Coming up this week on Breaking Badness. Today we discuss: For Crying Out Cloud!, Spearphishing Is When Preparation Meets Oppor-tuna-ty, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
For Crying Out Cloud!
- Doki is associated with the Ngrok botnet which refers to its use of the ngrok.io service that lets you generate short-lived URLs that will tunnel from the public internet to private infrastructure. Developers use it all the time, kind of like a reverse SSH tunnel for people that, well, don’t know how easy that is to set up. Anyways, this botnet scans for open Docker daemons that it can exploit, then creates a container that runs the common alpine image, then uses cURL to pull down more tooling. All pretty standard stuff, but since it’s using really common tools it’s hard to spot.
- The real fun bit to me here is the use of a Dogecoin address to generate C2 URLs—Dogecoin was kind of like a joke bitcoin that continues to stick around. It blew up among the 4chan crowd. Based upon money sent from the wallet, the malware will switch to a C2 based upon the Dogecoin transaction so the attacker here can change to any C2 they choose. It’s kind of like a DGA, but with a lot more control, right? It also hides as a kernel module which is slightly unique for Linux malware. This whole thing though, according to the report, is just a crone job, or schedule script that runs every minute. That seems to be the good place, for me, for hunting for this.
- This Doki bit is just an added capability from what I understand and no one had spotted this until now despite samples being on VirusTotal since January of 2020. Might have been that everyone was looking at COVID-madness, but yeah, it slipped under the radar.
- Using publicly available images has some advantages. Doki’s useless of the alpine image which alpine is a really stripped down version of Linux that is great for containerized applications since it helps you keep your images super small and just slimmed down to what you need. Since they are using alpine, probably the most common image out there, most administrators would just think it’s something normal that a developer is running. It is really hard to provide good introspection into every single container in a cloud environment. All these layers of abstraction help developers, but can provide hell for administrators.
- After the attackers have created their container, they go ahead and pull down, using cURL, another application every single developer uses, for pulling a file from a URL. Again, I make dozens of cURL calls per day as does every other developer that lives on the command line.
- This shows how much more people are concentrating on Linux malware. With everything moving to the cloud there are a lot of fresh targets out there running Linux. Couple that with these abstracted, complex systems like Kubernetes that a lot of administrators just aren’t adept at yet and you have a chance to exploit that learning gap as a malware author.
- People need to be making sure they aren’t leaving their Docker daemons exposed to the public Internet. Seems crazy to me that it is happening since most cloud providers make that difficult to do. This tells me that people are being sloppy and purposefully making their lives difficult.
Spearphishing Is When Preparation Meets Oppor-tuna-ty
- Several prominent verified Twitter users were seen tweeting a really simple and obvious cryptocurrency scam. This scam was the classic example of “Send us BTC and we’ll double it back to you”. As juvenile as this scam seems from a threat perspective, it was still wildly successful netting about 120k USD to the attackers.
- We now know that there were 3 individuals involved, two from the US and one from the UK. These threat actors are relatively young (all under 21 years old).
- In addition, we now know what extra data was involved in the attack, not just crypto scamming. We know that the personal DM’s from these compromised Twitter accounts were accessed, at least for a handful of users such as President Barack Obama.
- This attack was conducted in a really classic manner: social engineering over the phone masquerading as IT Support. This has been a staple of the SE attacker community for several years. It’s really effective at establishing trust with the victims, and as we can see here worked really well.
- We can safely assume Twitter is going to do a multi-step remediation plan to prevent this from happening again. Security controls such as Multi-Factor Authentication and network segmentation will dramatically reduce the risk of this specific type of attack from occurring again.
- Discord user #Kirk bragged about inside access to the Twitter admin panel used in the attack. It’s unclear if this is an insider threat that was paid off to provide access to the panel, as suggested in the Discord chat. We don’t have access to that data, and we may never.
- Bitcoin wallet tracing & IP address lead to a group of 3 individuals, two from Florida and one from the UK. Attackers are still focused on using BitCoin for cryptocurrency attacks, such as ransomware. One of the big risks, from an attacker perspective, is BitCoin’s lack of anonymity and privacy. All BitCoin transactions are publicly available, and in our own DomainTools research we highlight some of the transactions that took place. These public transactions to various wallets and CryptoExchanges allowed law enforcement to get the public identification for the wallets thus leading to a pretty solid conviction.
- International stability could have been impacted here. We can think about scenarios in which a VIP or countries leader that has access to a military might have tweeted about attacking another country. Human lives could have been significantly at risk here.
- Espionage / Blackmail leveraging against VIP’s. Especially in this day and age of political espionage having leverage over presidential candidates or other high valuable targets could have had major national security implications.
- Economic ramifications. The attackers had the ability to manipulate the stock market with some of the accounts they hijacked by tweeting out misleading information or directions a company would go.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
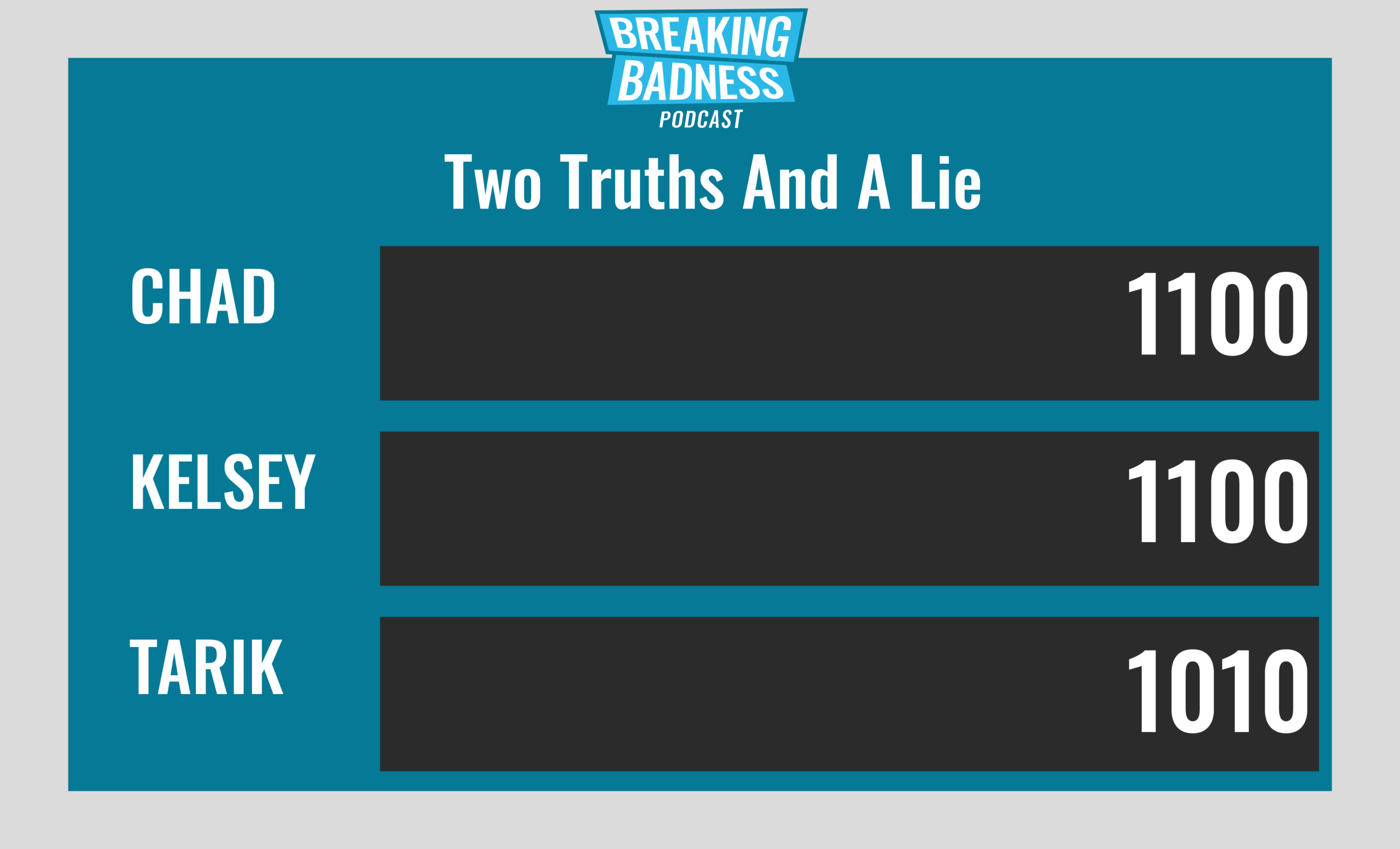
Current Scoreboard
This Week’s Hoodie/Goodie Scale
For Crying Out Cloud!
[Chad]: 6/10 Hoodies
[Tarik]: 7/10 Hoodies
Spearphishing Is When Preparation Meets Oppor-tuna-ty
[Chad]: 11/10 Hoodies
[Tarik]: 10/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




