Coming up this week on Breaking Badness. Today we discuss: GoldenSpy vs. Spy, Newly Discovered Malware Cracks The Xcode, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
GoldenSpy vs. Spy
- GoldenSpy was discovered by the Trustwave folks as mentioned and that it had two processes it installed as services, one that was capable of pulling updates and installing new binaries. All of this was bundled in legitimate tax software that businesses were required to install to conduct business in China. This is kind of how some of the Chinese government operations work though, right? As we know the government usually installs a team of people at a company and they have access to internals—that’s part of the requirements of operating in China. In this case though, after the blog post by Trustwave received some acclaim there were multiple, subsequent binaries that came through the original GoldenSpy malware—some of which were trying to erase its existence entirely on the system.
- There were multiple variants of the uninstallers. The first one Trustwave released a YARA rule to spot it so then the folks behind GoldenSpy released another that purposefully evaded the YARA rule by modifying some of the strings used in the detection.
- Trustwave has been great about identifying who is behind GoldenSpy since their initial report and said that this could very well just be a poorly designed updater and not actually APT-level activity from the Chinese government, but it still has the potential to be based upon everything else the updater is doing. There are plenty of TTPs that make it fit with nation-state activity. The uninstallers do tie to another Chinese company as well, but really, yeah, who can say. Attribution is hard here.
- The reason I chose this story for this week is because of how curious this case is. The first blog post was back in June from Trustwave, right? But they’re still finding new uninstaller variants being pushed and have recently published on that as well.
- My gut tells me we don’t have to be too concerned. If the uninstallers were installing some new, hidden variant that maintained persistence I’d be more worried, but I think the fact that they’re cleaning up as much as possible after themselves and trying to hide from YARA rules means that whoever is behind this tax software is paying close attention to the blog posts from Trustwave and is maybe trying to just clean up some overreaching software.
Newly Discovered Malware Cracks The Xcode
- TrendMicro found two Xcode projects infected by the malware from researching online. One happened on July 13 and the other on July 31. Fortunately, these projects are not too relevant for other users to download and integrate these into their own projects.
- This appears to be a new piece of Mac malware.
- Xcode is an integrated development environment for macOS containing a suite of software development tools developed by Apple for developing software on MacOS/iOS. So, XCSSET uses two 0-day exploits to poison the source code in the XCode application suite when used by developers to compile their application code.
- Using exploits, XCSSET abuses the existing Safari and other installed browsers to steal user data. In particular, it:
- Uses a vulnerability to read and dump Safari cookies
- Uses the Safari development version to inject JavaScript backdoors on to websites via a Universal Cross-site Scripting (UXSS) attack
- It steals information from the user’s Evernote, Notes, Skype, Telegram, QQ ,and WeChat apps
- It takes screenshots of the user’s current screen
- It uploads files from the affected machines to the attacker’s specified server
- It encrypts files and shows a ransom note, if commanded by the server
- Inside of the malicious XCode bundle, there is a single shell script called ‘xcassets’ and an additional folder that when executed drops additional malicious JavaScript and Applescript files that masquerade as legitimate XCode processes.
- The attacker has a lot of choices in what they do against affected developers via the arbitrary JavaScript injected into the browser.
- Modifying displayed websites
- Modifying /replacing Bitcoin/cryptocurrency addresses
- Stealing amoCRM, Apple ID, Google, Paypal, SIPMarket, and Yandex credentials
- Stealing credit card information from the Apple Store
- Blocking the user from changing passwords but also stealing newly modified passwords
- Capturing screenshots of certain accessed sites
- One 0 day is a vulnerability in the Data Vaults service, allowing attackers to steal session cookies. Data Vaults is a service that is a mechanism—enforced by the kernel—to protect against unauthorized access to data regardless of whether the requesting app is itself sandboxed.
- Another is a privilege escalation vulnerability in the Development version of Safari which combined with a UXSS allows high priv JavaScript to run.
- From their investigation of the C&C server, they were able to obtain the list of victim IP addresses that were collected by the malware authors. Out of the 380 entries, users from China are the highest with 152, followed by users from India with 103. So the victimology is pretty clear here.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
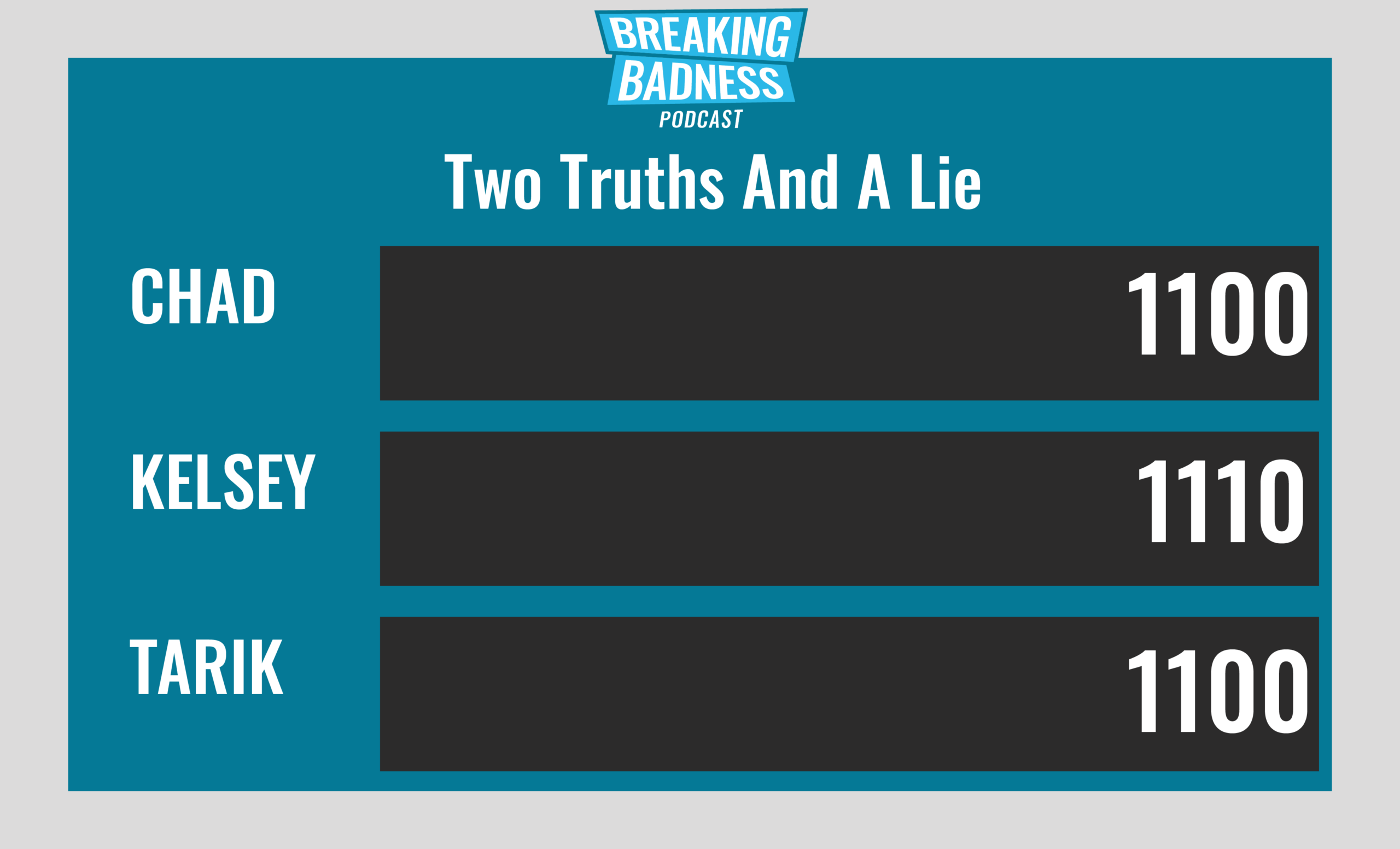
Current Scoreboard
This Week’s Hoodie/Goodie Scale
GoldenSpy vs. Spy[Chad]: 3/10 Hoodies[Tarik]: 5/10 Hoodies
Newly Discovered Malware Cracks The Xcode[Chad]: 9/10 Hoodies[Tarik]: 9/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

