Coming up this week on Breaking Badness. Today we discuss: Inkredible Octopus Scanner Malware Spread Via Supply Chain Attack, Unc0ver Dials Up Jailbreaking Tool for Every Single iPhone, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Inkredible Octopus Scanner Malware Spread Via Supply Chain Attack
- This malware was brought up to the GitHub Security Incident Response Team by a researcher that goes by JJ.
- JJ shared quite a bit with GitHub, he said that there was a number of NetBeans projects—which is a Java IDE—that were serving up malware and that the C2 servers for the malware at the time were not active, but that 20 plus projects were being used to spread the virus. He also had pieced the malware apart for them.
- So this is one of the ever increasingly-popular supply chain attacks where someone goes after the CI/CD pipeline for a project as their attack vector and gains persistence by building their malware into the created artifacts or developer tooling. In a world where everything is more automated this is a good place for malware to hide. In this case Octopus Scanner is enumerating NetBeans projects, finding users’ directory, copying in a malicious payload, and making sure that every JAR file built—think of that like a Java binary—is then infected with Octopus Scanner so it can spread to new projects. The dropper it would add to those JARs would then drop a RAT. The malware disguises itself as a text file that is actually a JAR as well, so a bit of obfuscation to avoid detection. All in all I found it pretty clever. It was a fun write up and I’m surprised they found it before C2 infrastructure was spun up and more damage done. Props to JJ out there.
- The original infection vector is unknown, but it does drop that text file that is a JAR I was talking about, that pulls down the NetBeans infector, which then creates a backdoored build file that then infects all JARs built. Then that can pull down the RAT which communicates with the C2 and so on and so forth. I’m guessing that JJ found this because the RAT it pulls down is one that they analyzed in a 2019 blog post called the Backdoor Factory I believe. Was a good write up as well.
- GitHub deobfuscated the malware and wrote up some details on how they did that. Would recommend reading for any reverse engineer out there.
- GitHub is obviously a massive boon to the open source community. Typically with how things work you have to put in a pull request to get your changes merged into any big project and hopefully people are paying attention to any changes to build processes there. However if someone is able to compromise this process it’s a huge concern right, especially if it’s a big project. Starting small on something like some NetBeans IDE repositories and slowly moving into bigger projects may be a way that these supply chain attacks evolve—kind of like how we see attackers infiltrating tertiary vendors to slowly work their way laterally into their final target’s network. These are complicated attacks though and a sign of a sophisticated attacker.
- Attacks like this are high risk, high reward I guess. If your pull request gets through you’ve got access to A LOT of developer machines, people with credentials to all kinds of projects. A lot of people blindly trust the packages they import as well and the projects they use so the impact here is massive. Supply chain attacks are hot right now for that reason. Couple that with so much of the build process abstracted away now in automation and you could potentially sneak into a lot more projects after you have a RAT on one trusted developer’s machine. The impact here is massive if it works. Luckily in this case we’ve got people like JJ keeping an eye out.
Unc0ver Dials Up Jailbreaking Tool for Every Single iPhone
- The unc0ver hacking team is a group of people who are focused on jailbreaking iOS devices, including iPhones, IPads, and Apple TVs. They have been around for the past few years, and currently have 11 members.
- Jailbreaking works by exploiting flaws in iOS to grant users full control over their devices. This allows iOS users to access new or additional customization and install otherwise prohibited apps which could make use of the hardware in new ways.
- One of the historic strengths of iOS has been its security. The device itself is quite locked-down and you can only do what Apple allows you to do. That’s fine as long as you want to play inside of Apple’s walled garden, so-to-speak. Jailbreaking the device can give you more power to do what you want, but it also comes with limitations. First, some Apple services may stop working when you jailbreak. Second, the software you install has no guarantees to do what it claims it does. If malware is installed onto a jailbroken phone, it has access to all data and files on that phone—including all other applications.
- The interesting thing here actually isn’t around this 0day. It’s around the recently emerging patterns with 0days and iOS devices. First, an early beta version of iOS 14 was leaked in February. It first appeared in China and has been spreading throughout the hacker and security research communities since. Second, Zerodium, the bug-bounty platform platform said “We will NOT be acquiring any new Apple iOS LPE, Safari RCE, or sandbox escapes for the next 2 to 3 months due to a high number of submissions related to these vectors.” Third, don’t forget about CheckMa8, the permanently unpatchable hardware flaw in older iPhones.
- These three data points put together suggest to me that security researchers are putting some real time and energy into exploring iOS and finding new classes of vulnerabilities. That means that the 0day used currently in unc0ver most likely won’t be the last.
- This group hasn’t shared any information around the vulnerability that was exploited, other than to say it is a memory corruption and consumption issue.
- Hearing from folks who have used the unc0ver software—it is super easy to use and user friendly. It has been tested on a very large number of iOS devices and tested many different versions of iOS, going back to iOS11. It’s the software that my dad could use to jailbreak an iPhone.
- This 0day is very serious. Serious enough that Apple has already released a patch—version 13.5.1. It dropped this morning. Remember, that given the glut of other possible 0days out there for iOS waiting to emerge, I suspect we’ll be seeing a few of the patch releases come out over the next few months.
- Extra Related Links:
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
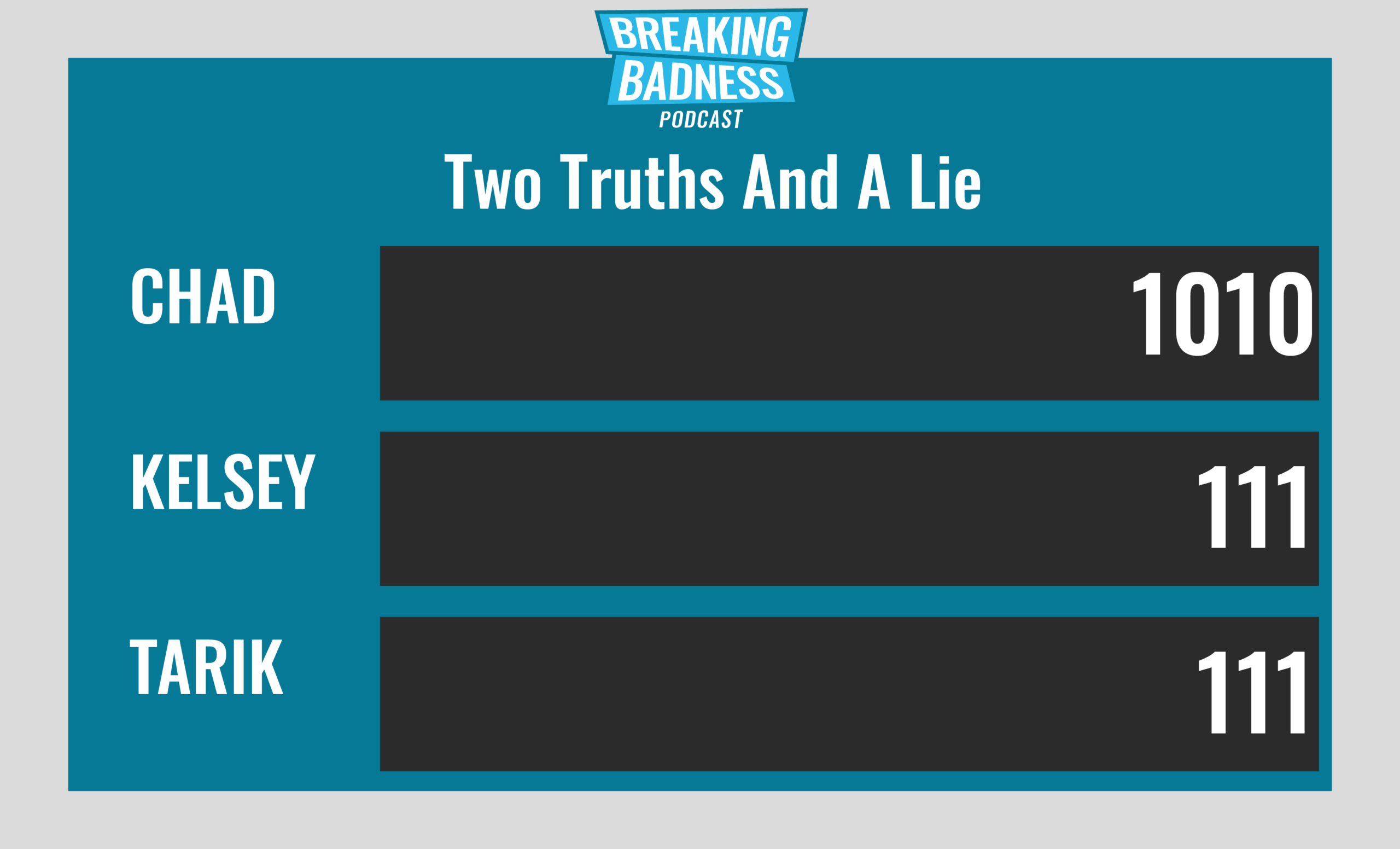
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Inkredible Octopus Scanner Malware Spread Via Supply Chain Attack
[Chad]: 6/10 Hoodies
[Sean]: 4/10 Hoodies
Unc0ver Dials Up Jailbreaking Tool for Every Single iPhone
[Chad]: 8/10 Hoodies
[Sean]: 8/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




