Coming up this week on Breaking Badness. Today we discuss: Researchers Play An Old-Fashioned Game of Whack-An-InvisiMole, Banking Trojan Walking On Thin IcedID, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Researchers Play An Old-Fashioned Game of Whack-An-InvisiMole
- InvisiMole has been around since at least 2013, but was first discovered in 2018. Their backdoors have had lots of modular spying capabilities and they were kind of an unknown since they couldn’t tell how the tools had been installed on systems. Now we know they are kind of like a second stage crew. I say that because InvisiMole tooling now reported on by ESET research is found only after Primitive Bear, also known as Gamaredon, has infiltrated a network. So this pro-Russiian group infiltrates, sets up some tooling, then, InvisiMole comes to hang out and do some spying, mostly targeting Eastern European states, diplomatic missions and that sort of thing.
- Regarding their more recent campaign, pretty interesting stuff in that they use long execution chains, DNS tunneling for their C2, have updated their toolset for this latest round of attacks. Everything they have done—still focusing on military and diplomatic objectives in Eastern European countries—is designed to fly under the radar. Gamaredon comes in noisy, then these guys sneak around real slow and spy. It sounds like they may be a specific and tailored, more sophisticated group from how the researchers describe it.
- So we’ve actually talked about Pteredo in a previous podcast. That’s the initial infection vector and is from the Gamaredon group. That was where this piece of the puzzle fell into place. Once they spotted that bit of malware bringing in the InvisiMole tool set they knew the two groups had to be linked. It looks to them like high value targets get “upgraded” to InvisiMole once they are found to be more useful.
- To move laterally through networks, InvisiMole uses BlueKeep and EternalBlue—and I’m sure they’ll be adding CoronaBlue to that soon as well. The other method and the one that is really interesting is they take benign documents from the place they have infiltrated and then add maliciousness to those and redistribute them. This is particularly nefarious since most people will trust documents pulled from their own file server. I would probably open it without a thought to be honest. Just like I’d open this episode’s planning notes if you emailed it over to me on the company drive without a thought. They also infect software installers on the networks they infiltrate so you can imagine GroupPolicy updating WebEx or something on everyone’s machines, but it’s an infected installer that drops another payload as well.
- This is another one of those where unless you are an Eastern European nation with diplomatic and military interests that need protecting it isn’t anything to worry about. These are hyper-focused attacks with some real craft that I would be worried about if I worked in infosec in that space. For the everyday consumer of course this isn’t that big of a deal. As Tarik always goes on about, threat modeling, threat modeling, threat modeling—and in this case the model for most people says don’t concern yourself.
Banking Trojan Walking On Thin IcedID
- IceID (or BokBot) has been around since approximately September 2017 and they’ve really cemented themselves as a modular banking trojan. Tactically, IceID has always been a slick man in the browser type of malware. Once it successfully completes its initial attack, it uses the stolen information to take over banking accounts and automate fraudulent transactions. IceID has generally been seen in the wild being distributed as a second stage, usually being delivered by other malware like Emotet.
- IceID changes the executable it attempts to inject into. We’ve seen IceID generally inject itself into the Windows Service Host executable, but the variant detected by Juniper does against the Windows MSI installer executable. Process injection helps masquerade malware against behavior based AV systems, and that’s what IceID is doing but this time is changing its techniques.
- All of us in security have noticed the huge uptick in COVID-19 related cyber attacks, and the delivery mechanism for IceID is doing the same.
- We have a multi-stage malicious document masquerading as the US dept of labor with the subject line discussing FMLA and Medical Leave related to Covid19. Once the document is opened, and the macro is allowed to execute, an initial downloader is executed which then pulls a 2nd stage loader to download and execute IceID.
- One neat aspect that IceID’s 2nd stage loader looks for is looking for a URL in it’s array of C2’s that contains a PNG file and tags steganographically embedded in it titled ‘IDAT” which is the IceID data configuration file.
- Once IceID has it’s initial foothold on the victim’s machine, it extracts and decrypts the embedded binary in that PNG file. That binary then gets saved to the users temp application data folder, and a scheduled task is created to execute that. That’s how IceID establishes its persistence. This is also the 3rd stage loader for IceID.
- That 3rd stage loader calls out to a single C2 to pull another stenographically embedded incomplete binary from a domain, decrypts it, and executes it. This is where the new process injection target takes place. From there, IceID has the ability to inject and monitor your favorite web browser processes, decrypt your browser SSL connections and grab form data from a whitelist of popular ecommerce and banking sites to send back to the attacker.
- IceID represents some of the most sophisticated cybercrime malware out there, and we can see how effective it has been over the years. The fact that the malware authors continue to tune it should give us all concern.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
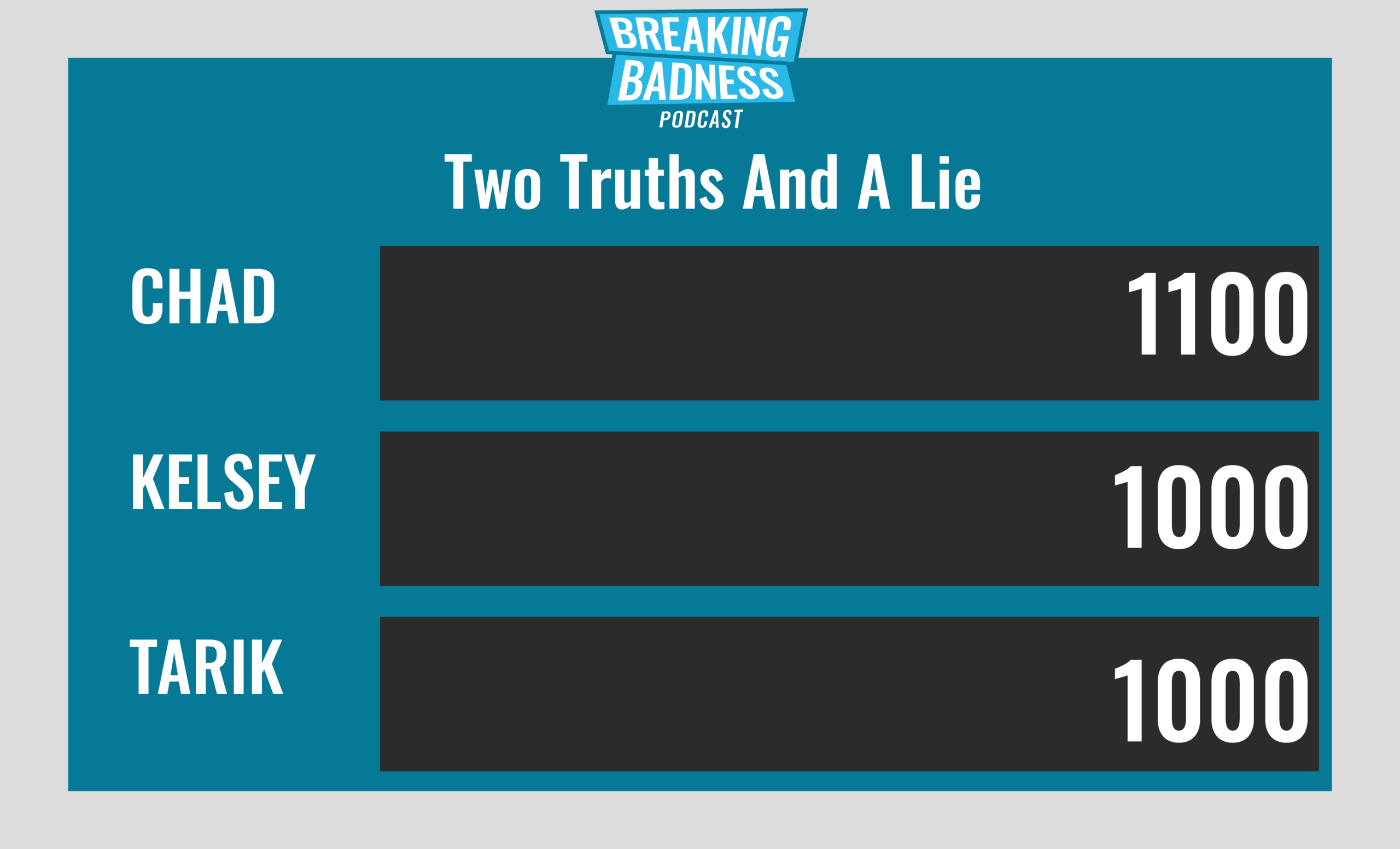
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Researchers Play An Old-Fashioned Game of Whack-An-InvisiMole
[Chad]: 7/10 Hoodies
[Tarik]: 7/10 Hoodies
Banking Trojan Walking On Thin IcedID
[Chad]: 9/10 Hoodies
[Tarik]: 9/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




