Coming up this week on Breaking Badness. Today we discuss: Hedging Your Emotets, The Root of All Evil, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Hedging Your Emotets
- Emotet is a strain that’s thought to originate from Russian cybercriminals and first showed up around 2014. Typically delivered through a malicious email attachment, it has been just about everywhere, super prolific, with lures for just about everything. Some people call it Heodo as well, should mention that, depending on the AV vendor. Emotet though started as a banking trojan, stealing credentials, the usual, but then shifted a few years down the road to a loader that allows for pulling down other payloads. This led to them then running a kind of Malware-as-a-Service botnet where they would deliver payloads for others. That’s where we started seeing Emotet deliver TrickBot and QBot which of course has been spotted leading to Ryuk ransomware and others.
- Netwalker is a ransomware that in early 2020 shifted to being ransomware-as-a-service and the affiliate model. The original author began recruiting people to spread the malware on cybercrime forums. Typical affiliate programs like multi-level-marketing, the Avon and HerbaLife of ransomware. And as suspected, CIS country based companies are prohibited from being targeted so no Russia, etc. Netwalker has had some pretty high profile victims including Michigan State University. I believe just under 200 infections in 2020 so their affiliates have been pretty busy all around. And we should note that authorities didn’t take down Netwalker itself but rather just the leaks site they use for double-extortion of their victims
- The dismantling was coordinated by Europol and almost a dozen countries. The work allowed them to do a few things: one was seizing physical infrastructure, another was taking over the botnet itself, and the third was injecting code to have Emotet delete itself in April 2021. All together a pretty herculean effort to take down the most professional of botnets out there. I honestly thought I’d be stuck seeing Emotet emails come across my desk for years to come. Happy to have it slow down even if for a bit.
- They seized a number of the administration servers that are around the world and redirected victims to law enforcement-controlled infrastructure before the April delete date. They also raided an apartment in the Ukraine of one of the Emotet operators and seized quite a bit of equipment.
- They released a joint statement, but I haven’t seen any personally that came from individual agencies. I know that most of the countries involved have had a major infection of Emotet at the government level so they are likely celebrating quite a bit. Lithuania’s national health organization for instance had a huge problem with Emotet just a few weeks ago in December of 2020.
- In terms of the impact of this operation on Emotet, I expect it’ll be slowed, but unlikely that it’s dead. I think that given the scope of the operation there was definitely more than one operator out there in the wild. That apartment in the Ukraine wasn’t nice enough for the amount of cash that Emotet has raked in so was probably middle management if I had to venture to guess. While this will stop the botnet for now Emotet’s at large operators are definitely writing code this very moment to try and take back control or even begin a new wave of infections. I can’t imagine they would sit idle after losing that cash flow source. Though, then again, maybe I’m wrong and they take this as a chance to retire. Maybe it’s a chance to write a whole new thing more dangerous than Emotet ever was with all the lessons learned.
- No information/statements from Emotet that I have heard, but I have to admit that I have been pretty head down and not paying attention to any communiques on the darkweb or anything. I’m guessing there’s been a lot of swearing and panic in some part of the web though, just not one I have access to right now.
- I do not personally know of any instances where Emotet was used to deliver Netwalker, but I wouldn’t be surprised if that was the case and I missed it simply because of how prolific and widespread Emotet was as the door to networks for ransomware affiliates.
The Root of All Evil
- Sudo is a magic command that gives you godlike powers. The “su” stands for super user, so it’s basically “super user do.” When you’re not logged in with root privileges—which is how you typically want it with general users, not to mention processes—you can’t perform various kinds of commands—unless you type sudo first.
- A moment ago I said that you typically don’t want general users to log in as root (or as “administrator” on Windows) and that’s because of this principle of least privilege. The principle is that any entity that interacts with the system, whether that’s a human or a process running on a machine, should have the least privilege necessary to perform their functions. The point is that anything—or anyone—can potentially be compromised, and when the thing that’s compromised has the keys to the kingdom, so to speak, you can have considerable problems. So that’s why when you’re not logged in as root, you have to use sudo for commands that require root privileges, and you get prompted for a password (and if you’re not among the users who are “sudoers” then you’ll get rejected). Really, everything in security in some way comes down to least privilege—the problems occur when someone or something escapes the boundaries of the privileges they should have.
- First off, the vulnerability that was reported last week has an awesome name: Baron Samedit. In case you’re not up to date with your Hatian Voudu deities, this is a pun on Baron Samedi, or Baron Saturday, who is a spirit of the dead who’s a colorful troublemaker of sorts. The pun here is on a command called sudoedit, which is a key part of the picture here. Stepping back—this is a buffer overflow vulnerability, where the system accepts input where it shouldn’t. The reason that happens in this case has to do with the escape character, the backslash. Normally, the backslash escapes control or logic characters (like the exclamation mark which acts as a NULL), but due to the flaw in this CVE plus a second one in sudoedit, if the command line argument the user is sending ends in an unescaped backslash, the system will accept input beyond there—something it’s not supposed to do. An attacker can use that to overwrite memory, with an arbitrary buffer size. So if you run sudoedit with the -s or -i arguments on an unpatched system, this bypasses the automatic special character escaping that sudo is supposed to do.
- Essentially, it’s a privilege escalation flaw that can theoretically give an attacker control over the system in question. That’s generally considered a Bad Thing, and depending on what the system in question is, and what network segment it’s on, it can be a Very Bad Thing. Now, there is one mitigation to the severity of this, which is really a two-parter: 1) the attacker needs local access to the system, and 2) the system needs to contain a file called “sudoers” which determines which users on the system have sudo privileges. But a vast percentage of Unix systems will in fact have the sudoers file, and there are various ways to get access to a system, so don’t take too much comfort in that mitigation.
- I wouldn’t necessarily think of it as leveraging Sudo, in the sense that just about every organization has at least *something* running some flavor of Unix, and that something probably includes sudo and the sudoers file. So even if you don’t *use* the sudo command, pretty much all the Unix variants support it, so this applies to basically everyone. And what you need to do is patch :) Patches for a bunch of distributions are already out, and we’ll likely see more of them in the coming days
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
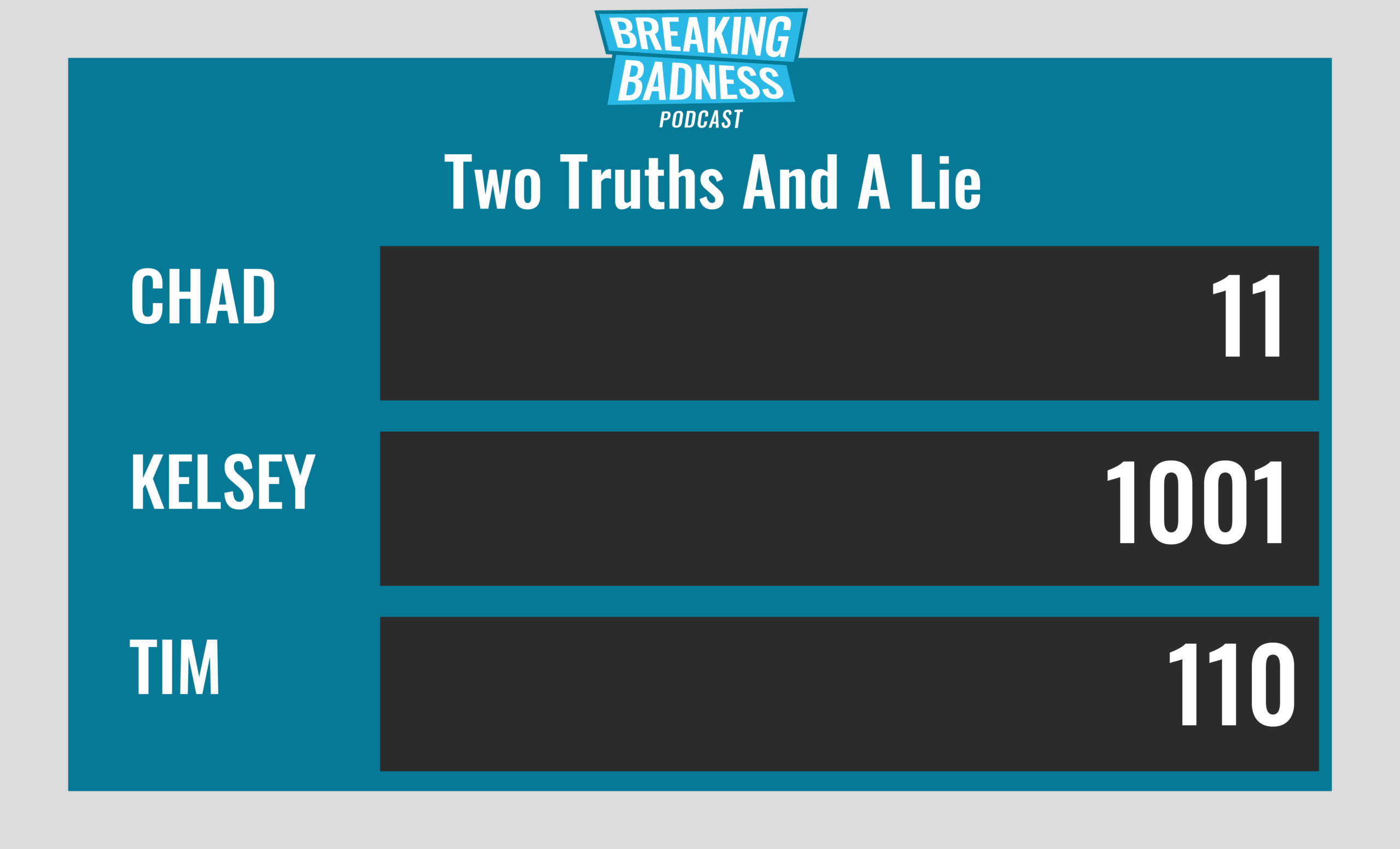
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Hedging Your Emotets[Chad]: 8/10 Goodies[Tim]: 5/10 Goodies
The Root of All Evil[Chad]: 6/10 Hoodies[Tim]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

