Coming up this week on Breaking Badness. Today we discuss: More Than A One TrickBot Pony, Worse for Ransomware, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
More Than A One TrickBot Pony
- TrickBot has been around since 2016, and is one of the premier banking Trojans that’s targeted Windows machines. TrickBot has been seen to do credential harvesting for banking credentials using Mimikatz and the C2 traffic for the malware is typically seen only on compromised home wireless routers with weaponized vulnerabilities.
- The security researchers at IBM X-Force initially made the discovery of TrickBot dropping TrickMo, which is a malicious Android application from a Tweet made by the German CERT team. IBM reports that this initially was discovered in September of 2019 and development of TrickMo is likely still continuing.
- Victims include Windows OS users that have already been compromised by the TrickBot malware. From there, if they have the appropriate version/build (or even possibly using the German language pack for Windows) they’ll be prompted for their mobile phone number and what type of mobile OS they use. If they fill it out and select Android, they then get a prompt masquerading as their own financial institution asking them to download TrickMo. It’s a really ingenious way of leveraging your existing foothold on a victim and expanding it for more financial gain.
- 2FA is becoming the gold standard for anti-fraud/account protections for all services nowadays. As such, attackers are devising means to bypass it. TrickMo has the capability of intercepting SMS messages from the victim, post-installation. Since SMS is one of the many means of 2FA, this is one way TrickMo can bypass 2FA. Another is via TAN codes, which are application targeted specific one-time use codes. TrickMo has the ability to intercept those and replay them back to the attacker.
- What’s interesting is that according to IBM, the victims appear to be only German speaking individuals who have already been previously infected by TrickBot on their Windows computer. So, you have to have been previously compromised and fall victim for the next stage of phishing to download/install TrickMo.
- This campaign is inline with the TrickBot authors motives, which is financial gain. What’s interesting is that this is making that bridged connection between the Desktop and Mobile space from one attack. This reminds me of the MacOS Wirelurker malware that I investigated awhile back.
- It’s very concerning when you have malware that can make a large impact against individuals and financial institutions essentially jump from one medium to another, like going from the Desktop to the Mobile space in one attack. Since malware authors definitely pull novel and new ideas from each other, we can definitely expect other threats to mimic this attack pattern.
Worse for Ransomware
- Ryuk ransomware has been around since 2018 and is attributed to the same Russian-based group that brought us TrickBot. From an operational perspective it has been used primarily to target enterprise environments where it does the usual ransomware thing—encrypt files and extort some money paid in bitcoin. They also always use the name of an esoteric actor or director for their email. Ryuk is usually distributed after a TrickBot infection and is thought to be the successor of the popular Hermes ransomware. To date of known BTC addresses, millions of dollars have been paid to decrypt files that Ryuk has encrypted.
- Ryuk is currently doing the same old targeting enterprise environments, but now targeting hospital care facilities. A number of journalists and researchers have reached out and asked these actors to cease for the time being, but they have refused to do so. It makes sense from a horrible person point of view—if lives are on the line then the hospitals are more likely to pay up fast and not take any time deliberating or contacting security experts.
- The impact is clear, real people will die. That’s what it comes down to here. I don’t know enough about medical equipment security but I have seen some talks that equipment is very poorly secured often wide open without any credentials and on insecure networks to boot. I really hope that the ventilators aren’t networked because these actors will try to get money any way they can.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
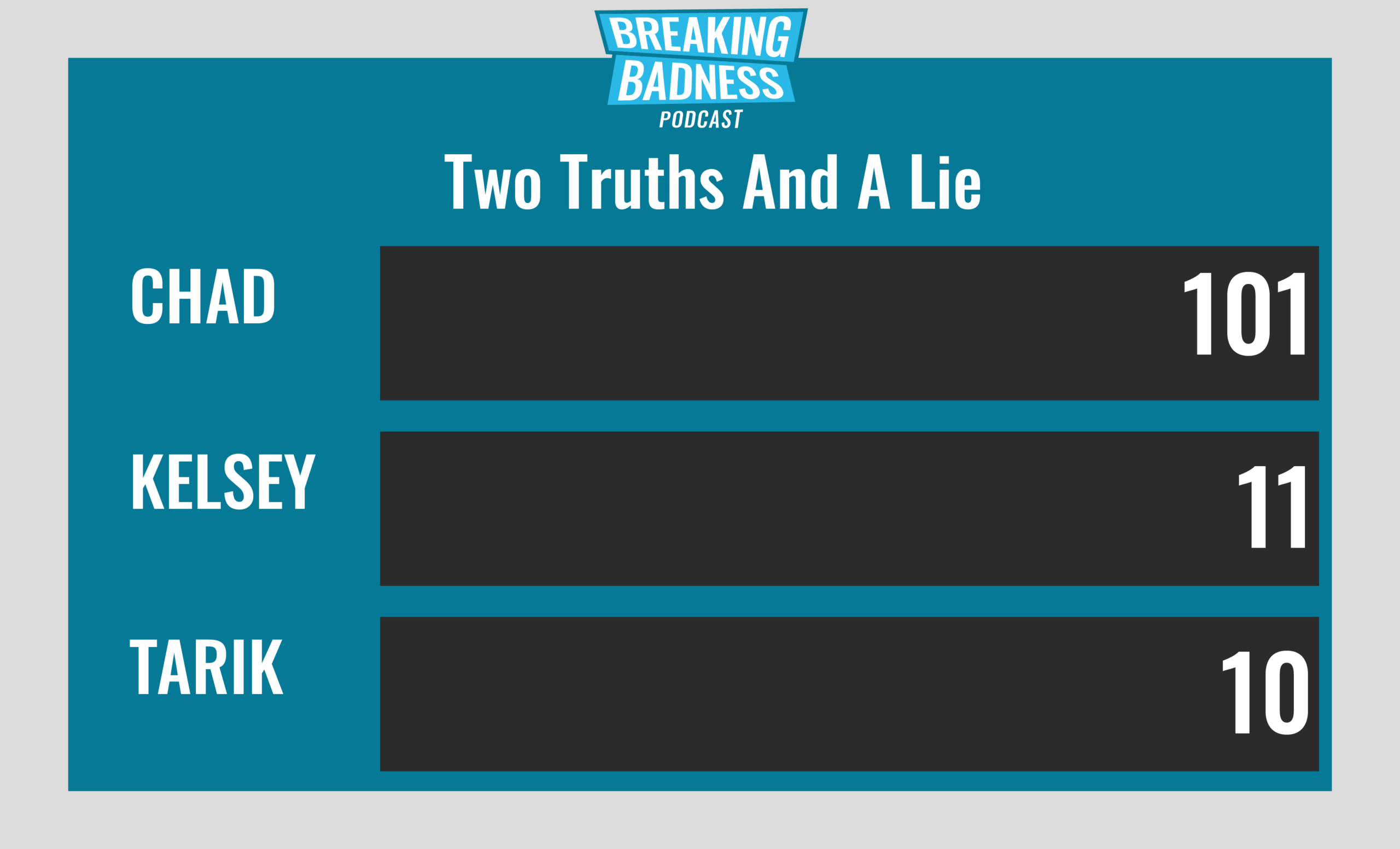
Current Scoreboard
This Week’s Hoodie/Goodie Scale
More Than A One TrickBot Pony
[Chad]: 8/10 Hoodies
[Tarik]: 8/10 Hoodies
Worse for Ransomware
[Chad]: 10/10 Hoodies
[Tarik]: 10/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




