Coming up this week on Breaking Badness. Today we discuss: Why Keeping Your Database Secure Is Like Herding Cats, The Crux Of The MATA, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Why Keeping Your Database Secure Is Like Herding Cats
- It’s a new thing and kind of ridiculous in name. I hate to say it, but I kind of like it. I hope getting “meowed” is up there with getting “owned” at some point. I am guessing whoever is behind this believes they are doing a good thing by making enough noise that people will actually stop leaving their databases configured to sit on the public web without authentication.
- Security researcher Bob Diachenko said he discovered this attack while looking at the logs for UFO VPN which was one of the VPN providers who claimed they didn’t keep logs, then exposed their log database online without authentication.
- I can speculate on this attack’s objective. like I was saying that it’s someone who thinks they’re making a change for good here. Like when people were going around hacking cable modems and fixing the RCEs in them. This whole open database exposed to the world thing has to stop. It keeps happening time and again and we see this data either under the control of some ransomware actor or sold on cybercrime forums. As a consumer I would kind of rather have things deleted and the company feel some pain and secure their servers than know that there is a high likelihood my personal data is floating around somewhere. Not ideal, but not the worst thing in the world.
- Probably people who are meowing for it by running Elasticsearch or MongoDB publicly exposed. I think it is spreading to support more databases for deletion now too.
- 4000+ databases have been deleted and further research with honeypots show that this thing is pretty effective at finding new databases spun up. Shodan of course has thousands of these exposed databases just sitting there that they have discovered. Researchers try to reach out all the time to get people to shut them and they don’t get a response. Impact here is a lot of data just going missing.
- Make sure you don’t leave databases open to the Internet with no authentication. There really is no excuse for it. And if you do, well, meow is going to come and delete everything you worked on, but at least it won’t be sold to criminals.
The Crux Of The MATA
- Lazarus group is the APT group linked to the North Korean government.
- They’ve been around for several years, and also go by names like HIDDENCOBRA or Zinc. Lazarus has been associated with some of the most notorious attacks that we’ve seen in the news cycle for the past decade:
- 2014 Sony Breach
- 2017 WannaCry
- 2019 – Stole 49$m from Kuwaiti institution
- A malware framework is generally several programs bundled together to allow threat actors (or pentesters) to generate their own unique malware, handle communications between them and other tasks. One common framework we use everyday is MSF.
- What Kaspersky has uncovered is a custom malware framework that they discovered associated with the Lazarus group, which they’ve titled MATA (the malware authors call their infrastructure MataNet) and has payloads for each OS.
- The victims themselves aren’t geographically common. Victims have been identified in Germany, Poland, Turkey, India, S.Korea and Japan. There hasn’t been commonalities between the industries of the victims either.
- The versioning of MATA comes down to the victim OS, so MacOS, Windows and Linux. Each of these versions come bundled together with unique exploits and other tools used for post-exploitation for data exfiltration.
- Code reuse and other artifacts are a really great way to do threat attribution, and Kaspersky did that here. There are two specific and unique filenames that are used in MATA that are seen in previously associated Lazarus malware.
- Architecturally, MATA also shares commonalities with previous Lazarus malware in their configuration such as using session ID’s, sleep intervals, count of C2 addresses, etc. They aren’t identical, but this is a pattern similarity in their configuration.
- I don’t think this framework represents anything we should be dramatically concerned with. Attack frameworks are really popular and used by script kiddies, red team operations and APT. Everyone uses them. They’re just more effective than writing malware/infra by scratch every time.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
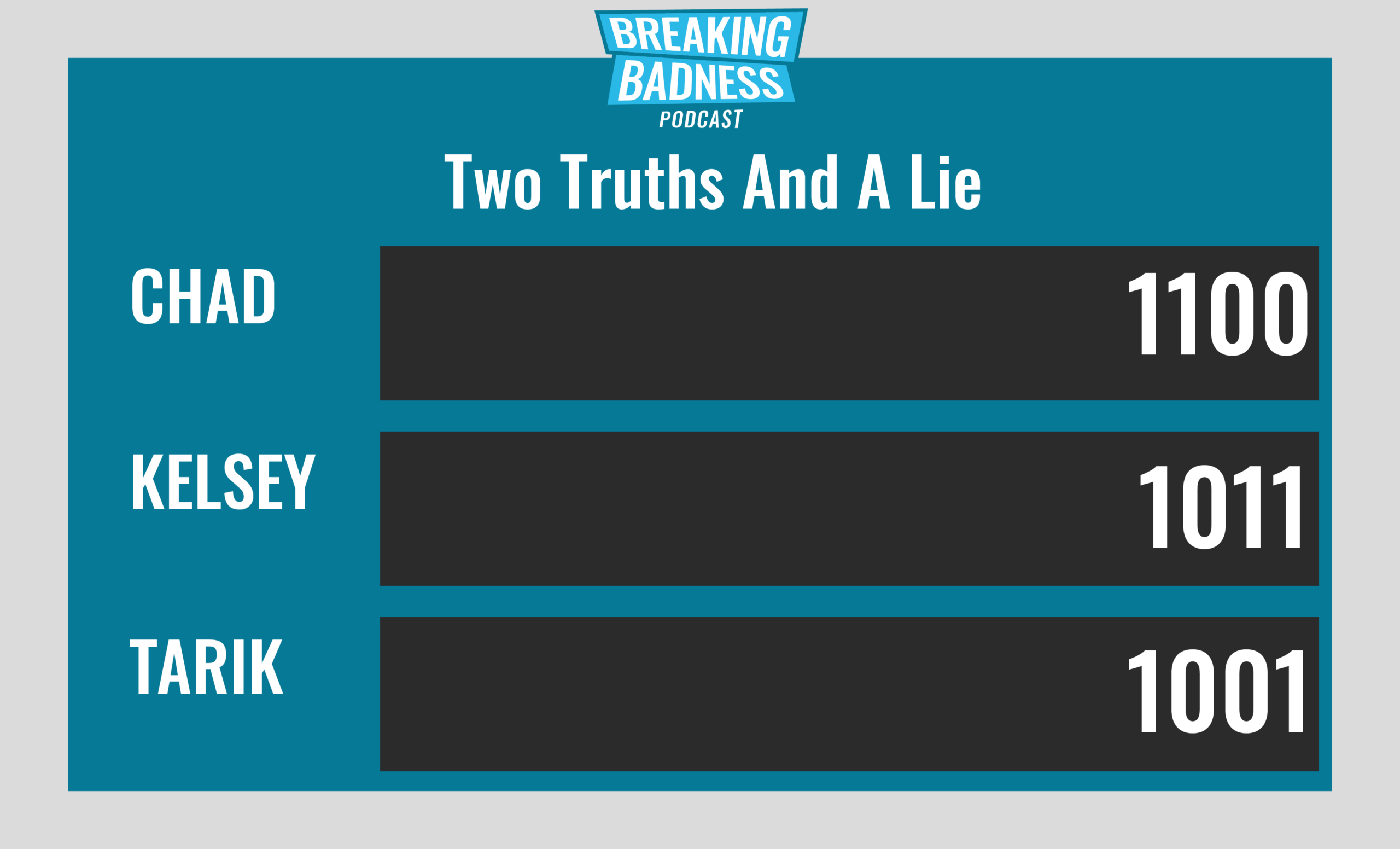
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Why Keeping Your Database Secure Is Like Herding Cats
[Chad]: 8/10 Hoodies
[Tarik]: 8/10 Hoodies
The Crux Of The MATA
[Chad]: 7/10 Hoodies
[Tarik]: 7/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




