Coming up this week on Breaking Badness. Today we discuss: Threat Poet's Society, Why Not WiFi?, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Threat Poet's Society
- Talos researchers labeled this RAT accordingly due to the Shakespeare references in the malware. What’s interesting is that they don’t highlight that in their threat writeup, which would have been interesting to know. I ended up downloading a couple of the samples of PoetRAT, and saw references to COVID-19, but also found verses from Shakespeare's Sonnet 116 in the text body.
- It’s common to see obfuscation tools use song lyrics to scramble source code, especially with VB Script used in malicious Word document attacks.
- From the attacker’s motivations, we have a really specific and targeted campaign against citizens of Azerbaijan. Although the attackers are specifically targeting Azerbaijan citizens, the industries and organizations being spoofed are pretty large in scope: government agencies and even private sector companies specializing in SCADA systems.
- Based on the capabilities of PoetRAT, it was also pretty broad in what it could do: keylogging, password stealing from the common browsers and overall reverse shell functionality.
- These threat actors behind PoetRAT took several angles to build tripwired Word documents masquerading as Azerbaijan government organizations. In those, the attackers built a VB Macro that dropped the PoetRAT from the document itself. Generally, we see downloader functionality from macro attacks, but the actual PoetRAT python binary was embedded in the document.
- Talos also noticed two other campaigns, both coronavirus themed both kicking off in April of this year. One side campaign was a specific phishing site attempting to harvest credentials against Azerbaijan government employees.
- The attackers here built a clever lure here in that the initial document appears blurry and the only way to view it is by enabling macros. The document is also watermarked with the Defense R&D organization of India’s logo, which on initial glance makes the document look “more official”.
- So, after the victim opens the document the macro kicks off, dropping Poet on the box in a ZIP file called ‘smile.zip’.
- Regarding the RAT itself, the ‘smile’ ZIP file that gets dropped post-macro execution contains a Python interpreter and the actual RAT file. Generally when we see Python-based malware, it’s compiled together via Py2EXE or PyInstaller as a single static binary.
- A lot of Python based malware I’ve analyzed has anti-sandbox detecting functionality in it, and Poet is the same. One technique that Poet uses is determining the size of the disk of the victim it’s running on. If it’s less than 62GB, then it’s likely running in a VM and won’t continue running. It’s pretty clever because when you’re running malware in a VM, you generally don’t allocate more disk space than needed because you need to save space, and it’s generally a waste. Especially when you’re running your own Cuckoo cluster, you want as many VM’s as possible.
- After making it past the sandbox checks, Poet has several useful C2 commands for moving data around, downloading additional payloads or exfiltrating data. Exfiltration is done via FTP, and although an archaic transfer protocol, not a lot of networks really do proper egress filtering so this exfiltration channel will work most of the time.
- Poet also leverages the Python OpenCV library, which allows interfacing with your computer's camera API. So, broadly speaking, Poet is pretty sophisticated in what it can do.
- One obvious thought is this is done by a threat group or actor that wants to attack the Azerbaijan government, in some capacity.
- This is clearly espionage related, the attackers definitely are looking for as much data they can collect on individuals in the private and public sector of Azerbaijan. The PoetRAT campaign is casting a pretty large net and catching what they can.
Why Not WiFi?
- AgentTesla is a .NET based infostealer malware that has been around since I believe 2014ish. According to Cisco Talos it is from the same folks that brought us LokiBot and FormBook. They do some fun things in the past with steganography -- hiding of data in images—that was pretty novel at the time for malware as it would unpack a second more malicious executable from the stegoed images and run that.
- The new samples also execute on an image that has another executable that does a bunch of anti-sandboxing checks before running its final form. They do the usual stealing browser credentials and basically every bit of unique information they can find on the system, but then also now grab the credentials from all of the wireless profiles.
- Agent Tesla grabs the WiFi passwords for SSIDs by using the netsh tool that is on Windows that lets you configure networking from the shell. This then pulls in all of the profiles and iterates over them extracting all of the keys and such. What I didn’t remember and I still find kind of funny is that it then ships all of this information over email in plaintext. How much stolen data is just flying around on unencrypted email relays.
- Experts think this may be the first step of the authors setting up AgentTesla for spreading over wifi though I am not sure why they didn’t just bundle it all together with the capability if that is the case. I feel more like it is a capability for some more targeted attacks from specific compromised users.
- Infostealers are always a big problem. I would say that it is a bit of a crafty payload as before. Anything with stego is always interesting to me. I guess I would lean on Tarik for a more accurate hoody rating first though as our malware expert.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
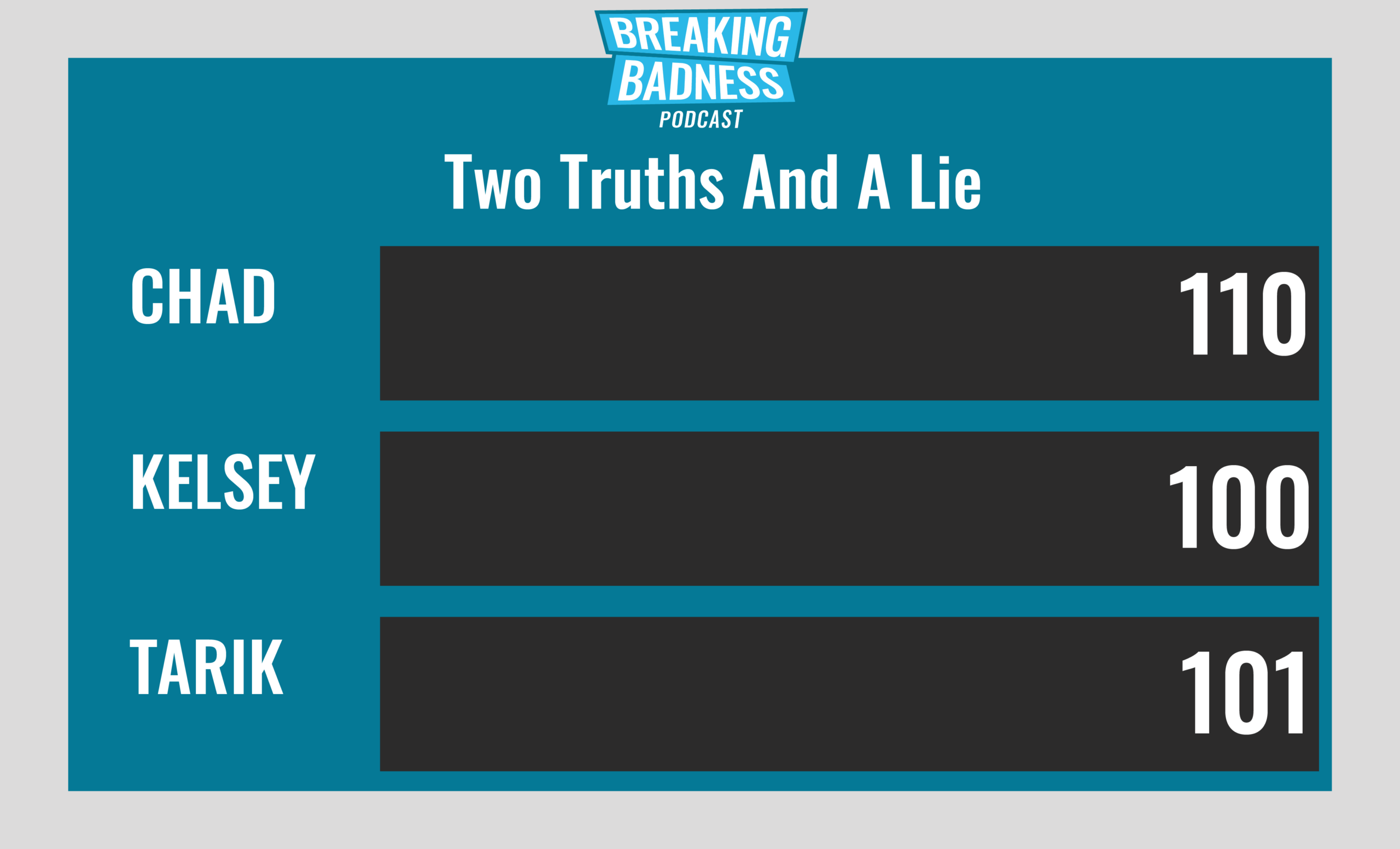
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Threat Poet's Society[Chad]: 6.5/10 Hoodies[Tarik]: 7/10 Hoodies
Why Not WiFi?[Chad]: 7/10 Hoodies[Tarik]: 7/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

