Coming up this week on Breaking Badness. Today we discuss: The Maze-a-morphosis, The Cobalt Strikes Back, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
The Maze-a-morphosis
- So Maze has been around for a short minute, but has already pulled in some huge earnings. They were one of the groups to start doing double extortion where they threaten to leak your data on a leaks site—6 months in the case of Maze—if you don’t pay them to decrypt and release the files. They tended to go after companies around the 200 employee range and with all of those tactics ended up being rather successful in the ransomware space—certainly up there with Ryuk even though now Ryuk has largely eclipsed that. Maze has since announced their retirement from the game which isn’t always them actually retiring, but perhaps generating a new persona and moving to some new tooling. We’ve certainly seen that happen before—new and improved tactics for an actor might require a rebranding if you will.
- Maze infections have steadily decreased and are being sunsetted. I think they will stop being available at the end of November or something like that if I remember right. They were an affiliate program so had underlings doing the actual infections and were taking a cut of the profits. Another common ransomware gang tactic to be basically a multi level marketing company. In their absence though, another contender always comes into play.
- So Maze affiliates are now moving under the Egregor banner which is a modified version of Sekhmet. They’ve been active since about September though Maze has said that Egregor is not an official successor. This new family is already in the top 10 for this quarter of ransomware infections so definitely on the rise.
- Egregor’s payload is really interesting. First off they only give 72 hours to pay a ransom before dropping leaks online. This accelerated time frame is sure to get some people to panic pay out if the double extortion wasn’t already effective. In addition to that their payload can only be decrypted if the key is provided at the time of execution so this makes it extremely difficult if not impossible to analyze individual samples in a sandbox.
- I think this short time frame for payment is an interesting way to motivate victims. I think this payload is also a bit more sophisticated than we are used to seeing so may become a bit more of a norm if it’s more successful. We have yet to see if the folks behind Egregor infections can be as effective and speedy as the Ryuk group, but overall I think we’ll see an uptick here if only because people like new tools and another set of lockdowns are coming. What better thing to spend your time doing at home than infecting machines and getting paid?
The Cobalt Strikes Back
- Many of you listeners may be familiar with Cobalt Strike, or if not intimately so, then you have probably heard the name. It is a pen-testing tool, but as you’d expect, its white hat intentions were ignored by many actors who saw it as a great way to achieve nefarious objectives against victim networks. Because what Cobalt Strike does is provide multiple ways to exploit the penetrated network once the attacker is inside. Since it lets you run PowerShell scripts, escalate privileges, etc, you have a lot of power to create C2 channels, move laterally, and generally wreak havoc. It’s not the sort of thing you want an adversary using against you.
- Not long ago, a repository was created on github. The repo you’re talking about here does in fact appear to be the source code for CobaltStrike 4.0, which was originally released just under a year ago (in December of 2019).
- The source code does appear to be authentic. Among other things, you can see the license check code…only thing is, it’s been commented out.
- As of a few days ago, the repo had been forked 172 times, so that cat’s pretty much out of the bag. I think this is going to prove to be quite popular. Naturally we’re thinking here about adversaries, but I’m sure there will be plenty of more or less benevolent red teamers who will be pretty stoked to be able to have free use of Cobalt Strike. As I said, this particular cat is out of the bag. There will be no getting this toothpaste back in the tube.
- Like so many things in security, this is less about an absolute (“it wasn’t available before, now it is”) than a matter of degree or magnitude. All sorts of actors used Cobalt Strike before. It’s just that now it’s available to more of them, and the cost to use it—assuming you have the know-how to obtain and modify it—has gone down. It will spread. And with the source code available, malicious actors will also modify it in lots of creative ways, so the various effects of it will be harder to predict and possibly to detect and mitigate.
- Having said that, I don’t see it as a game-changer. The adversary still has to do more or less the same things they already had to do to get a foot in the door of the victim network, and at each stage of an attack, they will leave some traces of what they’re doing, giving blue teamers various routes toward detecting and thwarting an attack. Obviously time will tell, and I hope I’m not wrong about whether it will be a game changer.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
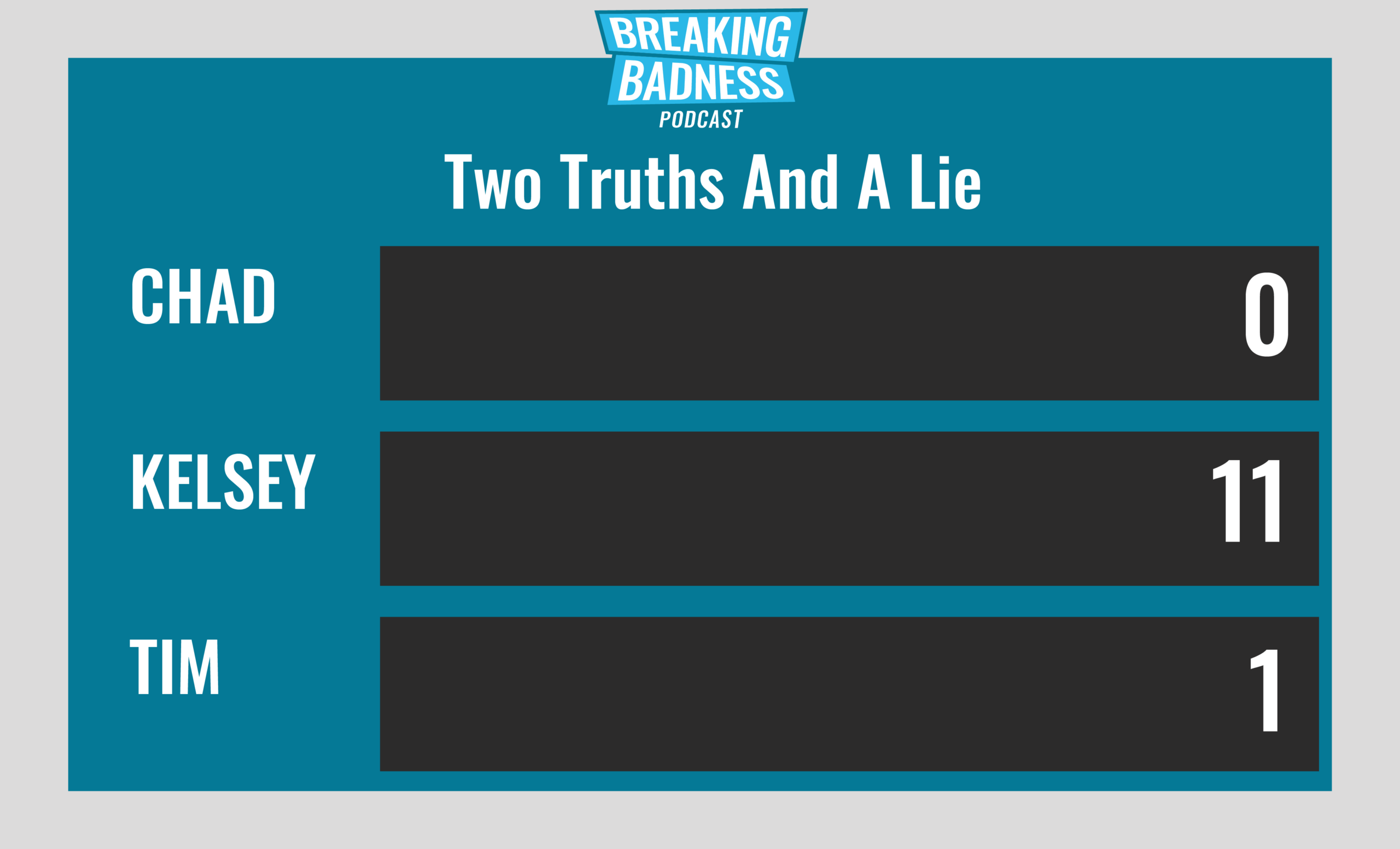
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Maze-a-morphosis
[Chad]: 7.5/10 Hoodies
[Tim]: 7/10 Hoodies
The Cobalt Strikes Back
[Chad]: 6/10 Hoodies
[Tim]: 6/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




