Coming up this week on Breaking Badness. Today we discuss: Everything Under the SUNBURST, Private Documents Vaccine Better Days, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Everything Under the SUNBURST
- There were quite a few interesting ways SUNBURST evaded detection:
- Use of “aged” or “seasoned” domains with creation times often years prior to the start of the campaign.
- Use of per-victim, and potentially even per-host, C2 domains and prominent cloud hosting providers.
- Victim-specific Cobalt Strike Beacon configurations.
- Significant separation between SUNBURST SolarWinds backdoor and follow-on TEARDROP/RAINDROP payloads to load CobaltStrike.
- SUNBURST C2 infrastructure appears to consist of re-registered, long-term adversary owned, or adversary compromised items with years of history prior to use in this campaign.
- Use of Namecheap, Epik, and NameSilo registrars, dnsowl and registrar-servers name servers, and cloud or colo hosting providers.
- The main takeaway at this time is just emphasizing the extended and deliberate nature of this intrusion, which started no later than September 2019 and continued through October 2020.
- The Cobalt Strike details are especially interesting, both the deliberate and stealthy way in which the attacker transitioned from SUNBURST to Beacon loaders as well as the anti-analysis and anti-forensic techniques used to defeat detection and analysis.
- The main takeaway is one we’ve been emphasizing at DomainTools since December - that an indicator-based, reactive defense posture to an intrusion such as this will yield too much advantage to adversaries, and make for a much more difficult cleanup (if an intrusion is even detected at all).
- Organizations need to leverage all sources of data and enrichment available to them in order to identify suspicious activity which could indicate stealthy or supply chain-delivered attacks.
- There is no immediate impact to this information as the campaign has now been exposed, and the adversary has likely cleaned up infrastructure and other artifacts of intrusion. However, we need to be aware of the fundamental behaviors used in this event as we will likely see similar activity in the future.
Private Documents Vaccine Better Days
- EMA is the European Medicines Agency which is the European Union’s drug regulator. They are the equivalent of the United States’ Food and Drug Administration in that they approve or deny vaccines. They are who all of the vaccine manufacturers submitted their approval documents to and had been under some scrutiny due to their delay in approving vaccines last year.
- So here’s the thing. The documents were purposefully manipulated then released. The manipulations have made both Pfizer and the EMA look misleading in the reputability of the vaccine. The cause here from the attackers is to undermine trust in vaccinations and, from my perspective, keep Europeans from trusting in and getting vaccinated as soon as possible.
- Nothing on how exactly they discovered it only that emails had been grabbed in the attack. If I had to bet—this would be some credential phishing that led to a compromised account with the correspondence.
- They have. On EMA’s site they have five blogs or so now with updates as they discover more during their investigation. Typical stuff you would expect to read up on with these sorts of breaches. Working with law enforcement, engaged a third-party firm for investigation
- I think we’re looking at someone who wants to undermine the trust in the vaccine for a social reason and interrupt a rapid vaccine roll out backed by public trust. It’s really hard to say who is behind so I really shouldn’t even try, but in modifying the contents it’s clear their objective was to spread disinformation about the vaccines.
- This past year, if anything, we have seen a never ending deluge of disinformation for each stage of the COVID-19 process from initial alarm to sporting event cancellations to PPE sales to fake vaccines to now vaccination lures for phishing credentials and funds. This isn’t so much a trend as the new normal or at least the normal for now. I’m concerned only in that it continues to annoy the hell out of me that adversaries keep targeting this global fear for profit.
- As we’ve seen with so much these past few months with Solarwinds, a dedicated attacker will always find a way no matter how many vendors they work their way through. The goal should be to limit the blast radius or make success so expensive that most attackers give up. Ways you can do that? Multi-factor Authentication is one road block for less complicated attackers. Encrypted emails and documents if you’re sharing confidential documents over email as they were in this case. If it’s confidential you should probably encrypt it instead of sending it over a likely unencrypted network connection like many SMTP servers are or can be downgraded to be even. Lastly I’d suggest implementing egress filtering for networks handling this confidential information. At some point exfiltration was a requirement here and filtered egress would have made another roadblock for adversaries to make this more expensive to achieve.
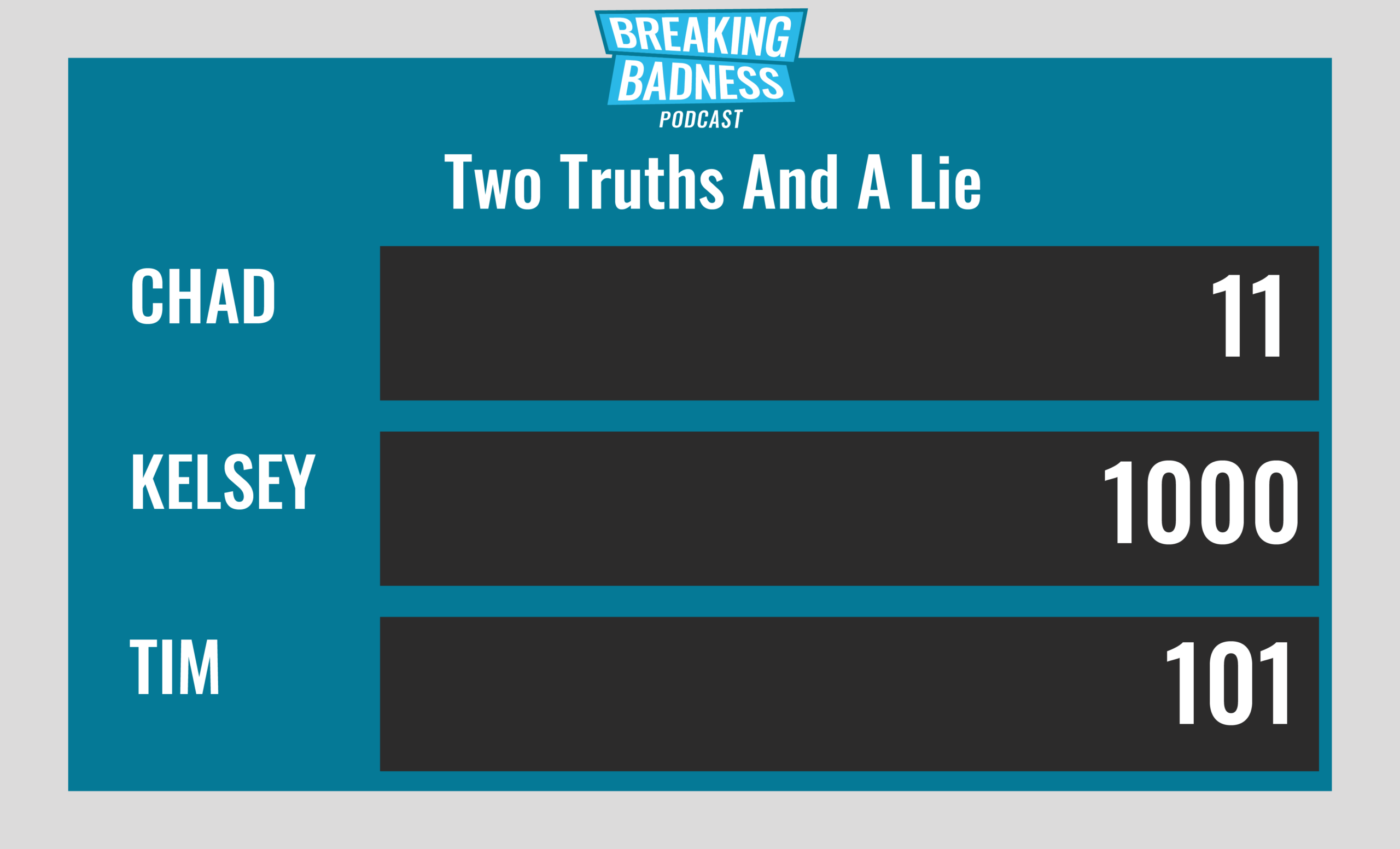
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Everything Under the SUNBURST[Chad]: 8/10 Hoodies[Joe]: 8/10 Hoodies
Private Documents Vaccine Better Days[Chad]: 3/10 Hoodies[Joe]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!


