Coming up this week on Breaking Badness. Today we discuss: Racking Our JetBrains, SolarWinds Krebs for Mercy, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Racking Our JetBrains
- We continue to see new targets as people have brute forced portions of the domain generated algorithm (DGA), or rather what was thought to be a DGA but is actually an encoding scheme. The FNV-1A hashes continue to be brute forced as well that contained various things the malicious DLL was looking for before continuing with its execution. Kaspersky in fact leaned in on this and spoke about how there are some similarities in the code between the Kazuar backdoor and the SUNBURST backdoor based on timing, hashes, and some other shared elements. Then on top of that all of course we have this accusation that JetBrains was leveraged in the attempt to get into SolarWinds Orion code base from JetBrains’ TeamCity CI/CD pipeline server which is kind of like a Jenkins or other build server—automatically builds software over and over again as changes are made by developers and runs tests to make sure it works as intended, runs security checks, etc.
- JetBrains is a Czech company that makes software used by developers all over the world. They make IDEs primarily—integrated development environments—that have all of these nice features that make developing software a little bit easier for programmers. IntelliJ is a huge one of them for developing Java applications, PyCharm for working in Python, GoLand for working with Golang and whatnot. Each has hand holding features and other niceties that many experienced developers refuse to work without.
- So reportedly—according to the New York Times and Washington Post, both of which reporting on this seems a little dicey to me—they are investigating the use of TeamCity as a platform for the initial infection into SolarWinds. This would indicate then that the people behind the Sunburst backdoor first breached JetBrains, created a malicious build of TeamCity, got that update installed at SolarWinds, breached SolarWinds using that, created the malicious version of the Orion tool, then got that pushed to target organizations, then breached those organizations and continued laterally with CobaltStrike and whatnot as mentioned elsewhere. Any time I see that many layers of complexity I am suspicious, but I’ve been surprised before.
- Initially JetBrains responded with denial since they had not even heard that they were being investigated. The CEO said on Twitter that the company would fully cooperate with any investigation if authorities did reach out to them
- JetCity is not entirely, but rather confident that their product was not abused in the SolarWinds attack. If I were able to bet on cybersecurity incidents in Vegas I would say that what I’m guessing likely happened here is that there is a build script executed by TeamCity that was running on SolarWinds’ instance which was doing the packaging of the malicious DLL or hiding it from prying eyes during their build process. This was mentioned to the press and they ran with “TeamCity hacked” when it was really just the CI/CD server executing build scripts as it normally would. Again, I’m willing to be surprised, but the layers of complexity here don’t add up. Hackers do the bare minimum to be effective and achieve their goals. That’s over three vendors out from their intended target and a lot of moving parts and security to bust through toward their end goal. Could of course just been speculative work, but again it’s rare that people running an espionage or cybercrime operation would choose to do something so speculative without end goals in sight.
- In regards to recommendations of organizations can of course check and see if the version of SolarWinds Orion your company is using is one of the affected versions. From there you’ll want to follow your standard DFIR process. If the answer to the question is yes it’s still unlikely that the people behind SUNBURST chose to act on your infection. Many major companies were not of interest in their operation and were never breached with further goals. However, quarantine and analyze, that’s all you can really do.
SolarWinds Krebs for Mercy
- You might have heard Chris Krebs’s name recently, because he was the head of CISA, the cybersecurity and infrastructure security agency, and he was fired shortly after assuring the public that the November elections had been conducted securely and smoothly (and a lot of his work had gone into the effort to make that the case). All of us in the community knew he’d have a ton of options on the table after that firing, and what he did was team up with Alex Stamos to form something they’re calling the Krebs Stamos Group. Well, it didn’t take long for that new company to land itself a high-profile job: helping SolarWinds with where to go from here.
- I think it was a great move on SolarWinds’ part—it suggests they’re taking their future quite seriously, and by extension, the security of their many, many customers. I think it’s safe to say that SolarWinds is in an existential crisis at the moment, and to me, a move like this will help the perception of them. It’s good PR, but I believe that they’ve done it for a lot more than just the PR aspect, because Krebs and Stamos are not just going to go in there and help SolarWinds craft up some public statements; they’re going to really get the house in order.
- Here is a blog quote from their CEO, Sudhakar Ramakrishna: "We have engaged several leading cybersecurity experts to assist us in this journey and I commit to being transparent with our customers, our government partners, and the general public in both the near-term and long-term about our security enhancements to ensure we maintain what's most important to us—your trust."
- They also told ZDNet that they’re looking for guidance on their posture and policies, to help them evolve into the kind of company they want to be after this.
- SolarWinds is on the NYSE, and as you can imagine, they didn’t get any love from the markets when this news broke. They’re currently trading at a little more than half of what they were at before this hack was announced—all you have to do is look at their 1-year chart on a finance site, and you’ll be able to see exactly when this hack was revealed. Interestingly enough, this is not the lowest their stock price has been in the last couple of years, so the market clearly isn’t giving up on them. I can’t help but think that this move to hire such well-respected security experts will at least calm investors down a bit. Of course, in the long run we’ll have to see what happens to their customer base.
- I have a few thoughts on how companies should deal with negative news. Obviously one of the first points is that bad news never ages well. But there’s a reason crisis comms is a thing: there is a specific discipline around how you communicate when there’s been a big corporate disaster, and part of that is this balancing act on how much you disclose and when. For one thing, you have to know, yourself, what’s going on, in order to communicate effectively about it. But if it takes time to even gain that level of situational awareness, then I think you do have to at least make an acknowledgement, even if it’s just in the spirit of “we acknowledge that something has happened, we’re on it, and we’ll keep you informed as soon as we know more.”
- I think humans tend to be relatively forgiving of mistakes that other humans make. Most of us have a degree of empathy, as well as the sense that it’s never out of the question that we could find ourselves in an uncomfortable spot sometime, and we’d hope the world would not jump to a snap judgment about us, either. So transparency is important, but so is making smart moves beyond just the transparency, to show that you grasp the moment of the situation and that you’re being smart about how you proceed.
- I think public disclosure gives other companies an object lesson in what not to do, for one thing! This goes back a ways, but for those who remember the Sony hack in 2015, they basically were facing extortion from the attackers, demanding that they not release a film about Kim Jung Un, and they caved to the attackers. That brought a lot of criticism, even from then-president Obama.
- In the face of reporting on misuse of its data, and its relationship with Cambridge Analytica, Facebook also took a lot of heat—they sort of went into hiding for a while, and of course that created an environment for both speculation and criticism to thrive.
- So missing the mark on disclosure of issues has a lot of potential ways to backfire, from erosion of public trust, to losing customers, to losing market value and share. With cybersecurity, there’s the added concern that silence in some cases may risk your customers’ security itself. You don’t want to make a bad thing worse. So to end on a positive note, I will reiterate that I think this move on SolarWinds’ part, hiring Chris Krebs and Alex Stamos, was a good one.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
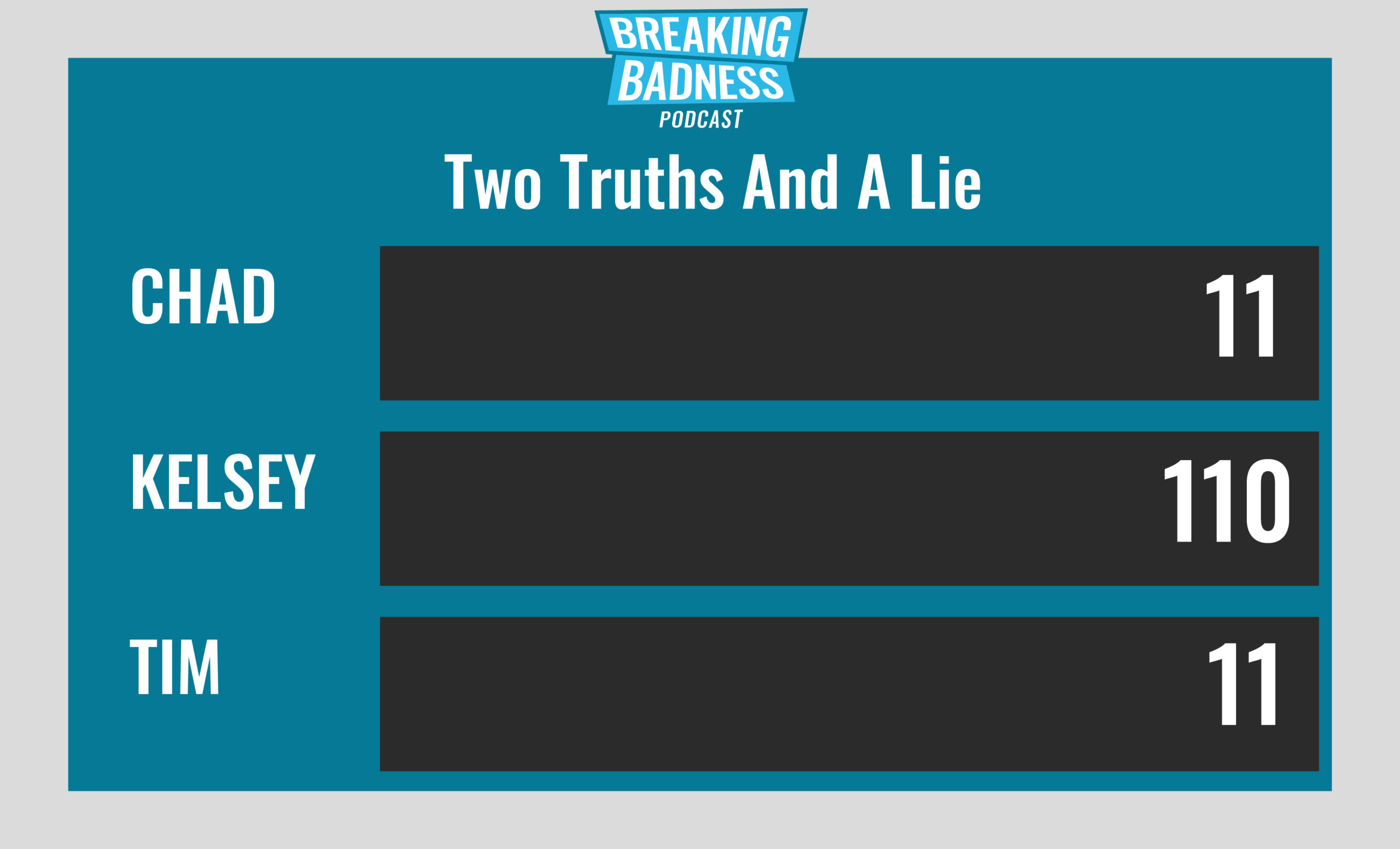
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Racking Our JetBrains[Chad]: 3/10 Hoodies[Tim]: 7/10 Hoodies
SolarWinds Krebs for Mercy[Chad]: 7/10 Goodies[Tim]: 8/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

