Coming up this week on Breaking Badness. Today we discuss: The Pros and Favicons Of Homoglyphs, How OilRig is Rolling in the DoH, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
The Pros and Favicons Of Homoglyphs
- A favicon is the little icon in the top of your browser tab that changes for each page. They’re unique and usually a way for you to quickly identify which page is in your browser tab when you have 300 tabs open and can’t see the text anymore.
- Favicons, like many images, can hold any number of additional code. We’ve actually seen them used in phishing kits and previous research at DomainTools has a repository somewhere of favicons. Basically, in this attack, the favicon is used as the delivery mechanism for the malicious JavaScript that does the skimming.
- Basically what happened here is the skimmers combined a homoglyph attack—basically a domain name that looks enar identical to another domain name at first glance, but say the g is swapped with a q for instance or a Cyrillic character—with this favicon-based obfuscated JavaScript to load their skimmer.
- Homoglyph attacks are rather common and we catch them a lot with our PhishEye tool which is designed to hunt for them and any other number of variations of similar unicode characters. There is a list put out by the folks that manage, I guess is the term, unicode that contains all of the similar looking glyphs that are possible. There are thousands of them and for that reason many registrars don’t allow special characters to be registered, but some, even though they aren’t supposed to, accidentally allow these registrations to go through. We’re talking about a Hebrew character that looks nearly identical to an m and allows for a mail lookalike domain. This is super common and so many variations for attackers to rotate through.
- The MalwareBytes research team detected the skimming kit by using a YARA rule on VirusTotal which is a great way to hunt for these kits. Code reuse is big amongst these skimmer groups and they were able to spot it by just looking for JavaScript that monitors form fields. A little bit of extra obfuscation might have hidden that technique from the YARA rule, but hey, not this time around.
- The cigarpage[.]com connections are captured well in the Maltego graph they put out. Links to a few other domains with a similar skimming history. The good news is that people are hunting for these homoglyph domains for major sites, the bad news is that attackers are going after these small time sites that often don’t have the resources to monitor and secure themselves.
- In terms of the number of sites impacted by this specific skimming attack it looks like only four or so have been hit, but these things move fast, are ephemeral, and keep finding new sites to exploit. They’re on to new things that will also probably be spotted way too late.
How OilRig is Rolling in the DoH
- OilRig is a suspected Iranian threat group that has targeted Middle Eastern and international victims since at least 2014. The group has targeted a variety of industries, including financial, government, energy, chemical, and telecommunications, and has largely focused its operations within the Middle East. It appears the group carries out supply chain attacks, leveraging the trust relationship between organizations to attack their primary targets. FireEye assesses that the group works on behalf of the Iranian government based on infrastructure details that contain references to Iran, use of Iranian infrastructure, and targeting that aligns with nation-state interests.
- Sources:
- MITRE ATT&Ck: OilRig
- OilRig Actors Provide a Glimpse into Development and Testing Efforts
- Iranian Threat Agent OilRig Delivers Digitally Signed Malware, Impersonates University of Oxford
- The OilRig Campaign: Attacks on Saudi Arabian Organizations Deliver Helminth Backdoor
- OilRig Malware Campaign Updates Toolset and Expands Targets
- Unit 42 Playbook Viewer
- OilRig Targets Technology Service Provider and Government Agency with QUADAGENT
- This group was previously tracked under two distinct groups, APT34 and OilRig, but was combined due to additional reporting giving higher confidence about the overlap of the activity.
- Palo Alto, Kaspersky, and FireEye all have great write ups on APT34/OilRig.
- Open source project that makes it easy to use DoH for exfil.
- In terms of a high level explanation of DoH: With DoH, DNS queries are hidden within the larger flow of HTTPS traffic. This gives network admins less visibility but providers users with more privacy.
- If adversaries have access to this toolset our ability to block domains and IP addresses goes away. This allows adversafies to obfuscate and make it more difficult for defenders to see what happens and bypasses a defender’s traditional toolset.
- This is unlikely OilRig’s first use of DoH. There is different malware going back to DoHC2 released at ATT&CKcon, and then PsiXBot Godlua Backdoor 2019.
- In terms of how dangerous this new technique is, they are kind of expanding on odl TTPs. When I think of OilRig I always think of DNS tunneling anyway.
- It’s hard to defend against this type of attack. I’d recommend starting by determining if your org is using DoH. Use tools like Zeek, JA3, and others to find out if you have hosts connecting to DoH TRRs.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
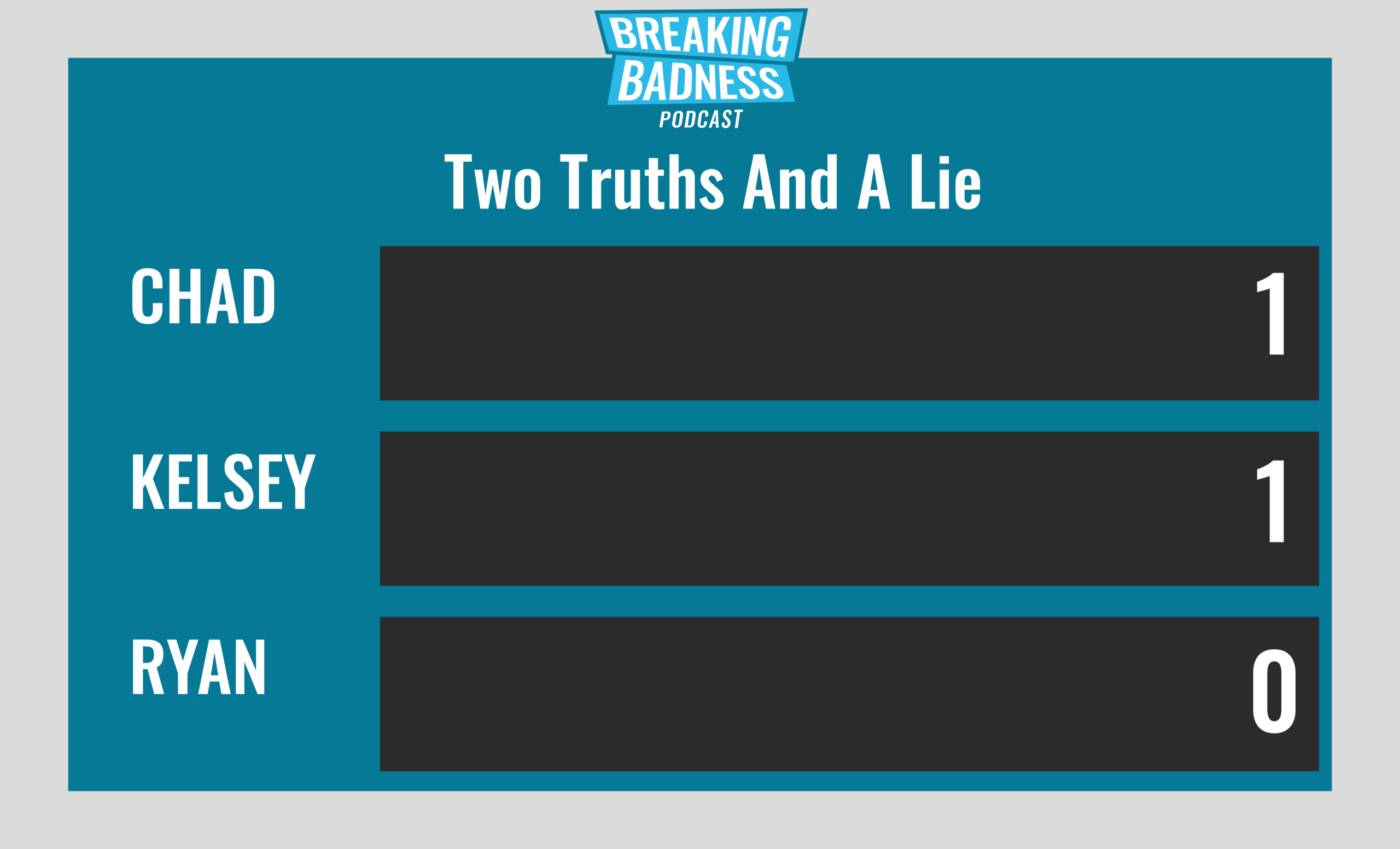
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Pros and Favicons Of Homoglyphs
[Chad]: 4/10 Hoodies
[Ryan]: 4/10 Hoodies
How OilRig is Rolling in the DoH
[Ryan]: 8.5/10 Hoodies
[Tarik]: 8/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




