Coming up this week on Breaking Badness. Today we discuss: A Miner Docker Attack, A Pi in the Sky Can Pwn Your i(phone), and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
A Miner Docker Attack
- There’s a new coin mining botnet on the loose. It was reported by Talos, and they have called it Xanthe.
- It looks for misconfigured Docker instances on the open Internet. We’re putting it this easy rather than simply saying “open,” since a user has to go through a number of quite intentional steps in order to expose a Docker instance to the Internet.
- After kicking any competing bots off the victim, it installs tooling that downloads the Monero miner. (Aside: this is quite common behavior among bots. They do all manner of things besides their primary function, including installing patches on the victim machine, sometimes to close the very vulnerability that allowed them access to the device in the first place. This almost sounds...benevolent...until you remember that they are there to eat your resources to mine coin for their operators)
- Moral of the story: please, please do not expose Docker instances openly on the web, unless they’re honeypots. It’s trivial to at least force it to use SSH authentication, and of course there’s more you can do beyond that. Also--don’t run containerized applications as root (but Breaking Badness listeners would never do that, right?)
- Second moral of the story: hey, at least it’s not ransomware!
A Pi in the Sky Can Pwn Your i(phone)
- Researcher Ian Beers of Google’s Project Zero discovered a flaw in iOS versions prior to 13.5 which allowed no-touch code execution
- He accomplished the attack itself using a Raspberry Pi (illustrating that it doesn’t require massive compute resources).
- The one Pi was able to simultaneously reboot, and pwn, multiple phones in close proximity
- Since this attack uses RF (802.11), an attacker could theoretically increase the range from which the attack could succeed by using a high-gain antenna and/or boosting the output power.
- The exploit uses Apple Wireless Direct Link (AWDL), which is a low latency/high speed WiFi peer-to-peer connection that Apple uses for things like AirDrop, unlocking devices via Apple Watch, etc.
- (Aside: there is a group, Open Wireless Link, which seeks to open source these capabilities for interoperability. Find out more at https://owlink.org)
- Ian’s (the researcher) persistence was formidable; achieving this PoC took several months of work. The story actually goes back to 2018, when Apple inadvertently leaked function name symbols in an iOS beta build. Ian discovered a function related to parsing AWDL, and started digging into the assembly underneath that.
- While Apple patched this particular flaw in iOS 13.5 and later, it’s a sure bet that there are folks out there looking for other bugs adjacent to this one. Further exploits may be exposed.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
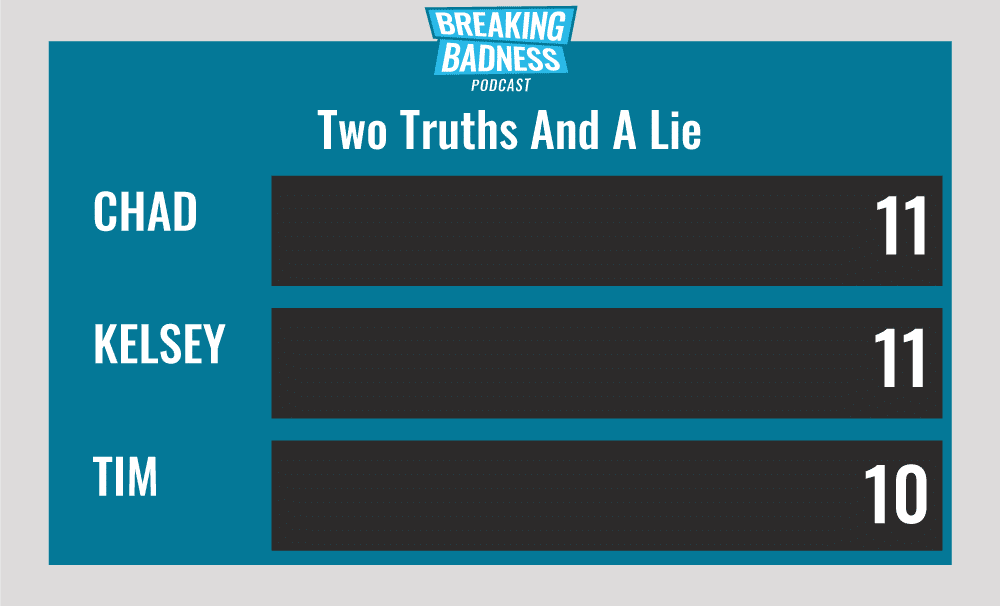
Current Scoreboard
This Week’s Hoodie/Goodie Scale
A Miner Docker Attack[Chad]: 3/10 Hoodies[Taylor]: 2.sleeve/10 Hoodies
A Pi in the Sky Can Pwn Your i(Phone)[Chad]: 5/10 Hoodies[Taylor]: 7/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

