Coming up this week on Breaking Badness. Today we discuss: Pwn2Own Goes According to LAN, Threat Actors Rarely Cut Users Any Slack, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Pwn2Own Goes According to LAN
- Pwn2Own is a big event organized by the Zero Day Initiative to find zero day vulnerabilities in common software with the goal of connecting companies and zero day researchers through some money. Encourages researchers then to report the vulnerability instead of selling it to governments or otherwise. Responsible disclosure at its finest. It’s a 2 day event and we always see some pretty high profile bugs come out.
- Big software firms usually looking to beef up their software volunteer as targets. It can be a nice thing to get out of pwn2own without a huge vulnerability being discovered.
- This year, two white hats discovered a string of three vulnerabilities in Zoom desktop clients that led to full remote code execution.
- A remote code execution vulnerability or RCE is when an attacker can remotely run arbitrary code on your machine. This is aakinskin to complete takeover since once they can run local code then dropping other malware, elevating privileges, and all that comes with that is rather trivial. RCEs are rarer and rare these days so it’s interesting that they were able to get here.
- As of now Zoom has not patched this vulnerability. So people know that it’s a series of vulnerabilities to get RCE, Zoom is aware of the vulnerability, and they have 90 days before the vulnerability is released by the researchers. So presumably the folks at Zoom will be quick to get a patch out for this. Right now I’m sure there are a dozen other researchers trying to figure out this exploit before Zoom can patch it.
- I absolutely love these events. This is what it’s all about. It’s an opportunity to get fresh sets of eyes on the software outside your teams, poke at them, find vulnerabilities, and make your software safer and more secure for everyone. Paying researchers good money leads to them not selling vulnerabilities on shady gray markets to governments and a safer Internet for everyone. Big fan and hope that more companies participate every year.
Threat Actors Rarely Cut Users Any Slack
- You know how cheesy action movies always seem to feature a bad guy (and it literally almost always is a guy) hiding in a laundry cart or jumping off a bridge into the bed of a farmer’s truck full of hay, to evade detection? That’s pretty much what you’ve got here, network-style. If you can ride along in network traffic that’s routine, then you don’t trigger alarms that are looking for traffic to unusual destinations, or using unusual modes.
- The user downloads the malware. That’s why it’s hard to detect as bad sometimes—you’ve got connections to a collaboration platform that the company has sanctioned and everyone’s using. So if the criminals are able to create an appealing lure, they get victims to download something that ends up causing harm. Often in the case of apps like Discord, the lures might be some kind of utility disguised as something related to gaming, since that’s a primary use of Discord. It’s social engineering, just like phishing. The CDN or content delivery network aspect of it is sort of incidental in the sense that it just means that a given hardcoded URL will serve as the termination point for the connection, and being on a CDN, that URL is a) almost always going to be an allowed destination, and b) is reachable from all over the world with good performance—low latency and high throughput. Not to mention resilience. So it makes for a darned fine way to distribute malware.
- If you can sneak out of prison in the laundry cart, you don’t have to construct some special getaway mechanism out of spoons and bubblegum and deflated footballs. You’re using existing infrastructure that’s always going to be there and available. The prison has to have some way to haul the laundry around. Online, if a malicious actor can use a popular service, one that almost no company is going to block outright, and which few are doing deep inspection on, for its command and control, then they don’t have to create their own infrastructure for that. We know that when purpose-built domains and IPs are used, they almost always get burned after a period of time. They get added to blocklists and detection rules and so forth, so there’s a cost to the actor in both time and money (though it’s probably usually stolen money, but still, that chips away at the Lambo payments, right?). If they’re using Discord or Twitter (which we’ve also seen) or Slack or other sanctioned tools for C2, they know that those aren’t going to get burned. It’s a bit harder to pull off, since there are always advantages to having full control over the assets you’ve deployed for C2, but if you can make it work, it’s got some serious advantages.
- Let’s start with Discord since we’re already picking on it. I mentioned those lures that pose as gaming utilities. Those are actually token stealers. If you can steal these tokens, which grant a user access into the Discord network, then you have the ability to stage further tooling for whatever it is you’re trying to carry out. Once you have an access token, you can use Discord webhooks to post pretty much anything you want into a channel, and it’s off to the races from there. Not surprisingly, one of the common infection types we see is—anyone want to take a guess? [pause for enthusiastic hand raising from Kelsey and Chad. “Pick me! Pick me!”] Right. Pay2Decrypt LEAKGAP is an example. Once it’s installed, we all know what happens next. (At least we hope we know what happens next: the company refuses to pay the ransom). By the way, even when they’re using CDNs like Discord for earlier stages, some of these ransomwares still are using attacker-owned DNS servers for final stage exfiltration and C2. DNS is another of those services that attackers love to ride along on since it always has to be available and it’s relatively easy to hide in all that DNS traffic.
- In some ways delivering maliciousness via collaborative tools has been with us for quite a while. So if you think of Twitter botnets, for example, you’re usually thinking of political influence or disinformation campaigns, and there certainly are plenty of those, but we’ve seen bot Twitter accounts used for C2 for years. The increase we’re seeing in these collaboration platforms being used for malware distribution corresponds, pretty predictably, with the rise in work from home during the pandemic. When Discord was primarily used for gaming or other non-work purposes, it wouldn’t represent such a useful mechanism for evildoers.
- The defenses for this have to be nuanced. A fundamental thing to begin with is that organizations, who are doing the right thing by trying to make collaboration as easy as possible, nonetheless have to make smart choices about which tools they support. There are tons of them out there, and of course you don’t want to just take a draconian approach and block them all, since that will [redacted] off your users and they’ll just find ways around your security. But if you work with users to find out what an acceptable, circumscribed set of tools is that everyone can live with, that’s a place to start. User education about this is still always a great idea. Like, if you’ve never said “please don’t download sketchy Discord gaming apps on your work computer,” it’s more likely that people will download sketchy Discord gaming apps to their work computers. From there, things get a little more complex since the traffic is all encrypted. There are security tools that do session termination and inspection of HTTPS traffic, and those might be worth a second look these days for companies that aren’t using them. (They can be a bit of a pain in the redacted to manage, but they can also be mighty useful). Basically we need to accept that this is happening and make some mitigation plans.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
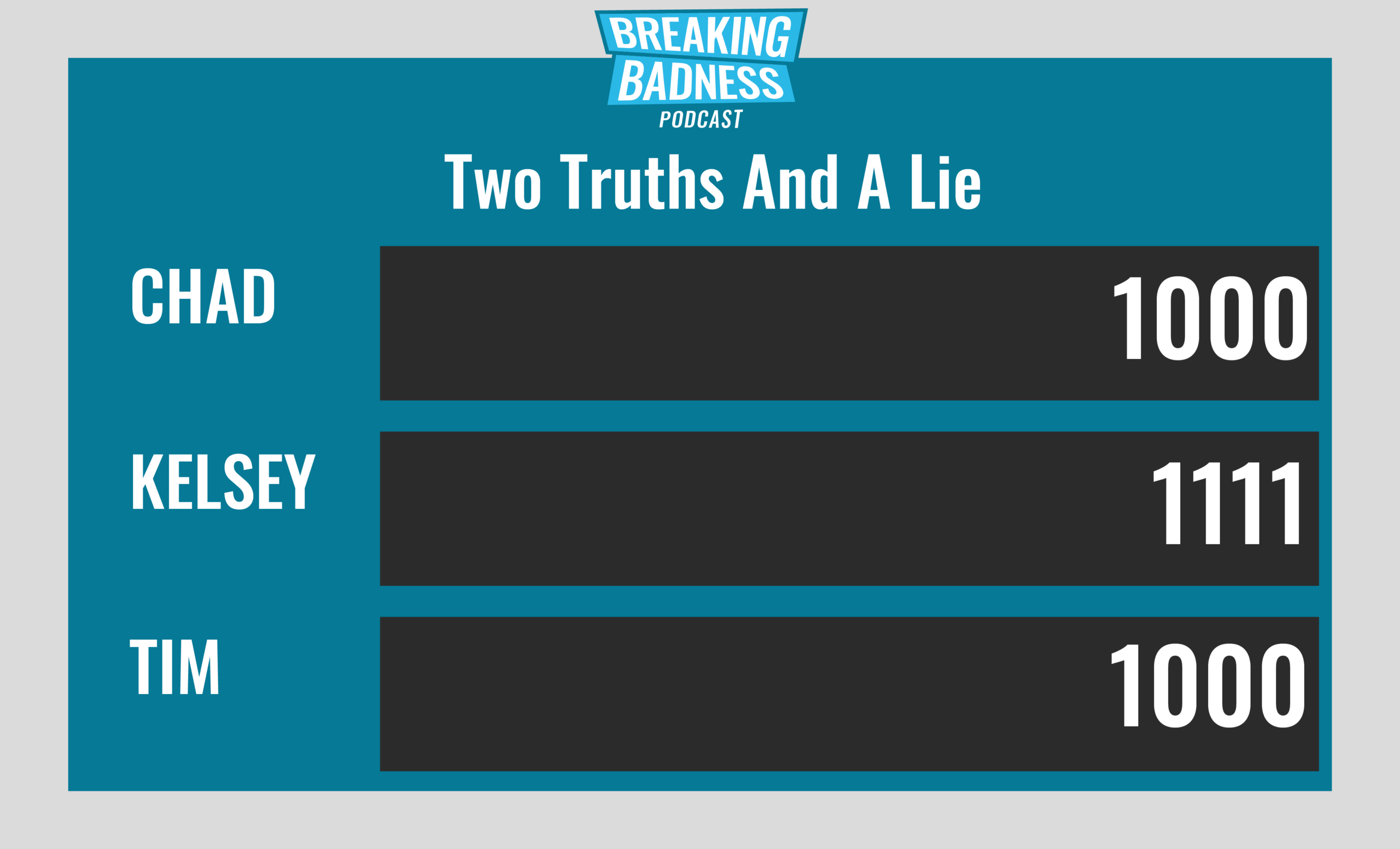
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Pwn2Own Goes According to LAN
[Chad]: 10/10 Should-ies
[Tim]: 6/10 Goodies
Threat Actors Rarely Cut Users Any Slack
[Chad]: 6/10 Hoodies
[Tim]: 6/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




