Coming up this week on Breaking Badness. Today we discuss: A New A-Peal to Apple's Bug Bounty Program, The Times They Are A Vulnerability Chaining, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
A New A-Peal to Apple's Bug Bounty Program
- Sam was under the impression that the Apple bug bounty program was for physical products, when he saw a $100k bounty payout for a 0day sign in bug he got interested in tackling more.
- They first scanned the 17.0.0.0/8 IP block owned by Apple and cataloged / screenshotted every available web server along with HTTP status code, headers, and response body. They then started tackling the known vulnerabilities and poking around to discover more.
- This recon was essential in determining their targets. It helped them define their scope and narrow down what they wanted to go after.
- Of the 55 vulnerabilities found by Sam and his team, 11 that were deemed critical, of those the Wormable XSS exploit that allowed them to pull photos and documents out of iCloud accounts via email as well as forward along the exploit to other iCloud users from the address book of the victim is really interesting. They also managed to pull AWS IAM keys and bypass authorization in some really clever ways.
- Apple was very responsive, most of these bugs were patched within 1-2 days, and in some cases within a matter of hours. Their total haul from the bounty program was $288k as of October 8th.
- In terms of how red teams and threat hunters can apply a similar approach, the scaling of their reconnaissance to capture tens of thousands of targets within the Apple infrastructure is certainly one worth emulating.
- The more responsive and thorough companies are in dealing with their bounty programs the greater chance they have of researchers going through them first, and not into the dark web. As to whether or not it is a “big deal”, I’d say yes based on the volume and impact of the bugs found.
The Times They Are A Vulnerability Chaining
- Vulnerability chaining is a standard now in vulnerability research/exploit development. Chained vulnerabilities are vulnerabilities that have been linked together to become more than the sum of their parts. For example, if you have a web application that transmits credentials in cleartext and then a threat actor snags those and logs into an account and finds an Unrestricted File Upload vulnerability in an account profile’s avatar picture that allows you to upload a webshell and gain command execution.
- From personal experience, I dealt with an investigation that involved a chained 0-day in Adobe Flash and IE 10 that was attributed to APT1 in a watering hole attack against Forbes.com. That allowed all Windows machines running the latest version of Flash and Internet Explorer 10 to be compromised.
- The CISA and FBI in their joint statement state that they’ve seen the recent privilege escalation vulnerability in Windows Netlogon being leveraged against several government agencies and networks. There isn’t direct targeting of election systems, however, it appears that some election systems that are housed in some of the compromised networks may be affected.
- Is that it appears that the election systems integrity hasn’t been compromised. The bottom line, really, is defenders of government networks need to stay on top of their security hygiene and patching.
- From a mitigation perspective, I really like the CISA/FBI’s advisory language of “if you’re affected you should assume breach”.
- It’s easy on paper to talk about security hygiene, but in reality, vulnerability management is very much dependent on the company culture and politics. It’s difficult to get others to prioritize security, especially in a situation where a vulnerability is high risk. You’re randomizing teams with their sprint planning sessions. Security can be a disruptive force.
- So, really, everyone needs to change when it comes to taking security seriously. We need to change the collective culture behind being randomized and interrupted to protect organizations. We need to have company cultures be ok with it. We won’t be successful if we don’t.
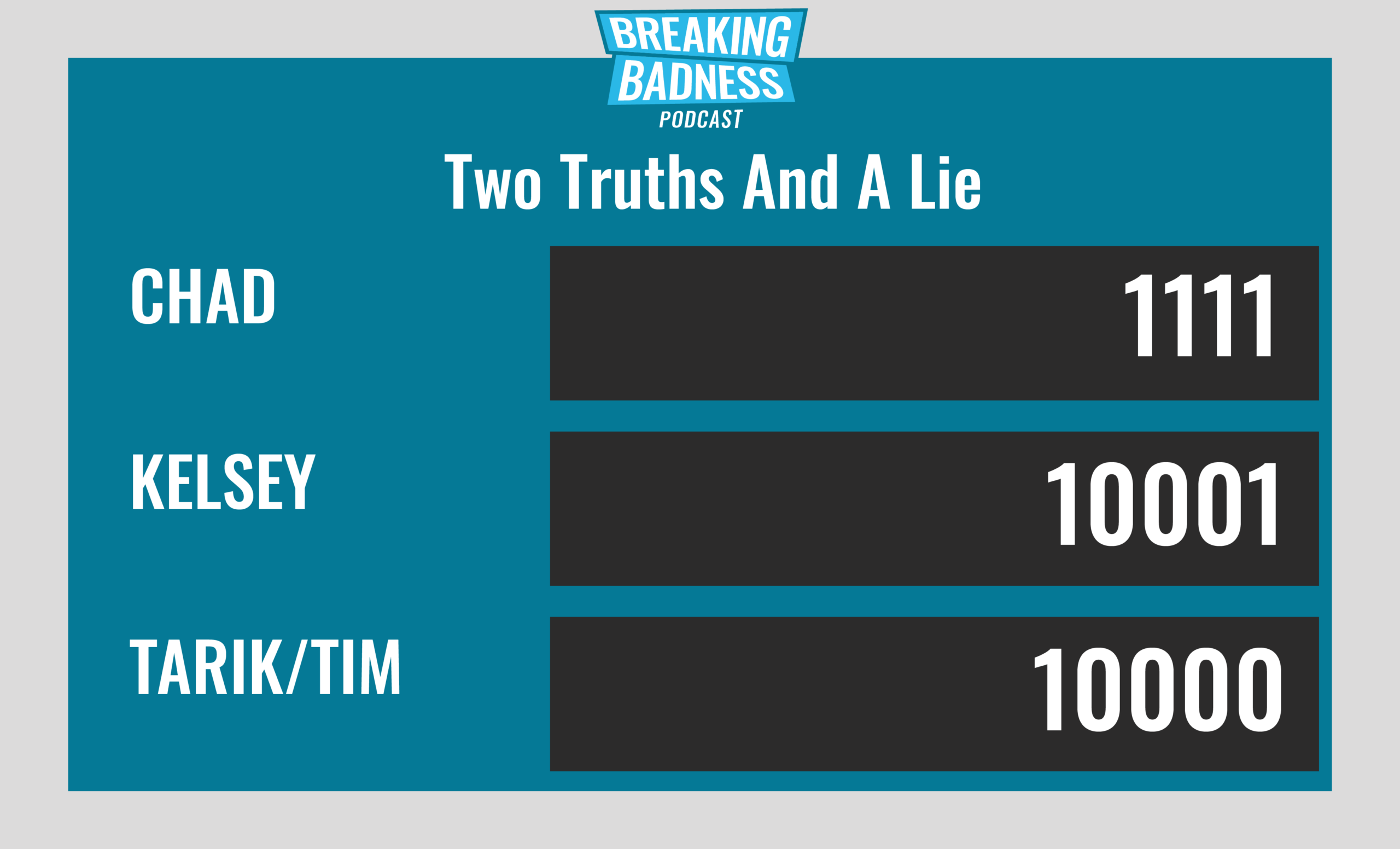
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
A New A-Peal to Apple's Bug Bounty Program[Taylor]: 10/10 Goodies[Tarik]: 10/10 Goodies
The Times They Are A Vulnerability Chaining [Taylor]: 4.26/10 Hoodies[Tarik]: 6/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

