Coming up this week on Breaking Badness. Today we discuss: You Think That M1's a Tank? It Just Got Popped, Dependen-Seize the Day to Hack, and our fun game, two truths and a lie.
Here are a few highlights from each article we discussed:
You Think That M1's a Tank? It Just Got Popped
- Apple’s new M1 chipset delivers a lot of performance by using specialized system-on-a-chip hardware for various functions. It’s a new chip architecture.
- As such, just as with legitimate software, malware has to be specially constructed to run natively on it
- A malicious Safari extension was discovered by Patrick Wardle last week (week of Feb 15), the first as of that time to be known to be M1-specific
- By the time we recorded the podcast a few days later, at least one other malware, dubbed Silver Sparrow, had appeared, also crafted for the M1 Macs
- The malware serves up ads and can redirect users to malicious websites to drop additional payloads
- This and other M1-specific malware may pose a bit of a challenge for a little while, for AV engines, although behavior-based analysis shouldn’t be affected by the different chipset. Static analysis technologies may take a little while to catch up
- We’re likely to see a slow rise in M1-specific malware, but it’s worth remembering that for malicious actors to get the most bang for the buck, they’ll be optimizing for what’s most common, which as yet still is definitely older architectures.
Dependen-Seize the Day to Hack
- Researcher Alex Birsan did some experimentation with popular package managers to see how easy (or difficult) it might be to introduce new supply chain malware
- Turns out, it was not that difficult. It took work, but the work yielded interesting results.
- Stepping back a bit, package managers are software that is used to install other software, or components. They are usually invoked from a command line or by a script, so their operation is opaque to the typical user
- Another researcher, Justin Gardner, had discovered some Node.js source code on GitHub that was meant for internal paypal usage, containing a manifest that included public AND private dependencies. This sparked Alex’s work
- Alex found that by spoofing the names of packages enumerated in the dependencies, they could install malicious (or in this case, imitating malicious) code
- The extent of their success was harrowing; very large companies were susceptible to this kind of attack, including some of the biggest names in the tech industry
- This led to some nice bug bounty payouts for Alex!
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
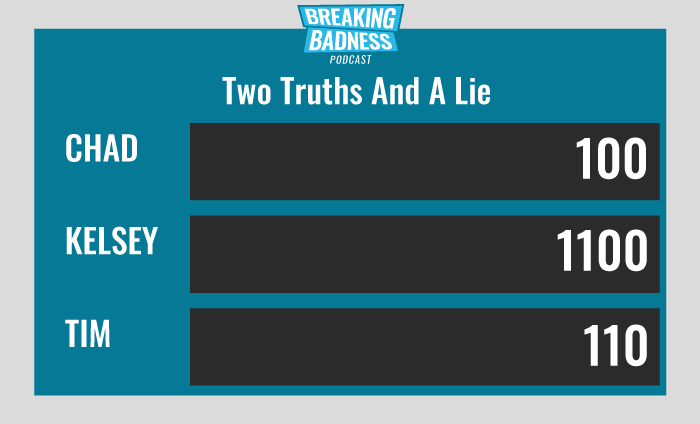
Current Scoreboard
This Week’s Hoodie/Goodie Scale
You Think That M1's a Tank? It Just Got Popped[Chad]: 3/10 Hoodies[Taylor]: 4.sleeve /10 Hoodies
Dependen-Seize the Day to Hack[Chad]: 6/10 Hoodies[Taylor]: 7.zippers.sleeves.drawstring/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

