Coming up this week on Breaking Badness. Today we discuss: Promises are Like Pie Crust, Made to be Trojan, Utah Kicks Over the Traces, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Promises are Like Pie Crust, Made to be Trojan
- The Turla Group is an APT threat that’s based out of Russia. They’ve been spotted and associated with attacks all over the private, public and govt sectors. From a TTP perspective, they’ve been associated with recycling old malware from other threat groups and reusing those in their attacks which is a really interesting tactic. Malware such as PlugX and Winnti (which are associated with Chinese based threat groups) are examples.
- This type of tactic is excellent at misattribution due to how threat intelligence operates.
- Kaspersky recently found that the threat group behind Reductor targeting European citizens bundled a spoofed visa application service inside of an executable. It’s unknown how the executable has been distributed, which is interesting from an attacker perspective. Reductor is sophisticated in how it poisons other files as a persistence/spreader mechanism by injecting itself and also has the capabilities of traditional RAT malware.
- Back in 2019, Kaspersky found a new variant of the COMpfun malware that they labelled as Reductor. One of the key features about COMpfun and Reductor is their ability to intercept TLS encrypted communications and spread itself via mounted devices like network shares or USB drives.
- Based on the victimology of Reductor and COMPfun the researchers at Kaspersky were able to with a high likelihood of confidence say that the Turla group is associated.
- These are the stages of the malware and main module:
- Initial delivery is unknown, could be a via www page or email
- User runs the dropper EXE
- Reductor then enumerates all mounted devices, spreads itself via injecting into other PE’s or doc/pdfs
- Keylogging, screenshots are big capabilities with Reductor, like many traditional RATs.
- This malware trojan is a treasure trove of PII at risk from victims. Credentials for personal accounts, social media, medical, e-mail, etc are great pivot points into a full user compromise.
Utah Kicks Over the Traces
- So the model that Google and Apple proposed uses bluetooth low energy and cryptography in their protocol design to provide some privacy for users—it is based on the DP-3T specification. They are also proposing that their protocol operates on the operating system layer where some of the other more, shall we say invasive, protocols are designed to operate with special privileges above those of normal apps which opens up all kinds of security and privacy problems for the user right? According to the ACLU, the Google and Apple proposal mitigates a lot of glaring privacy and security risks by the way it is designed and protects user privacy. Google and Apple also want to call it an exposure notification service instead of a contact tracing system. Everything is a name and that sounds a lot less Big Brother. To go a bit further in here the way it works is by having a rolling key tied to the bluetooth low energy hardware address and that key then will change every 15-20 minutes on a rolling schedule, to put it simply. That’s the privacy preserving portion. Google and Apple also want to manage the application so they can pull it from their devices when done. They, rightfully, don’t trust the government to do this in any sane, secure, or noninvasive way. Germany, Italy, Austria and Switzerland are already falling in line with the DP-3T spec while the UK and France are not — even though a study by the European Union said it aligns with GDPR privacy standards. We have yet to see what happens here.
- The Healthy Together App they’re calling it collects GPS, cell tower triangulation, and Bluetooth data to pinpoint users along with all of the user’s personal information. The company behind the app is called Twenty Holdings and they make in-person social apps for people to find each other. The data collected is just shared with health workers and Twenty Holdings employees unless you test positive, then all your location, symptom and other data gets handed over to the state. It’s the kind of thing Apple and Google were trying to avoid by having their app use cryptographic identifiers to protect users.
- Utah officials are convinced that it will help them slow the spread and reopen the economy. I’m not sure what the cost is on that though if you end up giving up even more of your location and health data. I don’t like a model where you get to delete all of that after this is all over. I may be a bit of a tinfoil hat though.
- There’s no privacy terms. They say it’s opt-in, but what about when establishments start requiring you to have the app to shop or otherwise? Opt-in is a few heavy suggestions away from mandatory.
- Most countries are looking at the Apple/Google model. The UK is testing their own app right now that the NHS is working on. India also built their own.
- All these companies don’t have security in mind. Apple and Google have been doing this a long time and their model is a published, cryptographically sound way to alert users when they’ve come into contact with the infected AND maintain their data privacy. I guarantee you someone will find holes in these apps just like they did with the one in India. Security researchers are salivating at a chance. India’s published app basically allows you to find the location data of anyone who has tested positive for COVID. It’s a glaringly obvious mistake.
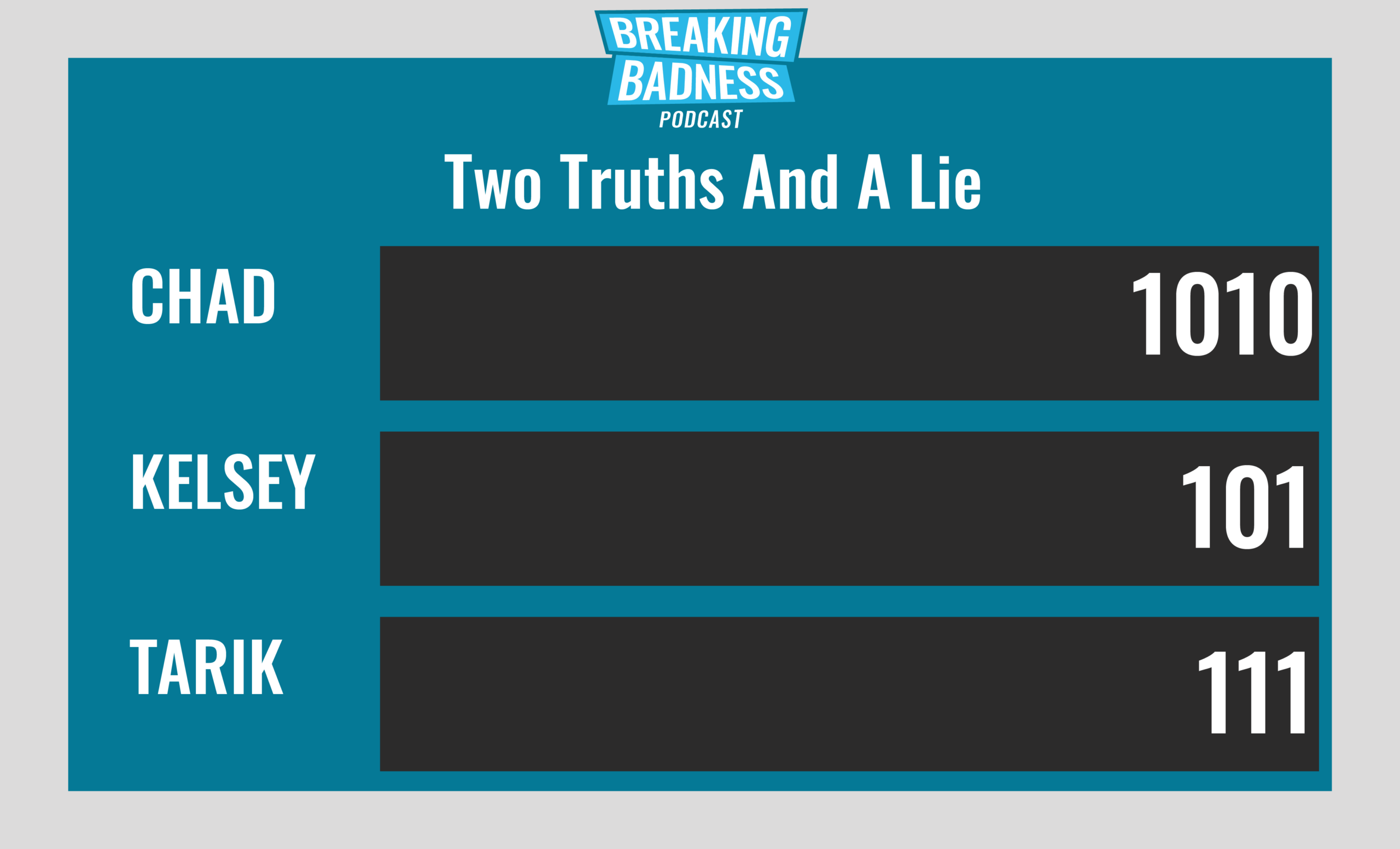
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Promises are Like Pie Crust, Made to be Trojan
[Chad]: 8.5/10 Hoodies
[Tarik]: 8.5/10 Hoodies
Utah Kicks Over the Traces
[Chad]: 10/10 Hoodies
[Tarik]: 10/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




