Coming up this week on Breaking Badness. Today we discuss: MontysThree and the Foley Tale, More Reasons for Healthy Phishing Paranoia, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
MontysThree and the Foley Tale
- In regards to MontysThree, there’s actually not a ton of history that we know about for this group. They are fairly recently discovered. Of course that doesn’t mean they are actually a new group—they may have been hiding and operating for a while.
- For their most recent campaign, while they seem to be operating against industrial targets, there’s no evidence that they have compromised any industrial processes—at least none that Kaspersky has revealed. What I’ve seen published about this campaign thus far—which is not a whole lot—indicates that the goal is espionage. At least, that seems to be the current objective. If they’re successful against one or more targets with that, we may learn more about what their long-term objectives are.
- The loader is part of a toolset called MT3, which has a few separate modules, and as you’d assume, the loader is the first piece. So the loader itself is disguised as a bitmap file. But this bitmap is actually a piece of steganography. Probably most of the audience is familiar with stego, but if you’re not, very briefly, it’s sort of a method of hiding in plain sight. Code that is one thing looks like it’s another thing. Images are a really popular method for doing steganography—the image looks like whatever it is depicting, but it also contains embedded code that is something else entirely. In this case, it’s a self-extracting RAR file. Once that executes, the malware is on the target machine and ready for business.
- Once the malware is installed, It goes shopping around for certain types of files. In this case, it seems to be targeting Microsoft and Adobe documents. It also has some “favorite” directories that it looks for. It also takes screenshots and does some fingerprinting of the compromised machines to figure out if they’re attention-worthy. And, presumably, its aim is to do the usual kill chain stuff, and end up exfiltrating whatever files look like they meet the adversary’s criteria.
- Like the steganography, this is another example of hiding in plain sight. They have hosted the C2 infrastructure on legitimate services like Google, Dropbox, etc—services that organizations can’t realistically block, and where inspection of traffic to them would be expensive—you’d basically have to have HTTPS inspection—a benevolent man in the middle proxy—watching for anomalous traffic. Certainly some organizations have that, but it’s finicky technology, and there probably aren’t super obvious signatures to look for. Having said that, some DLP technologies might be effective at flagging or blocking the exfiltration.
- As of now, we aren’t sure who is behind this malware. I don’t know if it’s ever been brought up on this podcast before, but attribution is hard. Kaspersky isn’t saying anything about who might be behind this activity. We’ll have to see what more is learned about them—either by researchers or by victimology, if victims are identified.
- I agree with the researchers at Kaspersky who found it interesting that the MT3 toolset seems to have a mix of sophisticated and amateurish components. This makes it less clear as to whether we’re looking at something like a state-sponsored group or not. Though certainly putting some crapware into the mix might be a good way for a sophisticated actor to try to throw defenders off the scent.
- Also I think anything targeting industrial infrastructure is interesting—of course you don’t like to see it happening, but it’s reality these days. Certainly I hope they aren’t successful.
- It’s hard to know, really, how concerned to be yet. We know these guys have some tools that could be effective. It sounds like they are reasonably savvy phishers. But ultimately we don’t know enough about the reach of it to make much of an educated guess about the risk level.
More Reasons for Healthy Phishing Paranoia
- We’ve seen COVID lures die down a bit over the past month, but since the President’s diagnosis, there was an upstick as this was tied into this specific campaign.
- Researchers at Proofpoint discovered the phishing email campaign used a COVID lure specifically highlighting the President’s positive test.
- According to Proofpoint, “Once the victim attempts to download the document, a fake Google Doc message is displayed which states that Google scanned the document and it is not malicious. When clicking the link, the BazarLoader executable is downloaded instead of a Microsoft Word document. Once installed, BazarLoader allows the threat actors to have remote access to the computer of the victim and use it to compromise the rest of the network”.
- In the end, Ryuk ransomware ended up getting dropped on the box.
- BazarLoader is a really covert piece of malware that is very minimalistically designed. While on the victim’s machine it operates really simply and blends in really well. We’ve seen BazarLoader almost always exclusively originate with targeted phishing attacks as a malicious URL or attachment by the TrickBot Gang.
- In this specific attack campaign by TrickBot, we saw the infamous Ryuk ransomware get dropped on the victim’s machine. </li
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
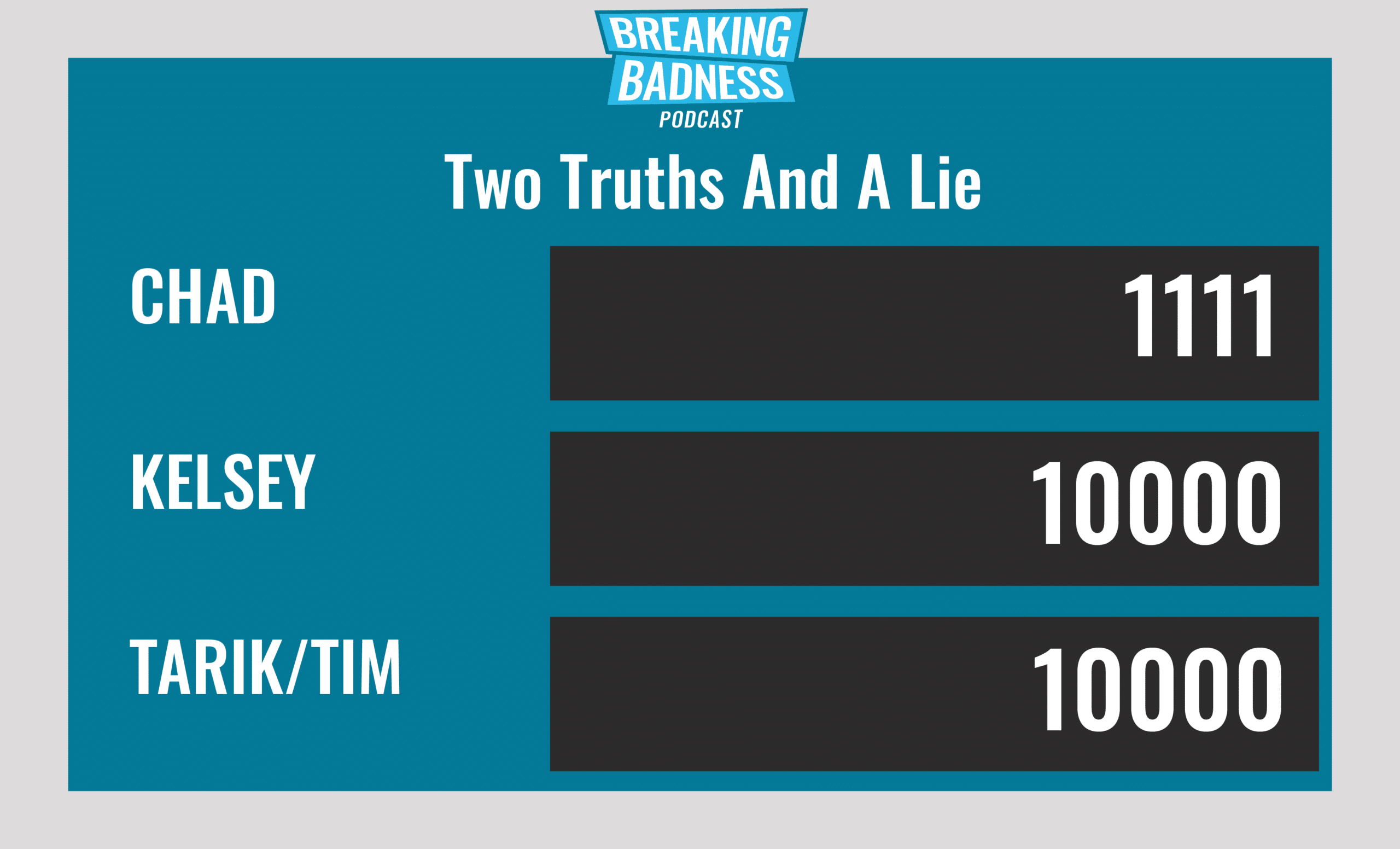
Current Scoreboard
This Week’s Hoodie/Goodie Scale
MontysThree and the Foley Tale
[Tim]: 5/10 Hoodies
[Tarik]: 7/10 Hoodies
More Reasons for Healthy Phishing Paranoia
[Tim]: 8/10 Hoodies
[Tarik]: 8/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




