Coming up this week on Breaking Badness. Today we discuss: Exploits Leave Me In Low Spirits, The Element of Surprise, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Exploits Leave Me In Low Spirits
- SPECTRE is a vulnerability that affects modern processors that do speculative branch execution. This is a feature to speed up execution by guessing which way the execution is going to go and preprocessing. So what happens is during that preprocessing, trying to predict what the user will want next essentially, private data is sometimes loaded into the processor’s cache. When there is a misprediction that data is sitting in cache and can be accessed, what is known as a side channel attack, when mixed with some specific timing. This came out with a whole host of other vulnerabilities that exploit the very nature of how these processors work such as MELTDOWN and others. The problem here with fixing this for Intel was that not doing predictive execution drastically slowed down their processors and since the attacks required running malicious code locally so a lot of people didn’t even bother to apply the microcode update from Intel that I believe just disabled speculative execution. However, a number of these attacks have come out and been demonstrated as working remotely and without the need for attacker controlled malicious code. And now we’re seeing even more refinements.
- This kind of vulnerability and its possibility has been kicked around since the early 2000s actually, long before Voisin’s research. People have seen this as a problem in how these processors were designed but it took some serious technical chops to perform the attack so it was just left around as a problem. Plus the improvement in speed was seen as a big boon for processor manufacturers, right? Julien I believe found this specific exploit for this vulnerability on VirusTotal.
- The exploit that cropped up on VirusTotal can reliably dump any file within a few minutes. It continuously tries to load a file then tries to grab it from the cache. That’s the timing bit. Basically just keeps requesting the file so it keeps getting loaded into cache at some point then does some timing magic to pull it out of cache.
- CANVAS is a tool from ImmunitySec that’s an automated penetration testing tool. I basically think of it as a souped up metasploit but written in Python. A lot of the exploits for CANVAS were leaked this last week and with that comes this exploit. Basically you point this tool at a system, say go, and wait for it to deliver root to you. It’s kind of a skiddie dream to have right, kind of like when Cobalt Strike’s source code was leaked for Beacon. A very robust tool that is now floating around out there.
- To ensure your organization isn’t exposed to this vulnerability, buy newer processors where this is presumably fixed. You can apply the microcode updates for processors that do have this problem. There are also a few situations where the exploit doesn’t work, but I believe that someone has already published a workaround for the SMAP problem mentioned in Voisin’s blog post. If you’re in the cloud most providers applied updates a long time ago since otherwise they’d have a lot of security problems right now.
- If a threat actor were to take advantage of this vulnerability, basically any file can be read. Password files and encryption keys being the primary target, right? This vulnerability existed before, but took some technical chops to exploit so this skiddie-friendly exploit will likely make its round into some malware shortly.
The Element of Surprise
- The name (HAFNIUM) is from Microsoft’s convention of naming threat actor groups after elements. They attribute this group to China; its victimology seems to be mainly American, and it has hit across a variety of industries and sectors. The main goal seems to be data exfiltration, and according to Microsoft, they are a pretty sophisticated group. This activity, where they’re exploiting the vulns we’re going to talk about here, is typical HAFNIUM behavior because they tend to target public facing servers. If they’re successful, they exfiltrate the data they’re interested in to download sites like MEGA.
- The important thing to keep in mind about these vulnerabilities is that they involve unauthenticated remote code execution, and this is why some folks in the industry were saying last week that the weekend would be canceled. I hope that wasn’t the case for too many folks, but 0days with RCE are a big deal, especially when they are in something as prevalent and business critical as Exchange. Now, having said that, the other piece of setup I’ll do here is to say that this affects onsite Exchange only as you mentioned in the intro. That used to be all Exchange, of course, but now that a lot of companies are using O365, the proportion of businesses affected is lower than 100%.OK, the vulnerabilities themselves are these:
- One is a server side request forgery vulnerability. This allows an attacker to send arbitrary HTTP requests, and authenticate to the Exchange server. Since I mentioned that these are unauthenticated 0days, this means that the attacker doesn’t have to have legit credentials to do this (else obviously they wouldn’t have to lean on the vulnerability to gain access)
- Next we have an insecure deserialization vulnerability. Briefly, serialization is a process that converts objects into a byte stream, such as for sending over a network, and deserialization is reconstructing the object from that byte stream. Insecure deserialization is when user-controllable data is deserialized by a website, and it allows a way for an attacker to insert objects into the stream. Technically user data really shouldn’t be deserialized for this reason. In the case of this Exchange vulnerability, it allows the attacker to run code as SYSTEM, which is basically root. Not good.
- The next two are both described identically in Microsoft’s advisory. They are post-authentication arbitrary file write vulnerabilities. Since the first two vulnerabilities in this chain allow the malicious actor to authenticate, clearly by the time they get to this one, they’ve satisfied that requirement, so they can in fact write anything they want to the server.
- When attackers successfully exploit the above vulnerabilities, they typically establish presence stuff. They installed web shells, which then facilitated further operations, such as stealing data, which as we know is HAFNIUM’s stock in trade.
- The thing you read about in the accounts of this activity is that they have dumped full contact lists. That’s bad enough, and I have to assume that many organizations may well have other services running on the box that’s hosting Exchange, so there’s any range of things they might be able to get their hands on. Critically, the backdoors that they’re installing here will not necessarily be removed when you patch, so although patching is as critical as any Patch Tuesday patch in recent memory, your work is not done when you’ve patched.
- Even if you’ve put the server behind a VPN—which would have protected you against this exploit if you’d done that before the vulnerabilities started being exploited—HAFNIUM can still get in. So you’ve still got the risk of continued espionage, exfiltration, and hardening of the backdoor access.
- If organizations have on-prem Exchange that was not sitting behind a VPN prior to whenever HAFNIUM started exploiting these vulnerabilities, which goes back at MINIMUM to January, but very likely before then...then organizations have to assume they are compromised. Anyway, there’s a series of Indicators that Microsoft describes in the advisory, which are too numerous and complex to go through in a podcast, but basically there’s a series of log entries and events, as well as a lot of file hashes and file names that can all be searched for to find signals of compromise.
- I’ll start off by saying that the silver lining to this as well as the SolarWinds stuff is that there’s been really good, transparent disclosure of these things, and it has been swift. Volexity and Dubex shared info with Microsoft and got well-deserved props for this from Microsoft in the advisory. Volexity’s blog is detailed—it’s worth a read, in addition to the Microsoft write up. This kind of collaboration is absolutely to be commended.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
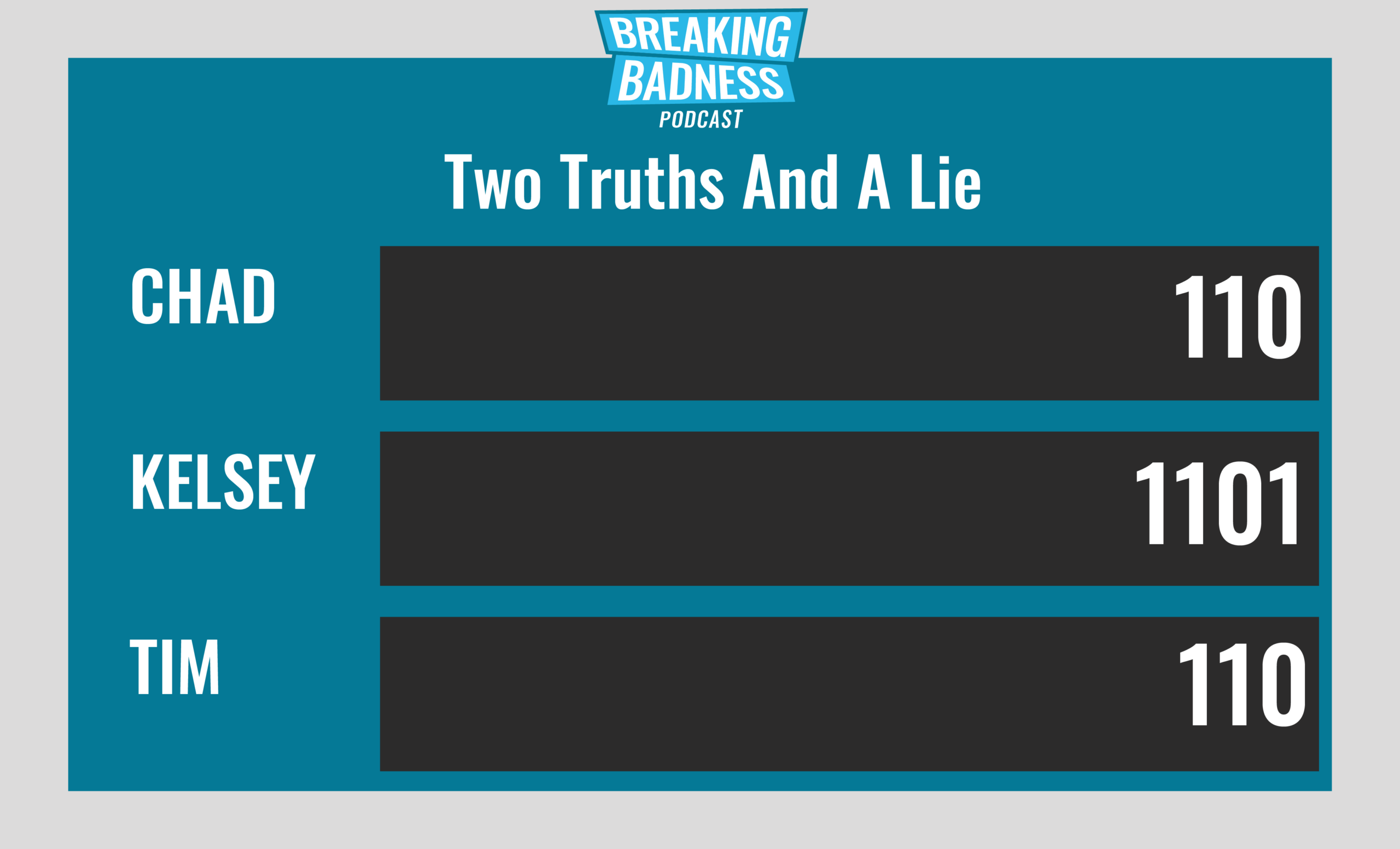
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Exploits Leave Me In Low Spirits[Chad]: 4/10 Hoodies[Tim]: 4/10 Hoodies
The Element of Surprise[Chad]: 10/10 Hoodies[Tim]: 10/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!


