipe devices, along with exchanging the usual range of messages – texts, notes, voice memos, and videos
- It cost over one hundred euros per month, which is kind of eye-watering to regular consumers, and is at least implicitly indicative of the kind of customers Exclu oriented itself towards
- It’s used by many – not just bad actors, but folks in sensitive fields like lawyers, doctors, and notaries
- There is some indication that other users engaged with it for legitimate privacy and sensitivity reasons – we’re guessing that’s where a chunk of the Dutch user base comes from
- Between the cost of the service and its relative size (which is about 3,000 users) we’re a little surprised folks on the straight-and-narrow would use it
- There may be some intricacies around privacy and having the servers in the Netherlands that made it more attractive in context, compared to larger services that may have US-based complications
- At its core, Exclu is a European encrypted messaging app with some other bells and whistles.
- What efforts were made to bring these cybercriminals to justice?
- It looks like a series of overlapping investigations by European law enforcement eventually came together, including a Dutch investigation on the service and its owners and employees, and a German investigation on service users
- But it looks much wider than just that, with Belgium, Italy, Sweden, and France involved at least
- Dutch law enforcement in particular are incredibly sophisticated (and, frankly, fun to watch) when it comes to cybercrime investigations, and it looks like they were able to fully compromise the system amidst the takedown – they now have five months of messaging data to keep searching through
- Alongside the raids aimed at Exclu itself, they’ve made dozens of other arrests and dismantled at least three drug labs
- This isn’t the first instance of a crypto-phone platform takedown either, is it?
- Nope! It’s become a favorite pastime of law enforcement, in fact
- EncroChat, which was a lot bigger and more robust, got taken down last July in what looks like a similar operation
- And then there’s our personal favorite, ANOM, which was a law enforcement operation from the start, a joint operation between the US FBI and Australian Federal Police to create a fake end-to-end platform from scratch so they could monitor it. Even the people working for ANOM didn’t know that, which makes for a fascinating story
- What’s next for this investigation?
- We expect the raids will continue while European police continue to go through the five months of messages they have
- And the intelligence seized from those, along with cooperating defendants, will probably lead to more raids not directly connected with Exclu
- And bad guys sweating it out until the knock on their door often leads them to make more mistakes too
- Whenever you seize a platform, if you work the investigation right it can be just a huge watershed event with follow-on effects for years. We’re gonna need more popcorn
Let Me Speak To Your Hypervisor
- Cybercriminals are actively exploiting a two-year-old VMware vulnerability as part of a ransomware campaign targeting thousands of organizations worldwide
- This is emerging and new articles are being published on this as we speak
- Let’s start with what VMware is
- They are a virtualization software provider and has been around almost as long as everyone in the game
- They help you take big computers and turn them into small computers that can be used to do just about anything you want
- ESXi is installed directly onto a server and then divided up into smaller computer and can vary based on operating system (OS)
- They were bought by BroadCom not too long ago
- This is an unpatched bug, so does that mean the organization knew about it previously?
- VMware being around as long as it’s been, they’ve put out many versions of ESXi – it’s one of those things where you’re continually evolving with operating systems as they upgrade
- As the OS market evolves, the hypervisor market also has to evolve, so you’ll find bugs
- Folks are pointing at these bugs saying they’re used to gain control of a machine and ransomware follows not too long after, but no one has really come out with the full exploit chain – right now it looks like it could be compromised – but it’s an emerging thing
- These vulnerabilities are known and there are patches, but it’s tricky to patch a hypervisor because there will be downtime and the level of support for your OS can be diminished
- This ransomware variant is known as ESXiArgs and we don’t know who’s being targeted, is that a fair statement?
- It’s very much ongoing, so yes
- There’s been a few generations of this as well, so the initial encryptions behind this were designed by someone who doesn’t seem super familiar with ESXi
- The attackers are using a triple extortion technique – what is this?
- Single extortion would be, “I have your files, you have to pay me.”
- Double extortion would be, “I will post your files and sell them,” so you can get money from the victim and money for selling them to another party
- Triple extortion is, “ok now I will sell the data back to the victims.”
- We’re trying to figure out how to get to a fourth, but we’re not totally sure and we don’t want to find out :)
- Is patching the only mitigation for this attack?
- It’s really tricky sometimes to do the patches, as we mentioned earlier
- Obviously, make sure your ESXi hosts can’t talk to the Internet – that would be really helpful, but even then that’s still tricky
- If you look at CISA, they’ve posted some scripts to hopefully help recover some files – that might be an avenue to restore data
- Patching and upgrading off of old version can open a Pandora’s box that might not be supported by other vendors – it’s a bit of a mess
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
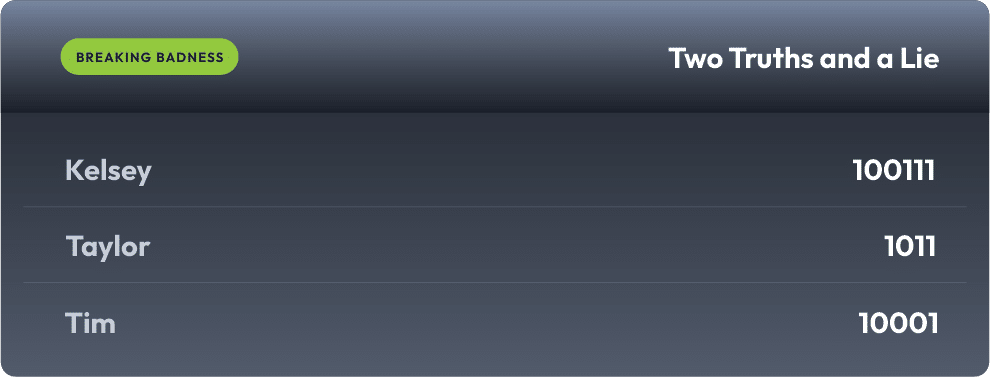
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Exclu-se You
[Taylor]: 5.5/10 Goodies
[Ian]: 2.5/10 Hoodies
Let Me Speak To Your Hypervisor
[Taylor]: 3.5/10 Hoodies
[Ian]: 0/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




