Coming up this week on Breaking Badness. Today we discuss: How to Keep Prime Ministers Grounded, Missed Patch Leaves More Than a System Vulnerable, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
How to Keep Prime Ministers Grounded
- First, this is how all write ups should always be done. The level of sarcasm here was deep, on the level of deep that I think only an Aussie could really manage to pull it off. So yeah, basically, I assume Alex Hope here saw a similar DEFCON talk years back to me where the author showed basically how you could datamine Instagram for boarding pass photographs and just collect peoples passport numbers from these insecure airline sites. That researcher actually reached out to airlines and they basically were like no we won’t fix that. So here we are, 2020, and Alex Hope told their friends about this possibility and sure enough an ex-prime minister of Australia had posted their passport on Instagram and badabing badaboom this leads you right to a passport number with minimal effort.
- I assume he had problems reading the barcode because everything is upside down down there, but all he had to do was put the booking reference number into the airline site. That will for most airlines log you in as the passenger with the airline and let you manage the booking. SECURITY!
- Inspector Element is Inspector Gadget’s evil hacker twin brother. If you right click on any page element you can summon him to perform evil. In this case Alex just needed to look at what data was passed along as part of the HTTP request. When the booking reference number hits the database, it will return a bunch of elements to the page that may be needed for managing the booking including passport number.
- Alex went through basic responsible disclosure. Spoke to the government, said hey any dummy can do this, government was like we don’t believe you then eventually proved it, then told Qantas, Qantas took five months to remove a single field from a web page hashtag fixed hashtag production hashtag programmer life, then—and of course this is heavily abridged since it took more effort than this—Tony Abbott called him and they had a chat about computer security and he got the okay to publish his blog post. Pretty cool ending actually if you ask me.
- Really this will continue to be an issue. Airlines aren’t going to change. Your boarding reference is your password for your travel. Your ID is the logon, right? At least at the airport, but online they skip that formality. So things could require in person changes so passport numbers aren’t leaked online, but passengers also want convenience. Not much will change I would suspect outside maybe for Qantas.
Missed Patch Leaves More Than a System Vulnerable
- German authorities made a statement last Thursday that a supposed “misdirected” ransomware attack caused a shutdown of major infrastructure at a hospital in Dusseldorf Germany, which led specifically to a death of a woman who needed urgent care and had to be taken to another city for treatment.
- This marks the first time we have actual data showing a ransomware attack has led to loss of life. We’ve speculated about it before as there have been several ransomware attacks that have targeted the medical sector.
- We know that approximately 30 servers at the hospital were compromised and had critical services rendered useless last week. The attackers left a ransomware note, but curiously enough it was addressed to an affiliated German university and not specifically to the hospital.
- This may be because the attacker compromised a section of the Henrich Heine university network that potentially was shared with the Dusseldorf hospital. Oftentimes attackers will see network ranges but don’t have context behind them. It’s all really just CIDR notation and not “hospital” or “university”.
- I think the most interesting thing here is that the hospital negotiated and communicated with the attackers. The channel and means that they did is unknown, but it was likely over Tor or a privacy-focused email system like Protonmail.
- What’s fascinating is that the attacker supposedly provided the key to decrypt the data and restore the services once they found out they brought down a hospital network.
- The downtime of systems resulted in the German hospital not being able to intake new patients and required her to be transported to another hospital 20 miles away. This led to a delay in treatment for over an hour, in which she passed away.
- In my personal opinion, it absolutely should qualify for charades including the death. It’s so easy to be abstracted from the human impact when you’re just looking at code and IP addresses, but this attack clearly shows otherwise.
- Here’s some really interesting data points collected about hospital networks and ransomware attacks:
- 172 ransomware attacks from 2016-2019, affecting over 1,446 hospitals/clinics and orgs.
- 6.65 million patient records impacted
- Ransomware amounts varied from 1,600$ to 14m$
- Downtime costs in California cost 23$-35$m
- Legal costs are still to be determined but they could be significant
- This unfortunately doesn’t surprise me, since ransomware has been rampant in the hospital sector for quite some time. I’m not surprised, just really disappointed in cybercriminals. So much for Robin Hood. I suppose a pseudo-silver lining is that the attackers gave the decryption key to the hospital for free.
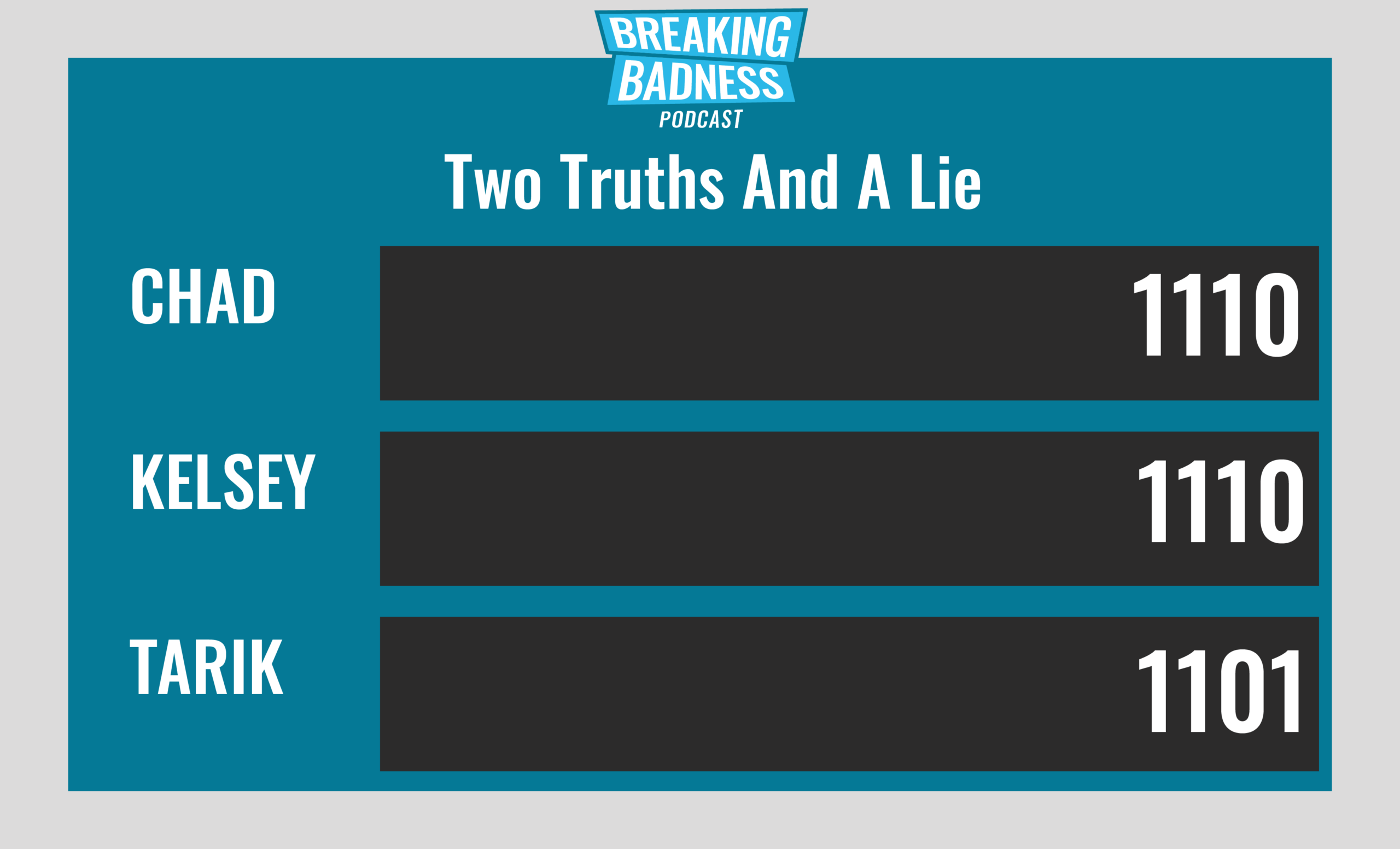
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
How to Keep Prime Ministers Grounded
[Chad]: 10/10 Hoodies
[Tarik]: 10/10 Hoodies
Missed Patch Leaves More Than a System Vulnerable
[Chad]: 10/10 Hoodies
[Tarik]: 10/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




