Coming up this week on Breaking Badness. Today we discuss: The Oldest TrickBot in the Book, The Big REvil, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
The Oldest TrickBot in the Book
- TrickBot’s been around since 2016. It’s a banking trojan, so as you’d probably guess, it aims to steal from banks, but it can also drain bitcoin wallets. It also uses mimikatz to harvest credentials, and it is frequently used to download Emotet, Ryuk, and other famous ransomware. It’s a multi-trick bot for sure. If you look at the CISA advisory we link to in the show notes, you’ll see that the set of MITRE techniques it carries out requires a fair bit of scrolling to get through.
- One of its distinguishing features is that it continues to evolve; its authors keep adding new modular features and capabilities. One interesting thing about TrickBot is its use of compromised wireless routers for C2. There are a lot of those available…we could do a whole month of shows on home router vulnerabilities.
- Listeners might recall how Microsoft and others took some legal action to shut down chunks of TrickBot’s C2. The main cited concern at that time was to protect the elections, but of course it also hampered their financial operations too. That was a good thing, but I think we all knew at the time that it wasn’t likely to be the death knell for this malware.
- The advisory specifically calls out a spearphishing campaign, which is designed to get the victim to download TrickBot. This campaign seems to be primarily targeting North American organizations, and the lure is a notice of a traffic violation (like road traffic, not Internet traffic!).
- As we’ve seen, there’s a pretty wide range of things that could happen to anyone who installs TrickBot. With this specific campaign, the link in the email (which says it has proof that you committed a traffic violation) is to a website, which is sitting on a compromised server (as opposed to purpose-built infrastructure), has a link to supposed photographic proof of the violation. Instead, it downloads a malicious JavaScript file that establishes C2 communications. From there, the advisory didn’t have much to say about which specific goodies are going to be installed; it just lists examples of some of the follow-on payloads that might be installed and run. Did I mention that it can load a cryptominer? That it can use SMB to move laterally?
The Big REvil
- It’s been a minute since we’ve seen something new from REvil—or maybe other explosions have just been happening all over the Internet instead so we missed it. In any case, REvil is a malware family based off of Gandcrab which is often called Sodinokibi as well. It’s a Ransomware-as-a-Service or RaaS offering that has kind of a pyramid of workers that pass money on up the chain. The REvil developers take something like a 30% cut from those doing the infection and ransoming and this has them estimated to making over $100 million a year in some cases. Rather impressive numbers. For a time last year REvil was everywhere and is still a big problem but other ransomware families have been busy as well, likely inspired by the numbers REvil was putting up in 2019 and 2020. There has also been some renewed interest due to a recent interview in The Record with someone claiming to be the REvil author—all hard to verify, right?
- Windows Safe Mode goes back to at least Windows 95 as I’m aware of it. The whole purpose is to only load the most essential things necessary to run your computer’s operating system. It’s the equivalent of the hardware troubleshooting step where you remove everything and add one component at a time until you figure out what went wrong. Almost all major operating systems implement it now since it’s so easy with how modular software is to absolutely bork your machine.
- Autorun is a common persistence mechanism to place something into a registry key that will auto-load every time you login. In this case they have placed a few registry keys around such as AstraZeneca and franceisshit. These both are used to boot the computer into safe mode.
- MalwareHunterTeam didn’t say how they came about the sample, but through regular hunting. What’s kind of fun here is you see a few things that REvil is likely doing—or can be inferred—that first they are using WinExec likely to avoid detection since that function is for old, old 16-bit Windows and these days CreateProcess is almost always used. They’re also likely booting into SafeMode to avoid EDR solutions which is sneaky to say the least.
If I’m reading it correctly when autorun launches REvil, it will, or could potentially, reboot into safe mode with networking turned on and then used to launch the encryption portion and ransom the user’s files. - After the device is fully encrypted, basically it’s time to pay up. REvil also has a page where they sell data of victims that don’t pay up so more than likely while things are being encrypted they are also being exfiltrated to a REvil controlled server.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
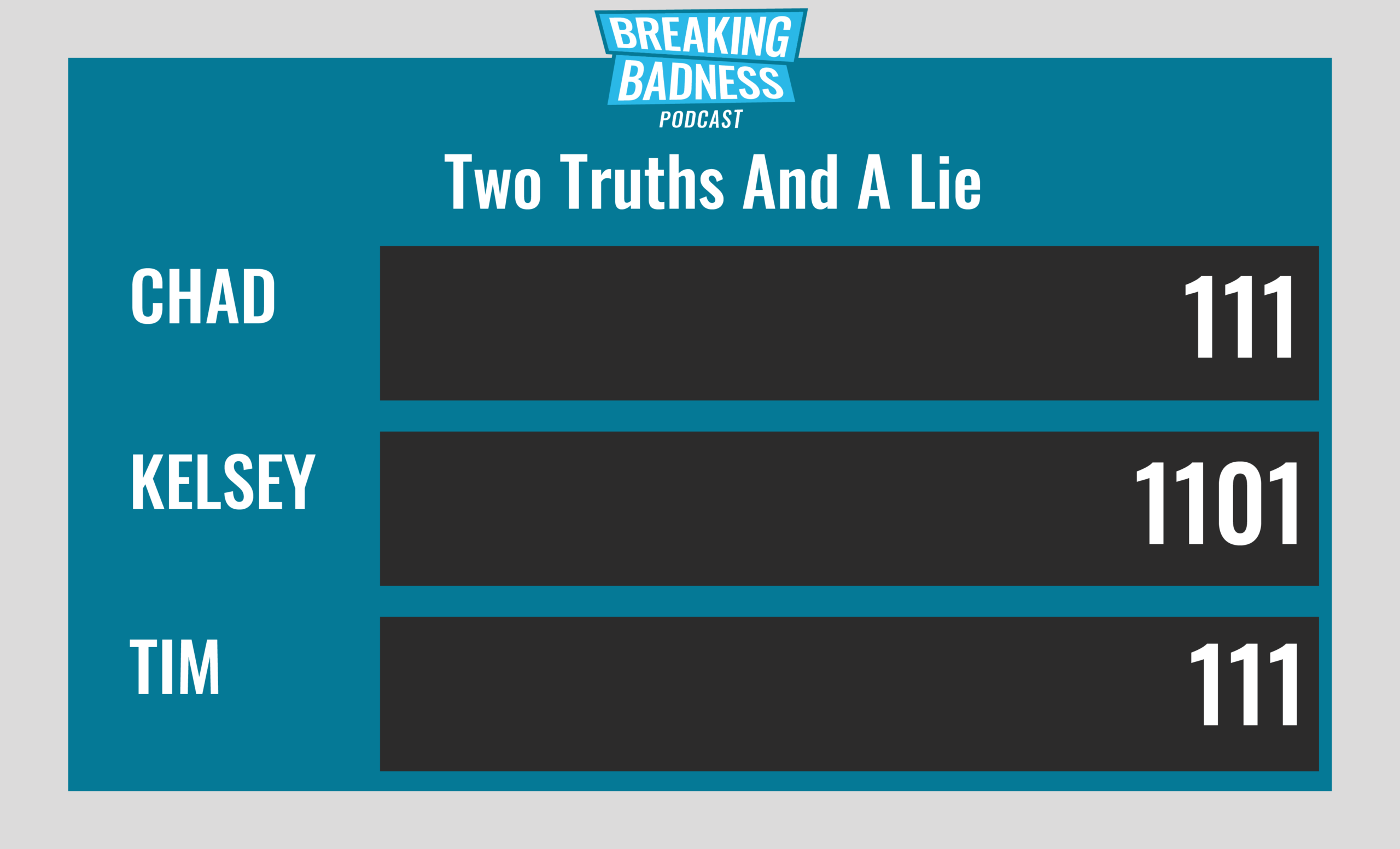
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Oldest TrickBot in the Book
[Chad]: 7/10 Hoodies
[Tim]: 6/10 Hoodies
The Big REvil
[Chad]: 0/10 Hoodies
[Tim]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




