Coming up this week on Breaking Badness. Today we discuss: Threat Actors Pull Bait and Switch, Crime Doesn’t Payload, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Threat Actors Pull Bait and Switch
- Microsoft talks about how no one, not even security professionals, were really prepared for everyone to suddenly work from home and open up all these new endpoints to corporate networks. How that coupled with all of the fear around the virus has attackers really ramping up their work. This means so much opportunity for immature security on the networks of those working from home.
- There has not been a single country or language not targeted by a COVID-themed attack according to the Microsoft report. I kind of feel like they may have left out some minor island nations in their scope there, but needless to say it is definitely the majority of places. They said daily they see 60k attacks that are COVID themed.
- Microsoft observed nation-states targeting healthcare organizations especially—at least some that also do the cybercrime angle. They are also going after a lot of VPN and other gateway and edge devices. Typical weak spots here for them to pivot into people’s networks for espionage, cybercrime or whatever their intended goals are with their campaigns.
- Microsoft identified 60k messages per day, some 2300 unique phishing campaign pages, the always trendy Emotet and Trickbot now have over 75 variants in the wild using COVID-themed lures. Pretty much everyone is on the bandwagon now. Luckily today with our telemetry at DomainTools we are starting to see a slow, but still more than we usually see for any set of scams.
- All agencies have released something at this point. They are all talking about VPN vulnerabilities since that has been a big one with remote workers and also that there will be scams coming about stimulus payments and what not. If it happens in the world it is a scam target.
- Defenders at this point have just been seeing a barrage of attacks for the last several weeks. The volume has been insane, but everything stays the same and uses all the same tricks. The only major concern for me are the users that have a flat network at home and some other already infected device, but really you should have some endpoint protection on people’s devices—big shout out to all companies not doing bring your own device and actually securing the equipment they buy. If defenders are in the other sect of people there well, they are going to have a bad time either way.
Crime Doesn’t Payload
- xHelper is a recently popular Trojan malware that affects the Android mobile OS.
- Since it’s a Trojan, we’ve seen it in the wild oftentimes packed with those popular and always suspicious greyware applications. Stuff like: “Download this app to make your phone faster” that’s really common in the Android malware space.
- The capabilities of xHelper are exfiltration of victims phone metadata, like the IMEI number, model number and other data points used to generate a unique fingerprint for each victim.
- From there, xHelper has been seen in the wild dropping various implants on the victim phone for additional use. LeechP downloader and finally Triada were found recently, Triada specifically using exploits to escalate to root privileges on the victims phone.
- In a post-exploitation scenario with an Android APK bundled with xHelper, your phones metadata gets sent off to the domain ‘lp.cooktracking.com’, which has historically been hosted on either Amazon or GoDaddy infrastructure for the past year or so.
- After that, from what we have seen, there will be multistage malware payloads that get downloaded and executed on the victim’s phones ultimately leading to an attacker with administrator level access on the device. The attacker can then effectively choose what they want to do next: ransomware, spyware, etc.
- xHelper’s authors ensure there is a copy of it located on the victims phones system partition, that gets called on upon device reboot. So, if xHelper doesn’t detect itself, it simply reinstalls itself from a system partition.
- On top of that, according to really interesting research from Malwareytes, Google Play was also responsible for one of the mechanisms to trigger xHelper. They weren’t able to determine how that was being done but they noticed it behaviorally.
- Just like with 99% of malware out there, unless you have reversed it yourself then you’ll need to reimage and wipe your phone. xHelper does a great job of keeping itself on your system, so, a simple removal of the APK won’t cut it here.
- Mobile malware is always really concerning because of the amount of sensitive data we keep on our phones, and the huge potential for account hijacking with all of the other accounts we keep on our phones.
- Android malware isn’t new, and it hasn’t been going away despite the efforts of a lot of orgs.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
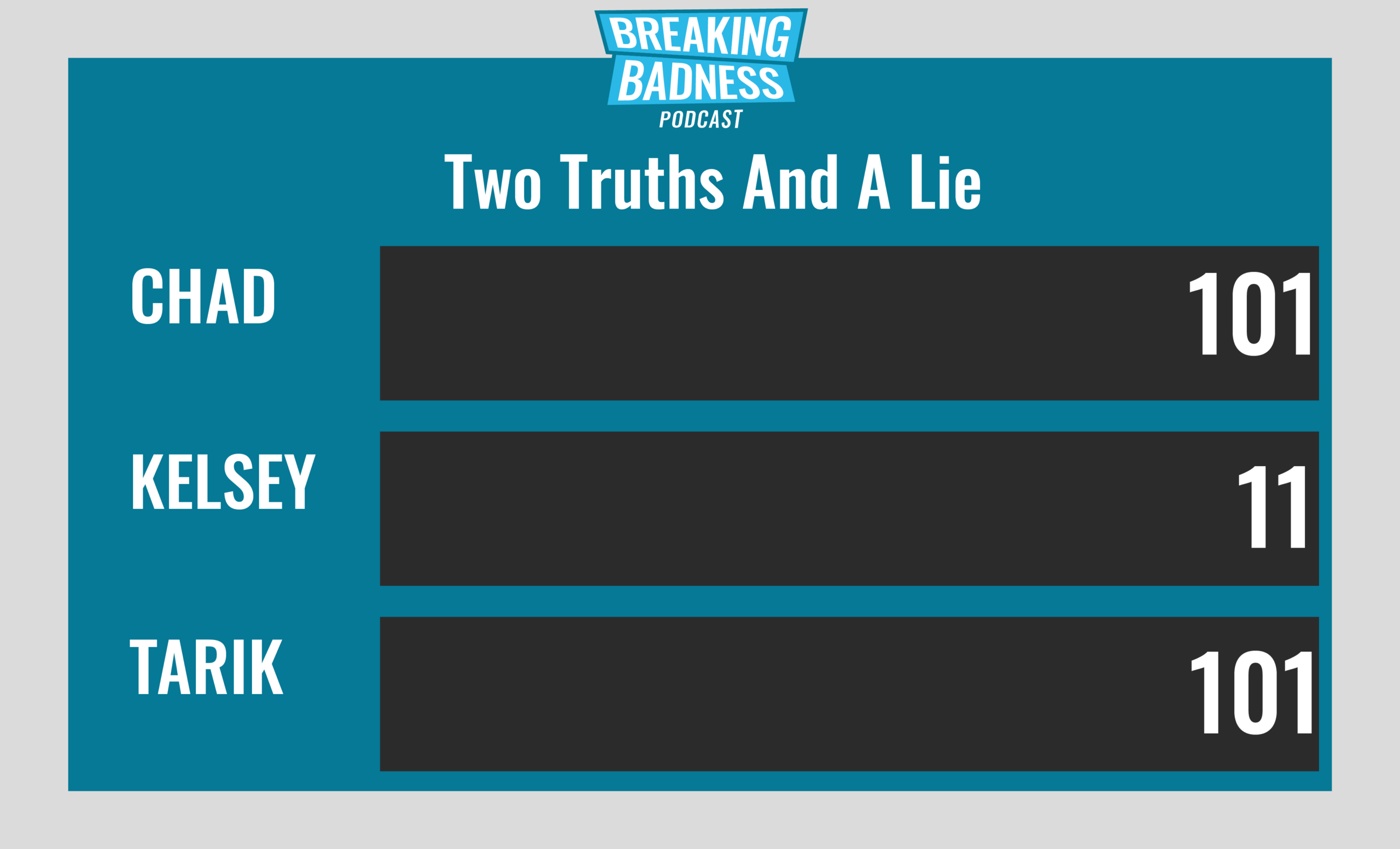
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Threat Actors Pull Bait and Switch
[Chad]: 8/10 Hoodies
[Tarik]: 10/10 Hoodies
Crime Doesn’t Payload
[Chad]: 7/10 Hoodies
[Tarik]: 7/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




