Coming up this week on Breaking Badness. Today we discuss: The Doc of the Town, A Tangled Krebs, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
The Doc of the Town
- One helpful approach is to simply follow the money. This starts by developing a hunting hypothesis: “Where do I think ‘cyber operations’ are likely to occur?”.
- Based on that hypothesis, develop criteria to search for activity related to this event or theme.
- Analyze to determine whether items are incidental or coincidental, or directly targeted and focused on events in question.
- Based on the above, learn adversary tendencies and trade craft to search for more, related activity.
- The malicious document was discovered by searching through commercial multi-scanner malware repositories (aka, VirusTotal but I don’t think we want to call out a specific service).
- The document is an item referencing the Armenia-Azerbaijan conflict.
- However, it contains a template object and other items which prompt a request to a remote resource which presumably contains additional instructions—however, this resource was not available for analysis.
- Based on the above, we were able to identify tendencies around both the malicious documents (the template object) and network infrastructure (domains and servers used for command and control).
- With these tendencies in mind, we could identify additional, related items which linked the Armenia-Azerbaijan document to an actor operating since at least December 2019 through November 2020.
- The document, when opened, attempts to make a connection to a remote host with a specific URL.
- Once connected, something is downloaded and potentially executed by the victim machine.
- The attack chain and methodology superficially matches similar document-template activity linked by other researchers to an entity called “Cloud Atlas” or “Inception”.
- The options for monetization or similar on this campaign are limited, so the likely purpose is espionage or establishing initial access to politically-relevant targets to further such actions.
- Attribution is hard! One easy analytical leap is to say “Russia!” because of where the activity takes place, but past Cloud Atlas activity has also focused on various Russian entities as well.
- The campaign is focused on conflict areas in the Caucasus and Eastern Europe - so outside of these regions, this is likely not a concern for others.
- However, the trade craft used is interesting and not well identified or consistently caught by current security solutions. Being aware of the techniques used can be very valuable for all defenders to protect against similar attacks.
- Shout out to Florian Roth, Jason Smart at PwC UK, and the Black Lotus team at Lumen as I know they have also tracked various parts of this campaign.
A Tangled Krebs
- Chris Krebs is the now former Director of CISA or Cybersecurity and Infrastructure Agency which sits underneath the Department of Homeland Security umbrella. He’s a career cybersecurity and risk management man previously having been the Director of Cybersecurity Policy at Microsoft, also working as an advisor to DHS before becoming Director of CISA.
- CISA made a website debunking election fraud claims. What might have really got him though was he said on Twitter that "59 election security experts all agree, 'in every case of which we are aware, these claims (of fraud) either have been unsubstantiated or are technically incoherent.'" Technically incoherent referring to the conspiracy theory of a government deep state program using a supercomputer to switch votes from Trump to Biden. He was fired via Twitter that same day by President Trump.
- Krebs was known to fill that role effectively and was respected within the cybersecurity community. The firing via Twitter really irked a number of people who found it disrespectful. On top of that a campaign came out on Twitter afterward trying to undercut his work due to his degree not being in cybersecurity which cybersecurity Twitter immediately lashed back at being that there were barely any cybersecurity programs when he was in school and that most people in this industry have degrees in something else anyways because it’s such a budding and growing field—and because an alternative degree nets you alternative perspectives.
- So I have a perspective on this which stretches back to my previous position at Dragos. Chris Krebs stood up CISA not just to protect elections, but also to protect industrial and critical infrastructure in the US. Previous efforts at DHS have existed, but many fell short and were often derided by asset owners and the security industry. Krebs’ leadership combined with the existing talent within DHS with better support allowed CISA to begin emerging as a competent, cooperative, and valuable partner for broader critical infrastructure defense. Removing Krebs threatens to undermine a lot of progress made in the past few years and unsettle DHS’ critical role in domestic cyber operations yet again.
- This election cycle had surprisingly little evidence of nation state participation, but I almost wonder if they see a bad enough situation that states are just letting us roll with it.
- I think we’re seeing a big test of all of our governmental systems and procedures right now. The elasticity of them is being exercised and we’re hoping they don’t snap. A third of the electorate honestly believes that there was election tampering and we can’t have the trust in our elections undermined without leading to even worse outcomes. As for CISA I hope that when Biden takes office he either rehires or brings in an equally competent policy person for the job.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
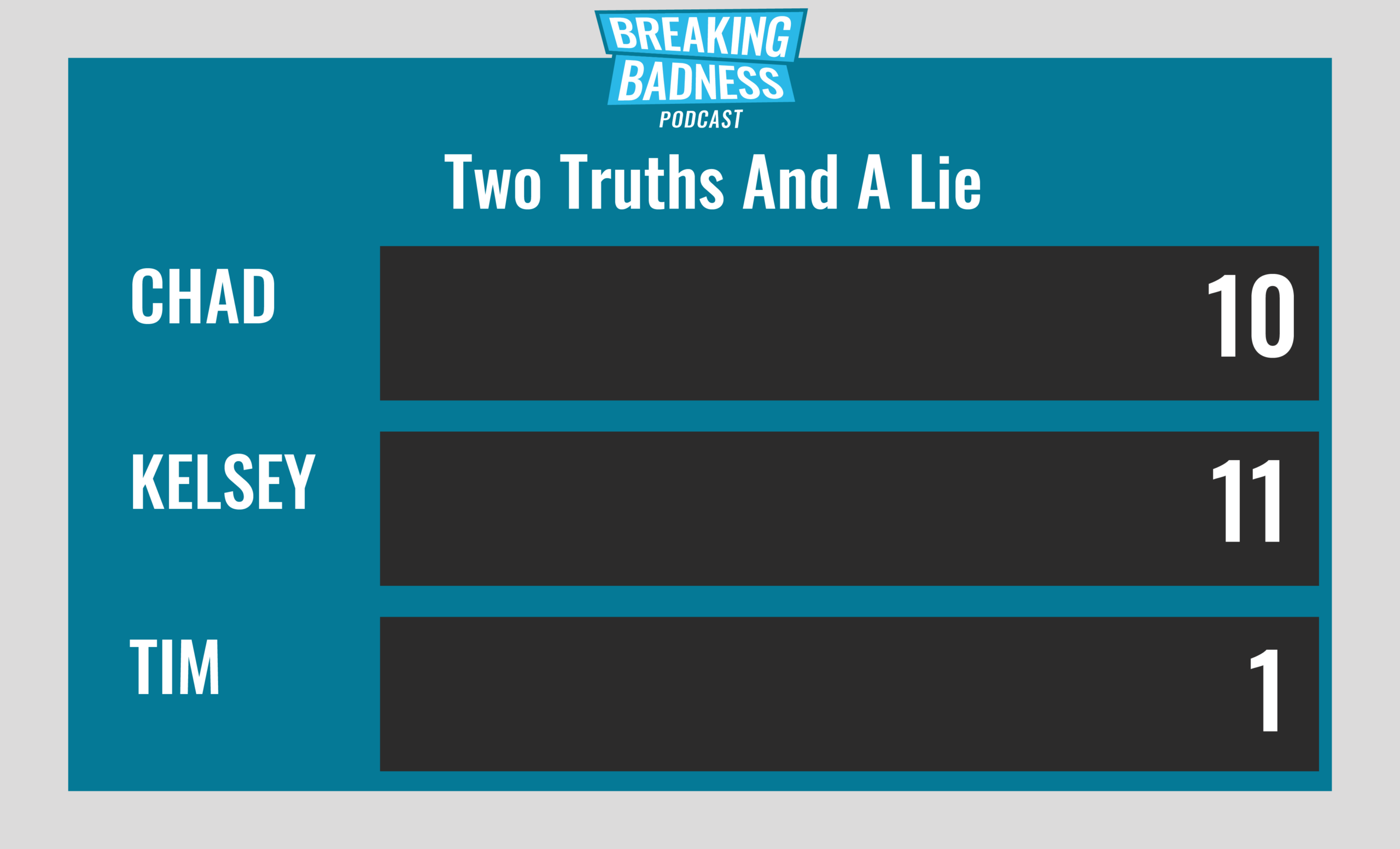
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Doc of the Town[Chad]: 4/10 Hoodies[Joe]: 6/10 Hoodies
A Tangled Krebs[Chad]: 1/10 Hoodies[Joe]: 4/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

