Coming up this week on Breaking Badness. Today we discuss: The Business of V2V: Threat Actors Capitalize on Coronavirus Epidemic, I Smell a RAT: TA505 Returns from Winter Vacation, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
The Business of V2V: Threat Actors Capitalize on Coronavirus Epidemic
- The emails in this case were looking to exploit—as these so often do—people on a type of disability welfare in a few Japanese prefectures. This is up there with the social security number scam calls telling you your services will be turned off and what not. Basically take a current disaster or epidemic then couple that with people in need or relying on one part of a social system, then tell them that reliance is in jeopardy and get them to open a malicious document.
- In the case of Emotet this is slightly interesting for the Japanese market since normally they focus on the subjects of corporate payment and invoicing to get people to open the documents.
- This all starts with the age old malicious Word document. Open it up, it says hey, enable macros for a good time, then you do and it infects your machine and the fun begins. The usual pattern with the Emotet infection occurs: chain of dropping a copy, installing a service, communicating to the C2, update, start network infection and credential thieving.
- I’m curious to see how things light up for the Olympics in Tokyo. Japan has already sent out a warning that cyberattacks should be up starting in the next couple of months. We saw it with the Sochi Olympics and it’s only going to get more and more prominent with every event. Anything that grabs people’s interest and can be leveraged to get them to open that document.
- You just have to assume that big upcoming events are going to be used to spread commodity malware and for some cyber criminals to get some quick cash. At this point though with the World Cup—and you know I’m a huge football fan—I’m sure some criminal is going to send out an Excel document with macros enabled that claims to have every worker’s name and where to donate money to their families or something. Every tragedy at this point is being exploited.
I Smell a RAT: TA505 Returns from Winter Vacation
- TA505 is a threat group that we can thank Proofpoint for tracking. They’re associated with some of our favorite malware threats, such as Dridex and the Locky ransomware. As you can imagine, they are obviously extremely financially motivated!
- This group is not only associated with Dridex and Locky, but they’ve also been associated with more surgical deliveries of RAT’s that they didn’t develop specifically, such as FlawedAmmy, Trick and GlobeImposter. They’ve been at the forefront of using different attack vectors and bypasses to deliver these tools. We can rate this threat group as definitely high impact in the global market.
- Word or Publisher document attachments with macros acting as a stage 1 downloader that grabbed additional malware to execute. In this campaign, Proofpoint’s researchers dubbed this specific new malware “ServHelper” and had two variants detected in the wild: “tunnel” and “downloader”.
- Proofpoint’s researchers dubbed the new malware family “ServHelper” because of a DLL filename associated with the malware.
- What’s interesting is that the malware is written in Delphi, which is a really old language and what many consider a dying language. Malware written in C/C++, Python, Go or .NET are the most common generally.
- In regards to the two variants: Tunnel and Downloader.
- The Tunnel variants have a lot more functionality, such as establishing reverse SSH tunnels serving up RDP over it.
- The Downloader variants lack the RDP functionality, but include the capability of having an SSH reverse tunnel back to the attacker C2 and obviously by the name include download & execute functionality.
- The ServHelper malware also shows how attackers are adding encryption capabilities where they can now, as all C2 operations are done over HTTPS. So detecting C2 beaconing is more difficult here based on HTTPS communication.
- Reading into the ServHelpers capabilities, specifically credential dumping from Web Browsers really indicates this is useful for accessing people’s financial systems. Or leveraging their access to their e-mail accounts to access financial data of their victims.
- Fortunately this malware follows a really easily detectable multi-stage pattern that we see all too often: Word macro to downloader to binary execution and no exploit code. I would have a reasonably high confidence in behavior based AV solutions to be able to detect this one since this attack pattern is really common.
- Now, that being said, the threat group behind this malware is really targeting individuals and not organizations that have the resources for a solid AV. So while the malware may not be elite to those of us that defend networks, it’s still going to be effective against normal consumers out there. We can glean that from how much financial damages this threat group has been responsible for.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
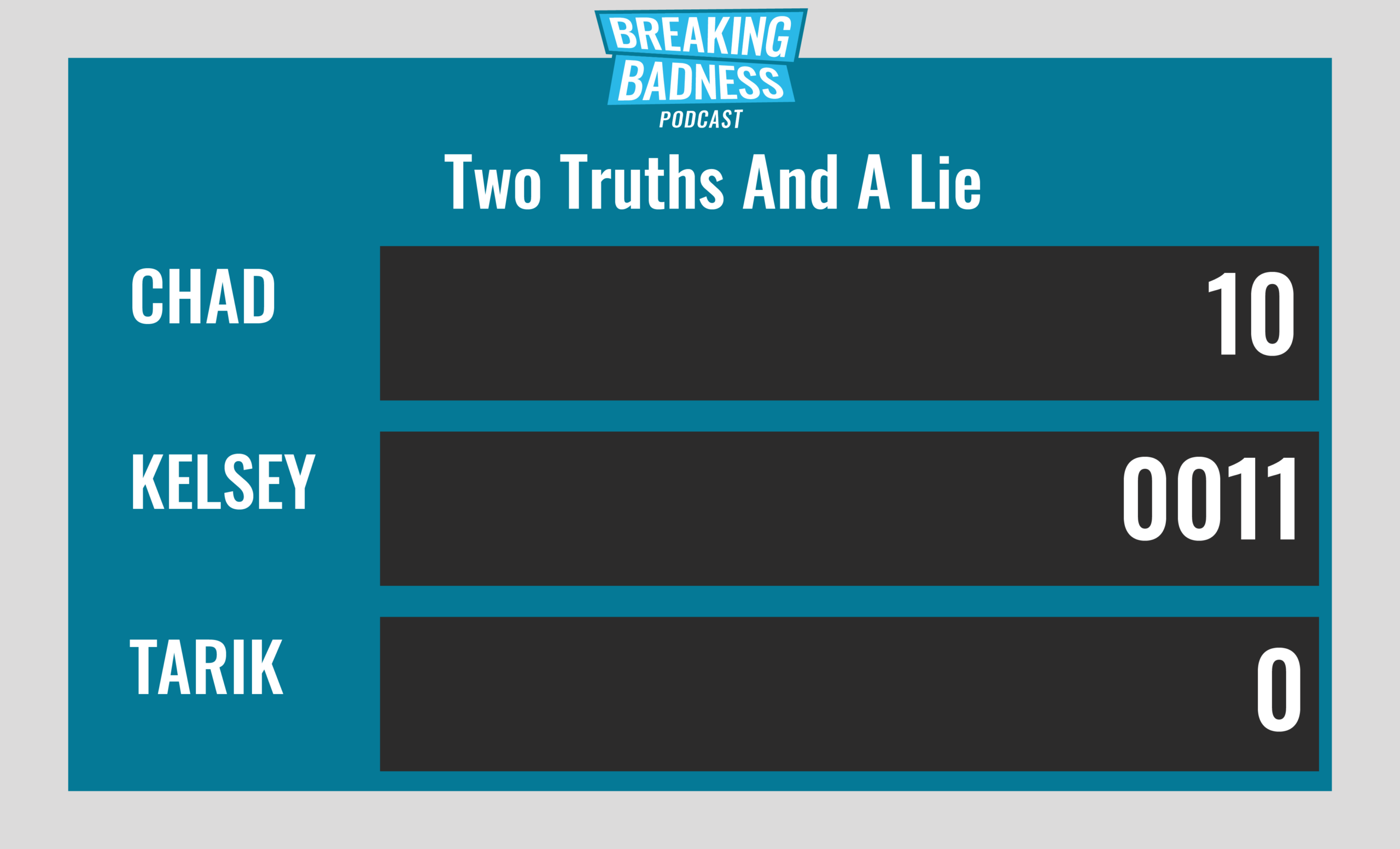
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Business of V2V: Threat Actors Capitalize on Coronavirus Epidemic
[Chad]: 5/10 Hoodies
[Tarik]: 6.5/10 Hoodies
I Smell a RAT: TA505 Returns from Winter Vacation
[Chad]: 6/10 Hoodies
[Tarik]: 7/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




