Coming up this week on Breaking Badness. Today we discuss: How APT 27 Kept Government Targets Under Their Thumb Drive, Ransomware Leaves Government Contractor Mazed and Confused, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
How APT 27 Kept Government Targets Under Their Thumb Drive
- Goblin Panda is an APT group that’s been around since 2013, but really came out hot in 2014. They almost always are working in areas of the defense and government sectors, operating in Chinese interest, and love to attack Southeast Asia—particularly Vietnam. Typical TTPs are maldocs with training-related themes that drop an executable or sideload a DLL implant. Pretty typical stuff that we see from government threat actors. Due to their attack patterns some experts say that Goblin Panda is likely two separate entities that often are directed on similar missions in the region, but not always working on the same projects. They often make use of commodity malware like PlugX or their own NewCore RAT which is a modified version of an open source RAT that is popular in China.
- USBCulprit is something that researchers found that can copy itself to USB drives to move laterally. It requires the executable on the drive to be launched manually then it will gather a bunch of data and begin looking for other drives for exfiltration. Researchers believe the idea here is to get in through air gapped networks, but I would be honestly surprised if this was that successful. I haven’t been in many air gapped environments, but the few I have have had USB ports soldered closed or not even available. Perhaps they were targeting a very specific air gapped environment with this. Either way Kaspersky telemetry says that USBCulprit has been floating around since 2014.
- In terms of what happens once a victim’s machine has been compromised, it does some bootstrap work then goes ahead and looks to offload any data it has stolen. It is a really simple system whereby a text file named 1.txt tells the malware whether it should be copying data to or from a USB drive, then a 2.txt file which says whether or not the malware should try to move laterally. Due to those simple mechanisms, researchers were able to infer quite a few things from their analysis.
- In Kaspersky’s code analysis, they observed what they dubbed RedCore and BlueCore. Furthermore they could also tell by the lack of network tooling and the code itself needing to be manually executed they believe this to be operated by a human handler. So this is likely, from that analysis, a mix of some espionage tooling and some technical chops.
- USBCulprit operates in three phases. There is the data gathering phase where it pulls in all documents of importance—DOC files, PDF, Excel spreadsheets you name it. Then from there the next phase is deciding whether it is transferring in or out. Then finally is whether or not it tries to infect laterally as we discussed before.
- Air gap is when you have a computer completely disconnected from any network interfaces. Typically this is for SCADA or certain research systems as a network security measure. I would guess they were attempting to go after some defense systems with this attack. Really surprised though that whoever is running their defense networks would allow for USB drives.
- Victims include all Southeast Asian countries. Vietnam being the majority with some dips into Laos and Thailand.
Ransomware Leaves Government Contractor Mazed and Confused
- Maze has been a ransomware that’s been around since roughly 2019. It originally started out as a variant of the ChaCha ransomware. It’s generally also been seen in the wild attacking private and government organizations in America, Europe, Asia and Australia. According to Palo Alto’s Unit42, we’ve also observed Maze being distributed via the Spelevo Exploit Kit.
- Maze is easily available on cybercrime markets, and operates under an affiliate model which allows the Maze operators to get a chunk of profits for each threat actor that purchases/uses their ransomware.
- Maze has been seen being distributed several different ways, such as exploit kits via drive by attacks or even emails. Maze is also associated with various exploits, one of the most popular being the recent Pulse VPN RCE.
- Once a foothold has been established in the victims network, usually a single workstation, Maze tries to obtain privileges and uses those for lateral movement and begins it’s encryption routines on all mounted drives. One big thing that’s different with Maze is that before it’s encryption routines kick off, Maze has been seen doing data exfiltration of said files. We’ve seen some of the more high impact ransomware starting to use this new technique to really help buff up their coercion into getting a victim to pay the ransom.
- So, there really is a simple decision tree with Maze: pay to get the decryption key to unlock your files and/or pay to not get your sensitive files released to the public.
- In this case, Sky News disclosed that a military contractor (Westech International) for the US responsible for ICBM Minuteman 3 missiles have been compromised by the Maze ransomware.
- We know that some sensitive data has been exposed, including payroll and emails. Westech spokespeople confirmed this to Sky News. One really interesting note from Manidant, is that the Maze creators and groups using it are separate but they do have coordination between them.
- I’m always extremely concerned when military secrets get exposed to unauthorized groups, especially so trivially.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
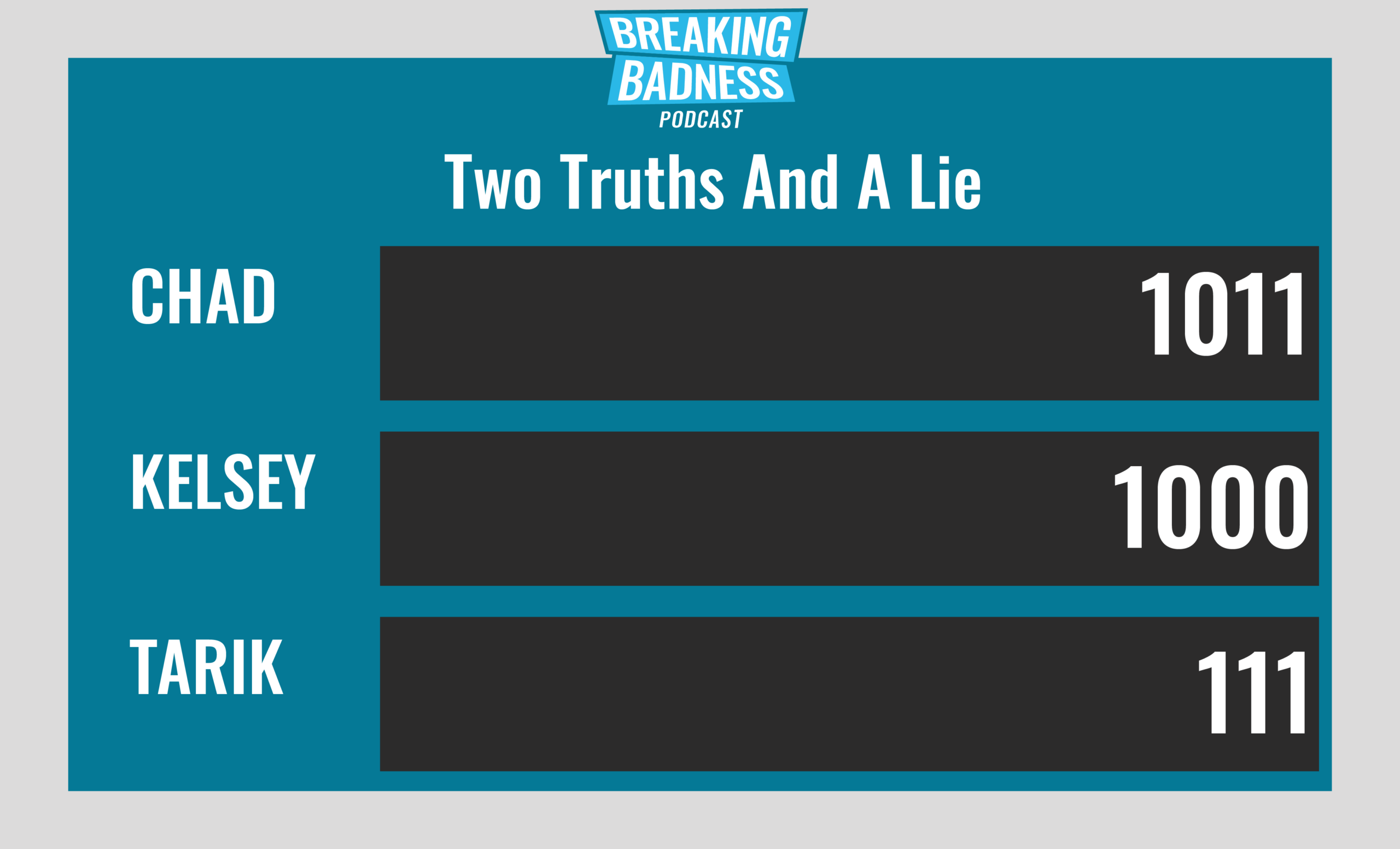
Current Scoreboard
This Week’s Hoodie/Goodie Scale
How APT 27 Kept Government Targets Under Their Thumb Drive
[Chad]: 8/10 Hoodies
[Tarik]: 8/10 Hoodies
Ransomware Leaves Government Contractor Mazed and Confused
[Chad]: 9/10 Hoodies
[Tarik]: 9/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




