Coming up this week on Breaking Badness. Today we will cover: A Discussion On US and Iran Cyber Relations, Chinese Company Ticks Off US National Security Agencies, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
A Discussion On US and Iran Cyber Relations
- Keep calm and Threat Model on!
- Does your organization actually have any overlay with any Iranian infrastructure, businesses or interests?
- For example, if you’re defending a Saudi-Arabian oil organization you’re definitely at risk.
- One thing to keep in mind (although lower risk for small/medium organizations) is that sophisticated adversaries are notorious for compromising non-related networks and using them as footholds to conduct additional attacks from. So while you may not be affected directly by Iranian threat actors, it’s important to keep in mind that it’s not out of the realm of possibility your infrastructure could be leveraged by them. Once again, this is likely to be low risk.
- Iranian threat group’s TTPs are generally lower on the sophisticated side. We’ve seen account take over attacks, Shamoon malware (wiper), DDoS’ing and spearphishing. Your security controls should already address these types of attacks!
- Organizations that have a threat model and have already mapped their security controls/defenses against common attacks and sophisticated adversaries will generally be prepared for any Iranian threat group.
- Here is a cliff notes version of recent US-Iran cyber relations:
- Major players are of course NSA/CIA/US CyberCom/etc and Iran’s APT 33 (Refined Kitten) that targets aviation/military/energy and APT35 (Charming Kitten) who targets journalists, Persians living outside Iran and government officials. Then there is also OilRig (associated with ISMDoor, some other malware)—reportedly hacked by the Russian FSB with some tooling hijacked. Also there is a whole slew of unsophisticated defacement and skiddie groups in Iran—Dark Coders Team, Cyber Fighters, Cyber Army, you name it.
- The US has been performing cyber activities against Iran since 2006. 2009/2010 of course being when Stuxnet was discovered damaging the Natanz uranium enrichment facility.
- Iran has been operating itself since 2009—probably in response to Stuxnet—mostly targeting US industry instead of government with the first public defacement being of Twitter’s homepage by the Iranian Cyber Army.
- Since 2012 the US has admitted to infecting Iranian computer networks for intelligence gathering—the Flame virus was the first of these publicly reported. Iran replied with a DDoS against US banks. Late 2012 also brought the Shamoon virus that erased 3/4 of Saudi Aramco computers and had all data replaced with a burning American flag. It is important to note Iran didn’t take credit for this particular campaign.
- Lots of espionage mixed with corporate attacks up until 2016 with some indictments of Iranian hackers and a resurgence of the Shamoon virus again targeting Saudi petrochemical plants—culminating in an attempt to cause one of the plants to explode through a cyberattack.
- 2018 Iranian hackers crippled Atlanta’s city government network and the US warned that Iran was preparing for extensive attacks against US and EU governments leading to an early 2019 report from FireEye of a corporate campaign from Iran to steal login credentials. Microsoft also came out saying Iran had targeted over 200 companies in the last two years.
- Then, in April 2019 things really ramped up even more. Defacement of Iranian data centers with American flags, then Tehran claimed it dismantled CIA espionage campaign, then in June the US conducted a massive cyberattack against Iran in retaliation for attacks against oil tankers in the Strait and the downing of a US drone. It appears that the June attack was actually a precursor to a physical attack that was called off, but there’s still some debate around that.
- Then again this last September there was an attack the US carried out as a response to even more attacks on Saudi oil infrastructure. You can kind of see the pattern here. Since then it’s just been a little bit more of the same.
- We’re starting to see more and more cyberattacks being used to discourage or outright avoid a kinetic confrontation. We’ve definitely crested having more cyber operations than physical at this point since it’s a no-loss game. I think with the elevated militaristic diction in the cyber space though we’ll start to see more physical attacks on cyber operations—like we saw with the hackers’ office in Gaza. I wouldn’t be surprised if drone strikes on data centers or startup offices because they had hackers or malicious code running on servers became common. It’s a weird space and cyber operations really remove humanity from the situation, gamify the actions, and then tie that in with drones. I’m hoping people are putting sane rules of engagement in place for this different theater all together.
Chinese Company Ticks Off US National Security Agencies
- In terms of what CheckPoint found in their report, lots of bad. Really bad. I didn’t realize just how widespread this app is too—they have 500 million active daily users. It was the most downloaded app in the US in 2019. It seemed like overnight I started seeing every screen on the train replaced with TikTok instead of Instagram if the person was under 25. That means there are a lot of vulnerable users out there.
- The most glaring vulnerability to me was the SMS Link Spoofing. You can send—from the TikTok site—a legitimate, from TikTok message with a link of your choice. So they’ll get a message from TikTok, click the link to any attacker controlled page—or install an APK of an attacker’s choosing. There is also an open redirect on their login page which opens a whole host of possibilities. The only validation is as long as the domain ends in tiktok[.]com you can redirect there so anyone can register malicious-tiktok[.]com and put it to use. Couples with a XSS vulnerability on the ads portion of their page and CheckPoint discovered that they could execute any action on behalf of the user as long as they clicked the malicious link sent. Create videos, delete videos, make follows, expose sensitive user data.
- These vulnerabilities, according to CheckPoint, have not been exploited in the wild.
- TikTok has released some fixes according to CheckPoint, but I don’t really like the extent of the permissions an app like TikTok requests on my phone. I’ve got too much of my life in there. But also I don’t feel that TikTok is for me—this is the social app for the younger generation. They are a lot less paranoid about such things than the rest of us.
- Chad’s words of wisdom: don’t click any random links that get sent to you. Monitor permissions requested. Don’t install any weird APKs suggested from the Play Store because it’s a malware playground at this point.
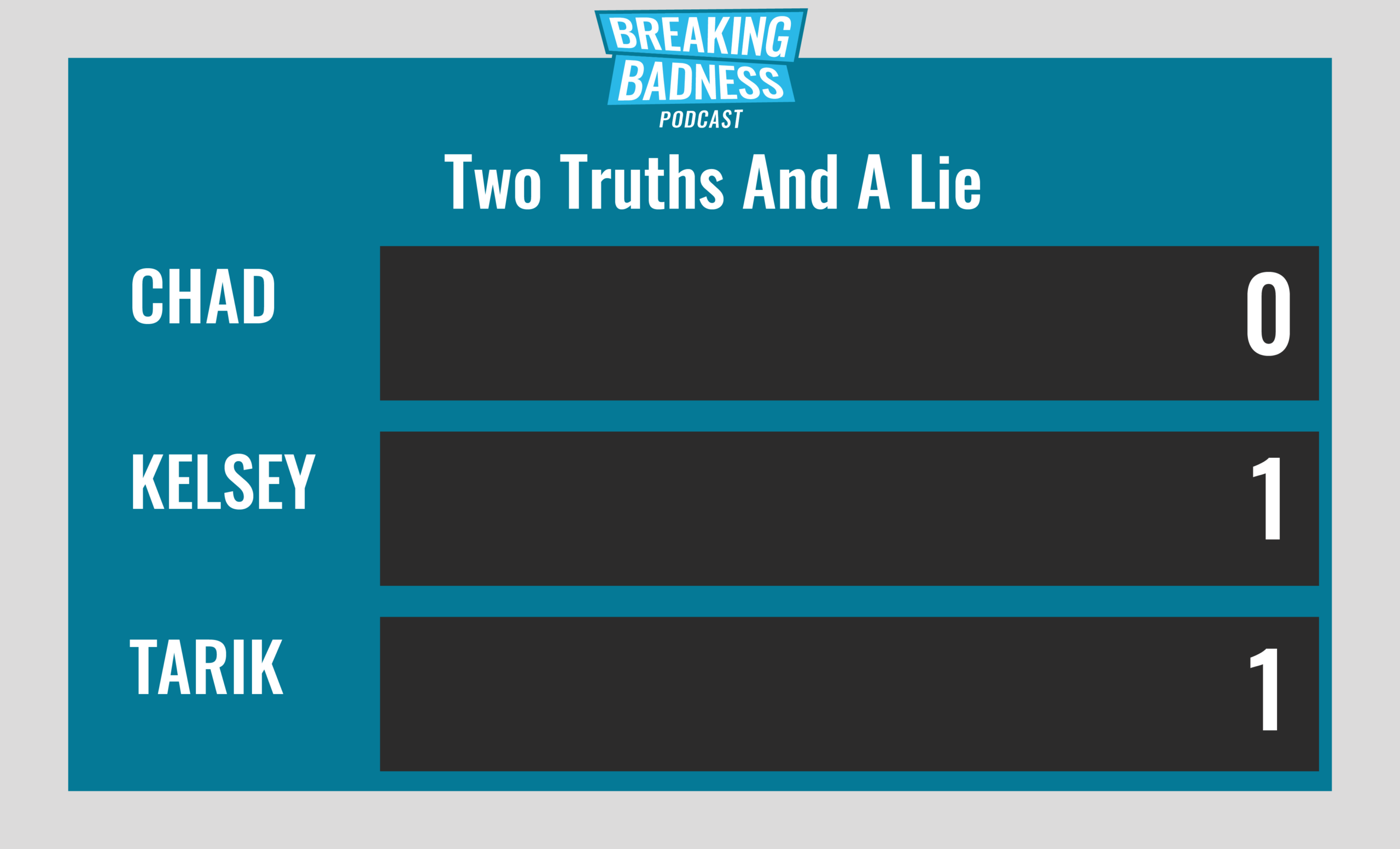
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
A Discussion On US and Iran Cyber Relations
[Chad]: 3/10 Hoodies
[Tarik]: 5.5/10 Hoodies
Chinese Company Ticks Off US National Security Agencies
[Chad]: 7/10 Hoodies
[Tarik]: 6.5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




