Coming up this week on Breaking Badness. Today we discuss: CISA And Ye Shall Find Ransomware Attack Warnings, Parke Diem: Seize the Parked Domain, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
CISA And Ye Shall Find Ransomware Attack Warnings
- I would assume that this has to be the massive increase in UNC1878 activity. UNC—standing for uncategorized—is how Mandiant rates threats and UNC1878 is just one set of intrusions underneath the Ryuk ransomware umbrella. UNC1878 was thought to have died off as they were quiet for several months, but have since come back with a fervor and on top of that they are going from initial infection to ransomware attack faster and faster. Normally it takes days for an attacker to gain that foothold and in most cases UNC1878 is encrypting victim machines in under 5 hours. They’re moving fast and attacking a lot at once. These agencies have reason to believe this is a mass targeted attack on hospital infrastructure.
- Last week Ryuk was in the news for an overall wave of observed, attempted and successful intrusions into the US healthcare sector.
- Typically, Ryuk attacks use either TrickBot or BazaarLoader, but with other tools now such as KEGTAP. For some reason UNC1878 has been changing their tooling and tactics a bit, likely because people have gotten used to hunting for their current tools. These initial loaders are used to drop the main payload and call back to a command and control server the attacker controls. The initial way people become infected is by opening a malicious document or by being directed to a phishing site.
- Once downloaded and the initial loader is executed, then things move on to the lateral movement stage where other machines on the same network are infected, then eventually the Ryuk ransomware encrypts the victim's files and demands a ransom. Interestingly, Ryuk has not been seen running the double extortion scams that we have seen groups like Avaddon doing where they demand a ransom or they will release the files online and the company will face GDPR fines instead.
- Ryuk is a talented group with some good tooling. They also shift their tactics and tooling to target high profile companies that they can make more money off of if successful. We’ve seen tens of millions stolen by them so far this year and they continue to be successful, motivated, and quick in their work.
- So we have actually had one death related to ransomware in Germany this year. These attacks bleed into the real world now and have real life consequences. This isn’t just some Excel spreadsheets encrypted anymore, but actual life saving machines. Arguably, those machines should never be on the network, but we’ve seen before how a single, vulnerable coffee pot has been responsible for reinfecting a company with ransomware and all by accidentally being on the wrong network. These things happen and it’s terrible these gangs are targeting hospitals at a time like this.
- The usual best practices of patch and multi factor authentication. You are going to get popped at some point. That’s just the truth. And it’s all about making it expensive and difficult for the attacker to propagate around the network. Slowing their progress buys you more time to catch the initial intrusion and triage. Simple as that. Well, actually really difficult to do well, but in theory the concepts are simple.
Parke Diem: Seize the Parked Domain
- Whether or not you know the term, pretty much everyone has seen parked domains from time to time. Some hosters have a cheesy picture of parked cars to help emphasize the point. Basically, parked is a sort of limbo state that a domain is in where it is registered, but not hosted on a server that serves up functional content. When you first register a domain, it’s usually parked for at least a short time—that time can be as little as minutes, or as long as the entire registration length of the domain. When you are the registrant (or have stolen the credentials of the registrant), you then have control over the DNS records for the domain, which allows you to point it to whatever IP you want, and away from the parking IP.
- But there’s also a very intentional use of parked domains, and that has more to do with this story. People will sometimes park domains that are intentional typos of legitimate domains, in order to drive visitors who accidentally made the typo to whatever content the domain owner wants them to go to. This isn’t always nefarious; it can be a way to make a few bucks off of affiliate advertisement and such.
- So again let’s consider that scenario where someone mistypes a URL and lands on a parked domain. If a more innocent type of parked domain can point the user toward an ad or a site that is paying per click for visitors, it can also point the user toward a malicious site that will stage malware, harvest credentials, et cetera.
- Basically, as background, what this story illustrates is that there’s kind of a spectrum of maliciousness that we see with parked domains. At one end of the spectrum is zero maliciousness—many (probably the majority of) parked domains don’t have any malicious intent tied to them. Then there are domains that we might call shady—they’re not necessarily outright bad and they don’t necessarily harm the end user, but they use mimicry to deceive users and they can then generate some profits through affiliate advertising, but they don’t cause actual harm to the end-user. But then there are parked domains like what Emotet is using here that are just flat-out malicious. An example from some research by Palo Alto is the domain valleymedicalandsurgicalclinic].]com, which auto-redirects the visitor to a server that loads Emotet onto the victim’s machine. Most listeners probably are familiar with Emotet, but as a reminder, it’s a Trojan that establishes a foothold on the victim machine and then can allow other more specialized malware to be loaded. Redirects, by the way, are often part of the chain of events that occur in malicious use of Internet infrastructure. Everyone’s seen it now and then, even if you didn’t realize what was technically going on. Your browser rips through a sequence of pages, sometimes spawning new tabs. There can sometimes be very long chains of redirects. It’s one of the reasons we collect redirect info, because when you’re researching nefarious infrastructure, seeing where a domain redirects to, or where it was redirected from, can be instructive.
- This is an example of that mid-spectrum parked domain situation. How it works is that the shady actor registered a domain that is a deliberate typo of xfinity (in this case xifinity,com), and I’ll tell you that when you see that in writing, the eye can definitely miss that “i” right after the “x.” That domain—guess what—redirects to a really classic example of a shady domain name construction: antivirus-protection.com-123,xyz. So, technically, the “.com” part of that domain name is a subdomain, which you can just set up in your DNS records. The actual registered domain is com-123,xyz. I took a peek into pDNS (passive DNS) records for that domain, and boy howdy, you can see all kinds of nefariousness with it. It mimics McAfee, Barracuda, and Windows, plus it has a few other sketchy subdomains like update-antivirus.com-123 etc. So you might be wondering why I call this one “mid-level” sketch since it seems rotten as anything. The reason is that you don’t actually get any malware when you hit these domains. Instead, you get tricked into thinking you’re infected, and then you get (guess what?) redirected again to a McAfee antivirus page. The thing is, that one is a legit McAfee site. So we can assume that the nefarious actor gets a couple pennies per click from McAfee affiliate advertising, and I guess McAfee probably gets a few customers this way. We’ll assume that they take the high road and discourage others from sending them potential customers in this shady way. At any rate, at least the victim doesn’t outright install malware when they hit these sites.
- Typosquatting can be a little tricky because sometimes users land on these URLs by literally mistyping them, rather than clicking on phishing email links and such. So, while I’ll say that of course you should have good phishing awareness programs, you can’t train folks out of making typos. (Well, I guess you could make everyone go to remedial typing classes, but I’m thinking most cybersecurity budgets don’t have a line item for that). In addition to having good network and host IPS and firewalls, there is in fact an education piece here, which is to make sure folks know that when they see rapid-fire redirects going on, they should be very cautious. When I see it, I quickly close the window or tab that has the redirects, and watch for odd activities on my machine or phone right afterward. Another education piece is that legit antivirus companies don’t run scans on your system when they’re not installed--so if you get a popup or a web page that says “you’re infected, go download this AV to clean it,” you should RUN AWAY!
- The recent examples with Xfinity and McAfee are obnoxious for sure, but as I said before they’re in the middle of the spectrum of badness. That Emotet domain (and really the one it redirected to) is 100% malicious, so it’s worse than this specific xfinity example. I think the takeaway here is that there are some things to look out for while you’re in the course of everyday web surfing.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
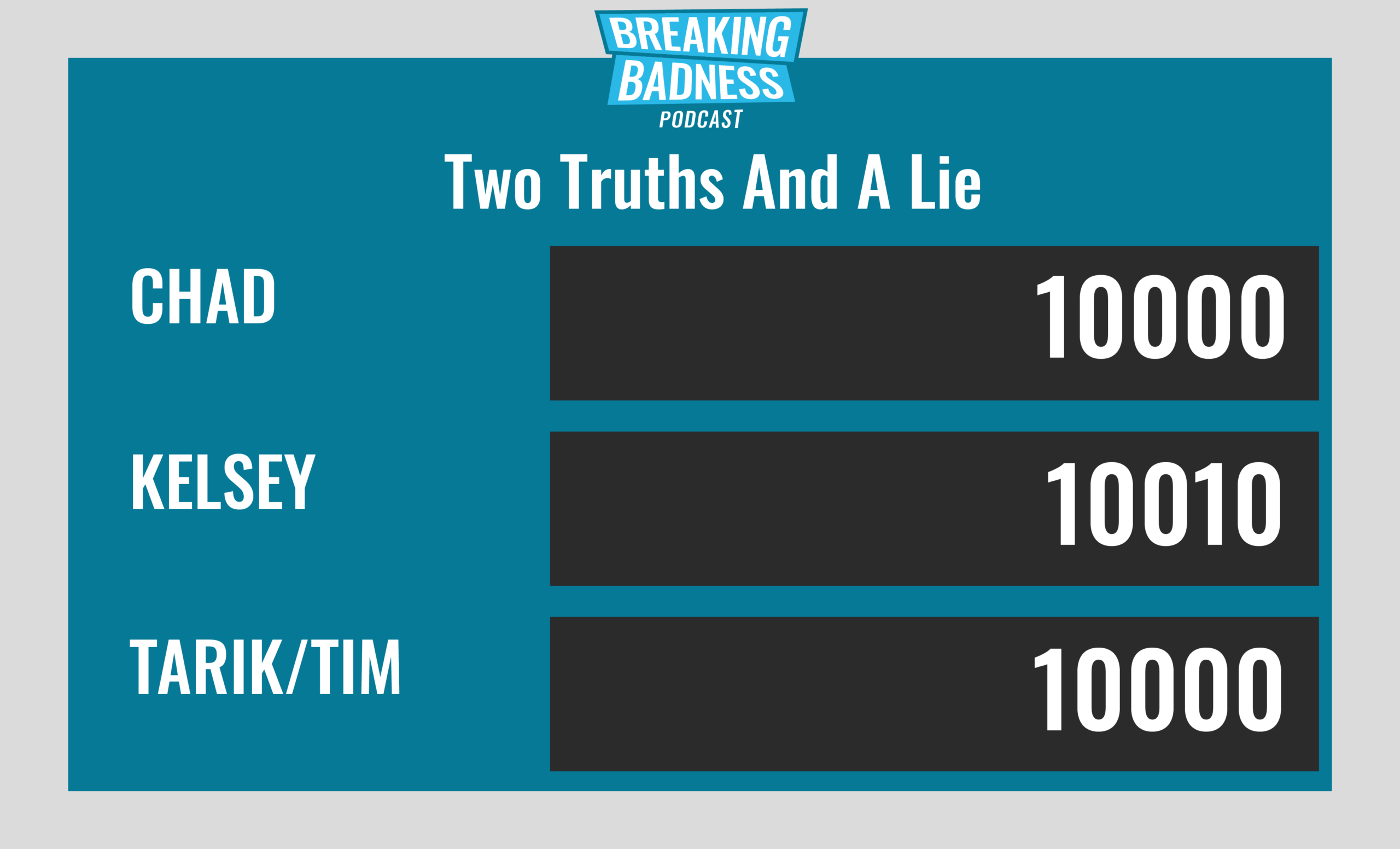
Current Scoreboard
This Week’s Hoodie/Goodie Scale
CISA And Ye Shall Find Ransomware Attack Warnings[Chad]: 9/10 Hoodies[Tim]: 9/10 Hoodies
Parke Diem: Seize the Parked Domain[Chad]: 6/10 Hoodies[Tim]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

